Over 1,400 CrushFTP servers uncovered on-line had been discovered weak to assaults at the moment concentrating on a important severity server-side template injection (SSTI) vulnerability beforehand exploited as a zero-day.
Whereas CrushFTP describes CVE-2024-4040 as a VFS sandbox escape in its managed file switch software program that allows arbitrary file studying, unauthenticated attackers can use it to realize distant code execution (RCE) on unpatched methods.
The corporate warned prospects on Friday to “update immediately” to dam attacker makes an attempt to flee the consumer’s digital file system (VFS) and obtain system information.
On Tuesday, Rapid7’s vulnerability analysis group confirmed the safety flaw’s severity, saying it was “fully unauthenticated and trivially exploitable.”
“Successful exploitation allows for not only arbitrary file read as root, but also authentication bypass for administrator account access and full remote code execution,” Rapid7 defined.
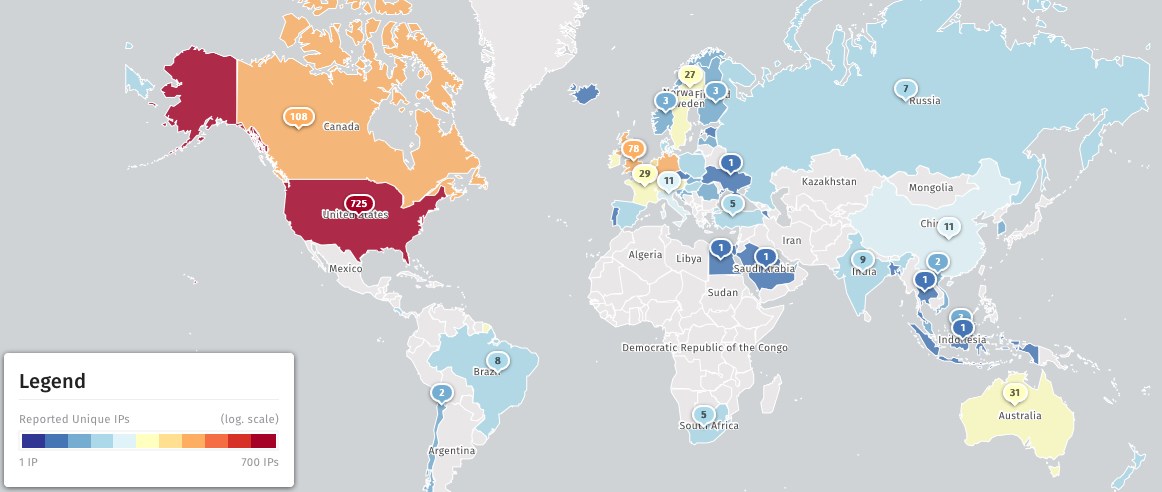
Safety researchers from the Shadowserver menace monitoring platform have found 1,401 CrushFTP unpatched cases left uncovered on-line, most of them in the US (725), Germany (115), and Canada (108).
Shodan additionally at the moment tracks 5,232 Web-exposed CrushFTP servers, though it would not present any info on what number of of them is likely to be weak to assaults.
Actively exploited in focused assaults
Cybersecurity firm CrowdStrike launched an intelligence report on Friday after CrushFTP disclosed the actively exploited zero-day and launched patches, revealing that attackers had been concentrating on CrushFTP servers at a number of U.S. organizations in what seemed like a politically motivated intelligence-gathering marketing campaign.
In response to proof discovered by Falcon OverWatch and Falcon Intelligence groups at CrowdStrike, CrushFTP zero-day was being exploited in focused assaults.
CrushFTP customers are suggested to recurrently examine the seller’s web site for the newest directions and prioritize patching to guard themselves towards ongoing exploitation makes an attempt.
CISA additionally added CVE-2024-4040 to its Recognized Exploited Vulnerabilities catalog on Wednesday, ordering that U.S. federal businesses ought to safe their weak servers inside per week, by Could 1st.
In November, CrushFTP prospects had been additionally warned to patch a important RCE vulnerability (CVE-2023-43177) after Converge safety researchers who found and reported the flaw revealed a proof-of-concept exploit.
