In Kubernetes, managing and analyzing community site visitors poses distinctive challenges as a result of ephemeral nature of containers and the layered abstraction of Kubernetes buildings like pods, deployments, and companies. Conventional instruments like Wireshark, though highly effective, wrestle to adapt to those complexities, typically capturing extreme, irrelevant knowledge – what we name “noise.”
The Problem with Conventional Packet Capturing
The ephemerality of containers is among the most blatant points. By the point a safety incident is detected and analyzed, the container concerned might now not exist. When a pod dies in Kubernetes, it’s designed to immediately recreate itself once more. When this occurs, it has new context, reminiscent of a brand new IP handle and pod title. As a place to begin, we have to look previous the static context of legacy methods and attempt to do forensics based mostly on Kubernetes abstractions reminiscent of community namespaces and repair names.
It’s value highlighting that there are some clear contextual limitations of Wireshark in cloud native. Instruments like Wireshark aren’t inherently conscious of Kubernetes abstractions. This disconnect makes it laborious to narrate community site visitors instantly again to particular pods or companies with out important handbook configuration and contextual stitching. Fortunately, we all know Falco has the context of Kubernetes within the Falco rule detection. Wireshark with Falco bridges the hole between uncooked community knowledge and the intelligence offered by the Kubernetes audit logs. We now have some related metadata from the Falco alert for the community seize.
Lastly, there’s the problem of information overload related to PCAP information. Conventional packet seize methods, reminiscent of these employed by AWS VPC Visitors Mirroring or GCP Visitors Mirroring, typically lead to huge quantities of information, most of which is irrelevant to the precise safety concern, making it tougher to isolate essential data shortly and effectively. Comparatively, choices like AWS VPC Circulation Logs or Azure’s try at Digital community faucet, though much less complicated, nonetheless incur important prices in knowledge switch/storage.
When’s the suitable time to start out a seize? How have you learnt when to finish it? Ought to it’s pre-filtered to cut back the file measurement, or ought to we seize every thing after which filter out noise within the Wireshark GUI? We’d have an answer to those issues that bypasses the complexities and prices of cloud companies.
Introducing a New Method with Falco Talon
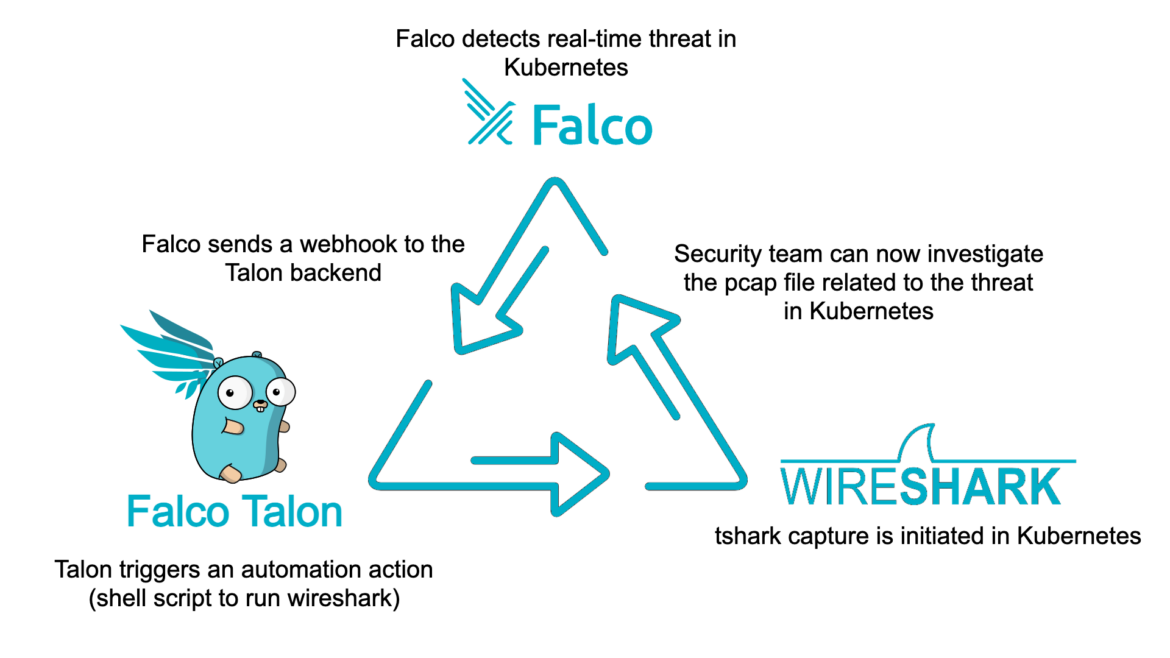
Organizations have lengthy handled safety blindspots associated to Kubernetes alerts. Falco and Falco Talon handle these shortcomings by means of a novel strategy that integrates Falco, a cloud-native detection engine, with tshark, the terminal model of Wireshark, for simpler and focused community site visitors evaluation in Kubernetes environments.
Falco Talon’s event-driven, API strategy to menace response is one of the simplest ways to take care of initiating captures in actual time. It’s additionally probably the most secure strategy we will see with the present state-of-the-art in cloud-native safety – notably, Falco.
Step-by-Step Workflow:
- Detection: Falco, designed particularly for cloud-native environments like Kubernetes, displays the setting for suspicious exercise and potential threats. It’s finely tuned to grasp Kubernetes context, making it adept at recognizing Indicators of Compromise (IoCs). Let’s say, for instance, it triggers a detection for particular anomalous community site visitors to a Command and Management (C2) server or botnet endpoints.
- Automating Tshark: Upon detection of an IoC, Falco sends a webhook to the Falco Talon backend. Talon has many no-code response actions, however certainly one of these actions permits customers to set off arbitrary scripts. This set off may be context-aware from the metadata related to the Falco alert, permitting for a tshark command to be mechanically initiated with metadata context particular to the incident.
- Contextual Packet Capturing: Lastly, a PCAP file is generated for a couple of seconds with extra tailor-made context. Within the occasion of a suspicious TCP site visitors alert from Falco, we will filter a tshark command for simply TCP exercise. Within the case of a suspicious botnet endpoint, let’s see all site visitors to that botnet endpoint. Falco Talon, in every of those eventualities, initiates a tshark seize tailor-made to the precise community context of the alert. This implies capturing site visitors solely from the related pod, service, or deployment implicated within the safety alert.
- Improved Evaluation: Lastly, the captured knowledge is straight away accessible for deeper evaluation, offering safety groups with the exact data wanted to reply successfully to the incident. That is worthwhile for Digital Forensics & Incident Response (DFIR) efforts, but in addition in sustaining regulatory compliance by logging context particular to safety incidents in manufacturing.
This focused strategy not solely reduces the quantity of captured knowledge, making evaluation quicker and extra environment friendly, but in addition ensures that captures are instantly related to the safety incidents detected, enhancing response occasions and effectiveness.
Collaboration and Contribution
We imagine this built-in strategy marks a big development in Kubernetes safety administration. In case you are all in favour of contributing to this modern venture or have insights to share, be happy to contribute to the Github venture at this time.
This technique aligns with the wants of contemporary Kubernetes environments, leveraging the strengths of each Falco and Wireshark to supply a nuanced, highly effective instrument for community safety. By adapting packet seize methods to the precise calls for of cloud-native architectures, we will considerably enhance our capability to safe and handle dynamic containerized functions.

Open supply software program (OSS) is the one strategy with the agility and broad attain to arrange the situations to satisfy trendy safety issues, well-demonstrated by Wireshark over its 25 years of improvement. Sysdig believes that collaboration brings collectively experience and scrutiny, and a broader vary of use instances, which in the end drives safer software program.
This proof-of-concept includes three OSS applied sciences (Falco, Falco Talon, and Wireshark). Whereas the situation was particular to Kubernetes, there is no such thing as a motive why it can’t be tailored to standalone Linux methods, Info of Issues (IoT) units, and Edge computing sooner or later.