After a CVE on open supply software program has been found and a repair has been launched, a fruitful apply for safety researchers is to go deep into the character of the CVE and the repair.
Along with curiosity, this good apply helps professionals and researchers prolong their data and enhance their understanding of safety vulnerabilities.
Being an engineer at Checkmarx, the primary device that involves thoughts to deep dive into the character of vulnerabilities is the Checkmarx Static Utility Safety Testing (SAST) engine.
This weblog put up will go into particulars concerning the nature of two separate vulnerabilities, CVE-2022-3602 and CVE-2022-3786, which hit the information at the start of November impacting a really well-known and largely adopted open supply software program bundle, OpenSSL. We’ll discover their repair and the way Checkmarx options can detect such susceptible code and assist builders with remediation.
CVE-2022-3602 and CVE-2022-3786
The official web page from OpenSSL, coping with November’s CVEs (CVE-2022-3786 and CVE-2022-3602) may be discovered right here.
The 2 vulnerabilities have an effect on OpenSSL as much as model 3.0.6, they usually contain a file named punycode.c, which is among the information that handle the parsing of particular encoding of domains (generally known as punycode).
With each vulnerabilities, “A buffer overrun can be triggered in X.509 certificate verification, specifically in name constraint checking”, they usually have been categorized as CWE-120 by NIST, as a “Classical Buffer Overflow.”
Buffer overflows
Typically, in C language, you will need to securely handle reminiscence buffers to keep away from any worth written in a buffer from being reused elsewhere within the code and being interpreted with sudden semantics. It’s value noting that in C, buffers embrace strings too!
Historically, strings are represented as a area of reminiscence containing knowledge terminated with a NULL character. Completely different string dealing with strategies might depend on this NULL character to find out the size of the string. If a buffer that doesn’t include a NULL terminator is handed to one in every of these capabilities, the perform will learn previous the tip of the buffer or will result in sudden behaviors, similar to buffer overflows.
Let’s undergo some technical particulars on the character of the 2 OpenSSL vulnerabilities.
CVE-2022-3602
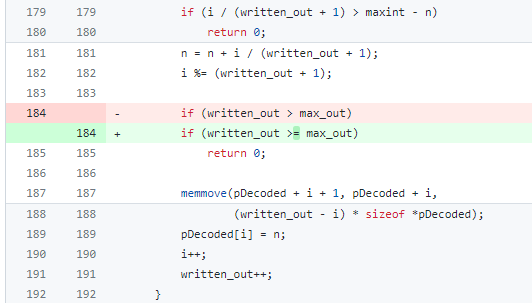
It’s a buffer overflow associated to the perform ossl_punycode_decode, the place there’s a test on the scale of a buffer for larger-than (>) values however omits the equals-to (=) values out of any test, as seen under.
The purple spotlight is the outdated model of the ossl_punycode_decode supply code (OpenSSL 3.0.6), whereas the inexperienced one is the mounted model (OpenSSL 3.0.7).
The test at line 184 was leaving the case “=” unchecked, letting knowledge with the identical dimension of max_out variable to succeed in the subsequent traces in this system and enter the additional a part of the perform.
The repair addresses such a case, by including the “=” case to those that have to be excluded with return 0.
Based on this proof, the buffer overflow is because of the absence of a correct test in opposition to the scale of a buffer which EQUALS the utmost, whereas there are circumstances outlined to handle sizes which can be bigger (return 0) and smaller (simply proceed).
Technically, this case is much like off-by-one vulnerabilities, the place an utility doesn’t correctly handle buffers that are precisely the scale of the utmost anticipated, as a consequence of a number of assumptions on the info buildings acquired in enter.
Numerous assumptions may be executed on knowledge buildings acquired in enter, they usually all deal about trusting the supply of such enter, in time period of its content material, its format, and its dimension; to construct safe code, assumptions needs to be averted.
As a substitute, sanitization and validation strategies needs to be applied within the code: sanitization is the exercise of eradicating extraneous knowledge from a given enter, remodeling it into innocent knowledge, appropriate with enterprise guidelines and safety insurance policies (e.g. eradicating particular characters from a string earlier than utilizing it as a parameter in SQL); validation, however, is the exercise of checking the content material of a given enter and rejecting any enter that doesn’t adjust to utility’s constraints (e.g. rejecting any string that’s higher or equals to the scale of a reminiscence buffer).
Checkmarx’s Codebashing coaching platform gives a number of classes to show builders the right way to write safe code in C, addressing correct strategies to handle buildings similar to buffers, stacks, and heaps, which might help builders keep away from introducing vulnerabilities of their code, similar to CVE-2022-3602.
For instance, relating to off-by-one, Checkmarx’s gamified platform reveals the scholar part of susceptible code and its unwanted effects at runtime, each in reminiscence and interactively:
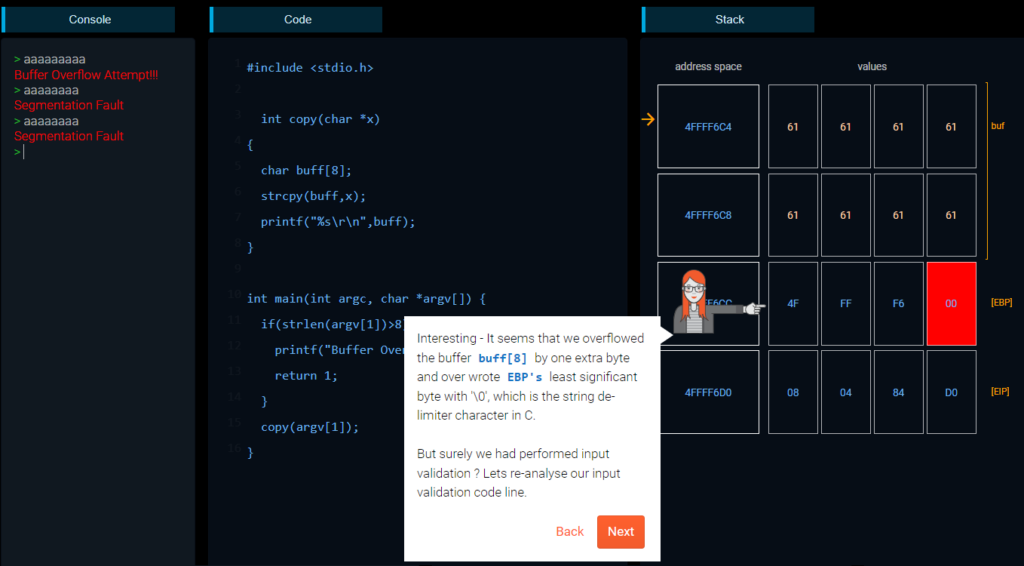
On this state of affairs, the susceptible code is strong when the buffer is bigger or smaller than the anticipated dimension; nonetheless, it’s not protected when precisely 8 characters are entered.
CVE-2022-3786
t is a buffer overflow associated to the perform ossl_punycode_decode, which manages a number of circumstances of writing characters (chars) to a buffer, earlier than utilizing that buffer in additional contexts, similar to studying it as a string.
OpenSSL 3.0.7 launched using this PUSHC macro, to handle operations in buffers correctly, as stacks:
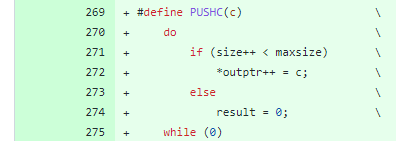
The macro is then used instead of outdated 3.0.6 “memcpy” capabilities, all over the place it’s wanted.
Just like the earlier instance above, the purple spotlight is the outdated model of the ossl_punycode_decode supply code (OpenSSL 3.0.6), whereas the inexperienced one is the mounted model (OpenSSL 3.0.7).
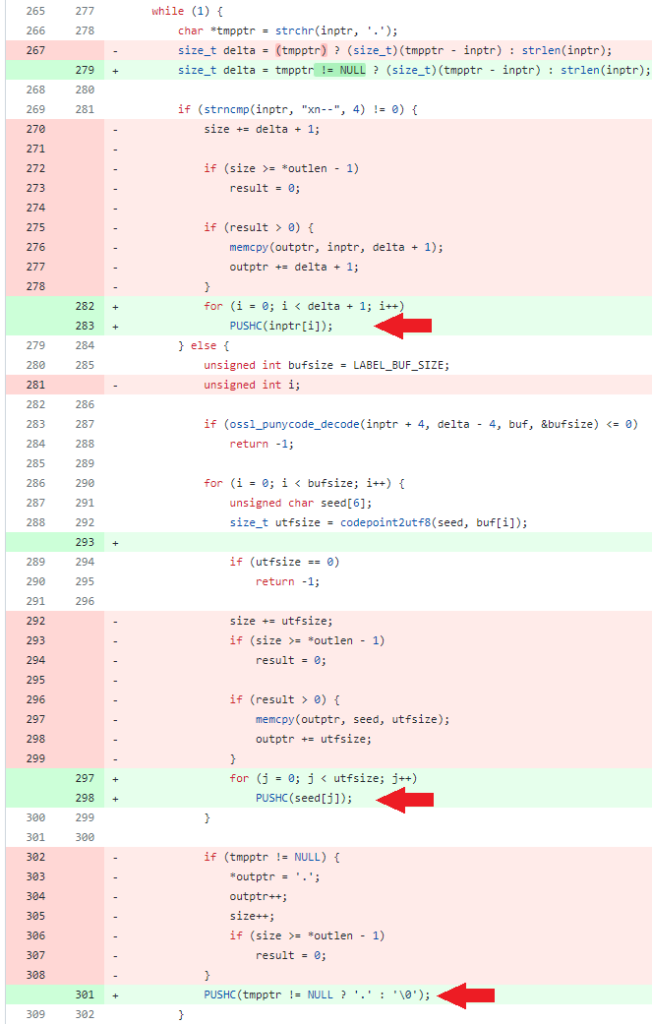
The change on line 301 manages the absence of the NULL character, which can result in sudden behaviors if the simply populated stack is utilized in different contexts (e.g., as a string!).
Checkmarx SAST has a selected question for C/C++ Language which known as “Improper_Null_Termination.” It’s within the class of Buffer Overflows, and it has Excessive severity.
Its purpose is to establish buffers that haven’t been correctly terminated by NULL characters.
By scanning OpenSSL 3.0.6 with Checkmarx SAST, the punycode file seems in two outcomes associated to line 276 and 297 for Improper Null Termination question:
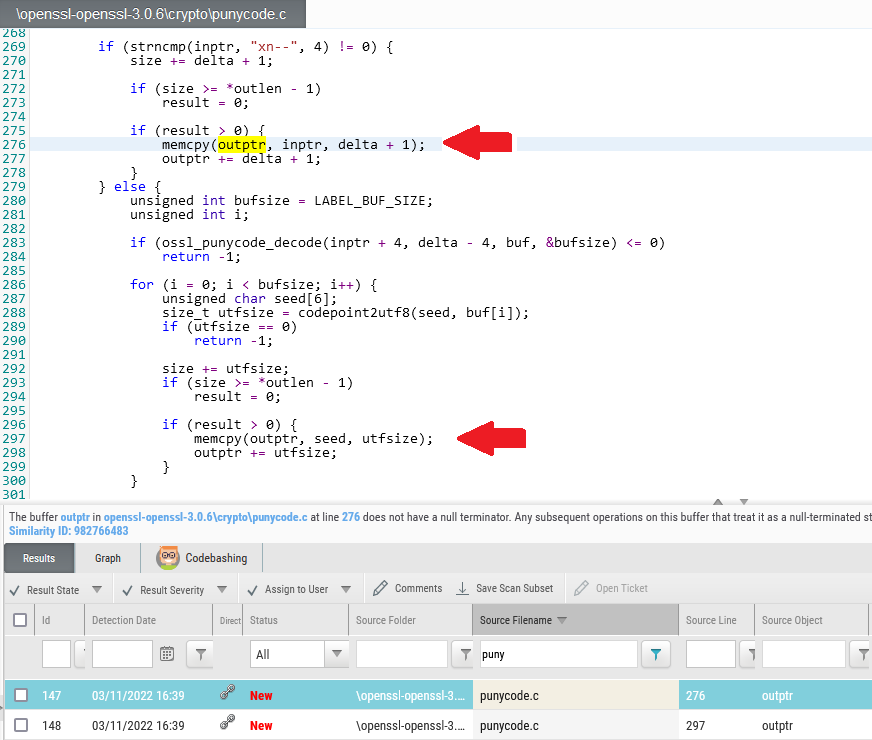
The outline of the discovering at line 276 states:
“The buffer outptr in openssl-openssl-3.0.6cryptopunycode.c at line 276 does not have a null terminator. Any subsequent operations on this buffer that treat it as a null-terminated string will result in unexpected or dangerous behavior.”
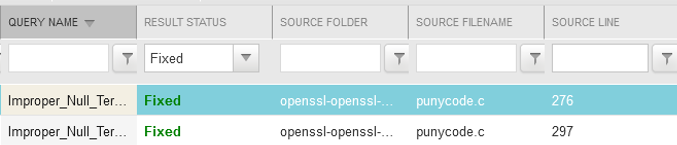
By scanning OpenSSL 3.0.7 with the identical preset, the 2 vulnerabilities seem as mounted:
Conclusion
Any utility might current vulnerabilities because of the massive dimension of functions, inheritances from older variations, errors, or errors. As evident with the not too long ago recognized OpenSSL vulnerabilities, even well-maintained and mature functions might current vulnerabilities that might be all however unattainable to be recognized by a handbook evaluate of the code.
On the identical time, the safety consciousness of builders is a key issue to supply and keep safe code.
Checkmarx SAST and Checkmarx Codebashing might help in elevating the bar of safety in your organization and in your builders and safety champions. Each options are absolutely built-in into our Checkmarx One™ Utility Safety Platform.
Study Extra
To be taught extra or see for your self, request a demo at the moment!