When investigating a possible assault on cloud companies, Daniel Bohannon often has to deal with the verbose logging of Amazon Internet Companies (AWS), an issue that may enable an attacker to cover in an avalanche of knowledge.
Whereas AWS sometimes produces solely a single occasion for each programmatic API name, accessing the administration console via the Internet results in an exponential improve in occasions, says Bohannon, a principal risk researcher with cloud identification service supplier Permiso Safety. In a single session, for instance, 81 clicks on customers, workloads, and roles resulted in 5,370 occasions recorded within the AWS log file.
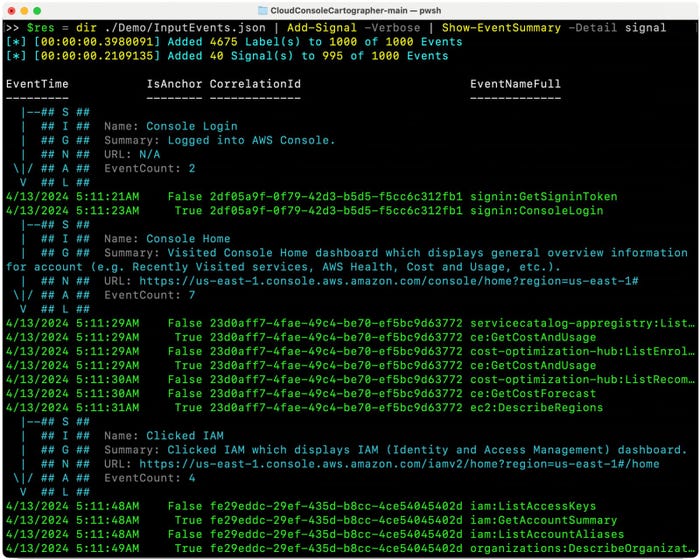
The sheer quantity of occasions leads to a lot noise that it turns into onerous to find out what a consumer is definitely doing within the AWS console, the risk researcher says. For that motive, Bohannon and fellow risk researcher Andi Ahmeti plan to launch an open supply software on the Black Hat Asia convention in Singapore to assist safety managers and incident responder consolidate cloud log occasions right into a document of consumer actions.
“The idea is that you input your raw logs — and we [show] 100% of those raw logs — but then we enrich the data on top of that, which … contains all the information about the events that led to those events,” he says. “We all have that full signal information, which … contains the summary, the labels, all that kind of stuff.”
Traditionally, the quantity of knowledge in log information have made it tough to find out the occasions that led as much as a compromise. Generally the issue is that the cloud service doesn’t log sufficient occasions to find out what occurs, comparable to final 12 months’s criticism that Google Cloud Platform (GCP) fails to log ample information when a consumer accesses a storage occasion.
In different instances, the particular ways in which cloud companies talk info to their clients can lead to an absence of visibility, particularly with the variations that corporations face with multicloud use. Greater than half of corporations have open ports undermining their safety and take some two months to shut the vulnerabilities.
AWS Produces Avalanche of Occasions
For companies utilizing AWS, the variety of occasions produced in a log whereas utilizing the Internet console may be vital. Simply clicking on a listing of customers produces 18 occasions for under three identities, and that is a light case of AWS’s verbosity, says Bohannon. A consumer who clicks within the AWS console to view the customers within the identification and entry administration (IAM) console will see greater than 300 occasions produced within the logs for CloudTrail, Amazon’s auditing functionality.
“That number can actually get as high as 100, 300, or even 700 events, depending on the settings you have in your Web browser — all just for one click,” he says. “So at a core level, every single action you take produces at least one event, but often it’s dozens or sometimes even hundreds of additional events associated with it.”
The researchers’ open supply software, Cloud Console Cartographer, goals to show the record of occasions captured by CloudTrail right into a succinct timeline of actions taken by the consumer. This system provides feedback to the cloud log that categorizes a sequence of captured occasions into alerts — precise consumer actions.
“We want to show all of our mapping to remove as much noise as we can but still keep all the raw events,” Bohannon says. “So anything that’s unmapped is great, it’s still evidence, and defenders can make the most sense of it.”
No Plans for Different Clouds
Cloud Console Cartographer, which shall be out there on GitHub, produces an enriched log of occasions and has a Internet interface that lists the alerts in a desk. At the moment, 240-plus guidelines for classifying collections of occasions into consumer actions — that’s, alerts — have been created that shall be used to counterpoint log information.
The 2 risk researchers intend to maintain engaged on increasing the variety of classifiers and hope that others will do the identical.
Bohannon and Ahmeti could transfer on to creating the software for different cloud platforms, however as a result of totally different cloud suppliers have alternative ways of logging, what works for AWS is not going to work for Microsoft Azure or Google Cloud Platform, they are saying. AWS is verbose, however Azure is the other — its logs are so terse as to be unhelpful, Bohannon says.
“I feel like every platform, every cloud platform has unique challenges that will have to be addressed in different ways,” he says. “So we might find in the future that we can integrate other cloud platforms into this, but [for now] we at least have plans for additional GUIs related to AWS that we are going to be working on after the initial release.”