Okta warns of an “unprecedented” spike in credential stuffing assaults concentrating on its id and entry administration options, with some buyer accounts breached within the assaults.
Menace actors use credential stuffing to compromise consumer accounts by making an attempt out in an automatic method lists of usernames and passwords usually bought from cybercriminals.
In an advisory at the moment, Okta says the assaults appear to originate from the identical infrastructure used within the brute-force and password-spraying assaults beforehand reported by Cisco Talos [1, 2].
In all assaults that Okta noticed the requests got here by the TOR anonymization community and numerous residential proxies (e.g. NSOCKS, Luminati, and DataImpulse).
Affect and suggestions
Okta says the noticed assaults had been notably profitable towards organizations operating on the Okta Traditional Engine with ThreatInsight configured in Audit-only mode somewhat than Log and Implement mode.
Likewise, organizations that don’t deny entry from anonymizing proxies additionally noticed a better assault success charge. The assaults had been profitable for a small proportion of shoppers Okta stated.
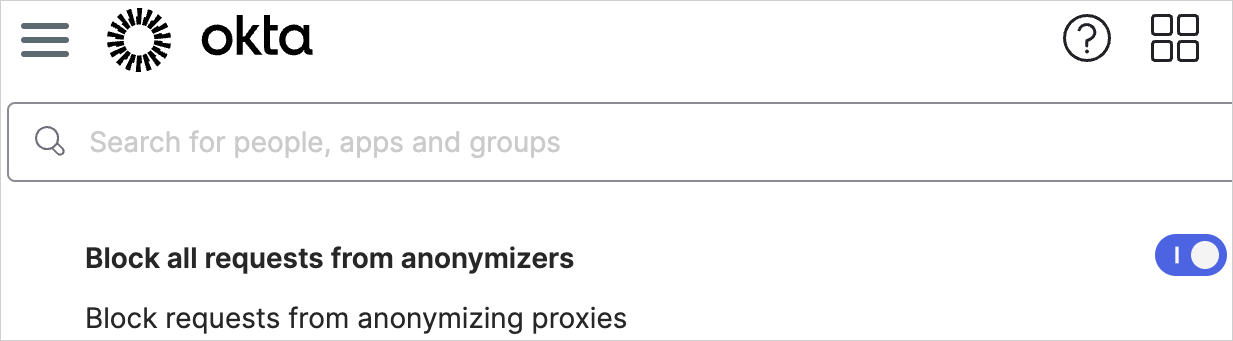
The corporate offers a set of actions that may block these assaults on the fringe of the community:
- allow ThreatInsight in Log and Implement Mode to dam IP addresses recognized for involvement in credential stuffing proactively earlier than they will even try authentication.
- deny entry from anonymizing proxies to proactively block requests that come by shady anonymizing providers.
Okta
- switching to Okta Identification Engine, which provides extra sturdy safety features, together with CAPTCHA challenges for dangerous sign-ins and passwordless authentication choices like Okta FastPass.
- implement Dynamic Zones which permits organizations to particularly block or permit sure IPs and handle entry based mostly on geolocation and different standards.
Okta additionally offers in its advisory a record of extra generic suggestions that may assist mitigate the danger of account takover. These embrace passwordless authentication, imposing multi-factor authentication, utilizing robust passwords, denying requests outdoors the corporate’s areas, blocking IP addresses of ailing reputation, monitor and reply to anomalous sign-ins.
BleepingComputer contacted Okta to study what this proportion was and the way clients had been impacted.
