In an alarming growth for the cryptocurrency group, the Ledger Join Package, has fallen sufferer to a classy provide chain assault, ensuing within the redirection of customers’ crypto transactions to a pockets managed by the attacker. The Ledger Join Package is a crucial part within the decentralized software ecosystem owned by Ledger – an organization that manages billions of {dollars}.
Key Findings
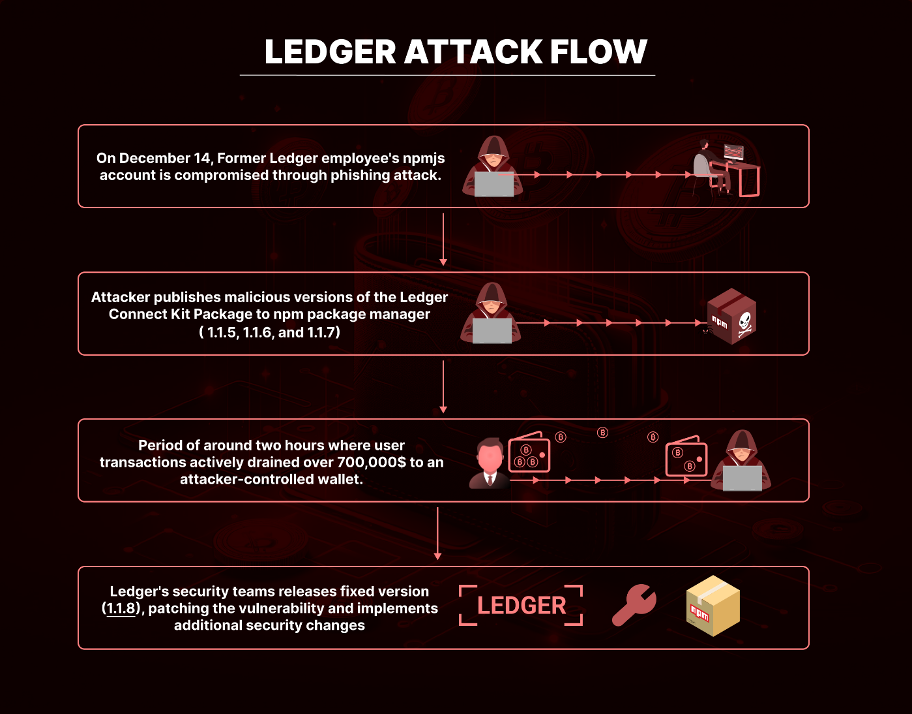
- NPM Account Takeover: Ledger Join-Package was compromised on account of npmjs account takeover of a former Ledger worker.
- Affected Variations: Malicious code was injected into variations 1.1.5, 1.1.6, and 1.1.7, leading to wallet-draining assaults.
- Impression: At the moment, over $700,000 has been stolen because of this safety breach.
- Fast Mitigation: Ledger swiftly launched model 1.1.8 to patch the vulnerability.
Assault Particulars
The Ledger Join Package, instrumental in linking customers’ wallets to decentralized functions (dApps), like SushiSwap and Revoke.money, was compromised when a risk actor took over the NPM account of one of many initiatives maintainers. The actor then continued to publish a number of new variations of the bundle, injected with malicious code, that drains the wallets of customers. Unsuspecting customers that carried out transactions unknowingly despatched their crypto funds to an attacker-controlled pockets.
The breach focused variations 1.1.5, 1.1.6, and 1.1.7 of the Ledger Join Package NPM Bundle. These variations have been contaminated with a malicious drainer, that diverted consumer funds to an attacker-controlled pockets. The compromised bundle used a rogue WalletConnect challenge to reroute funds.
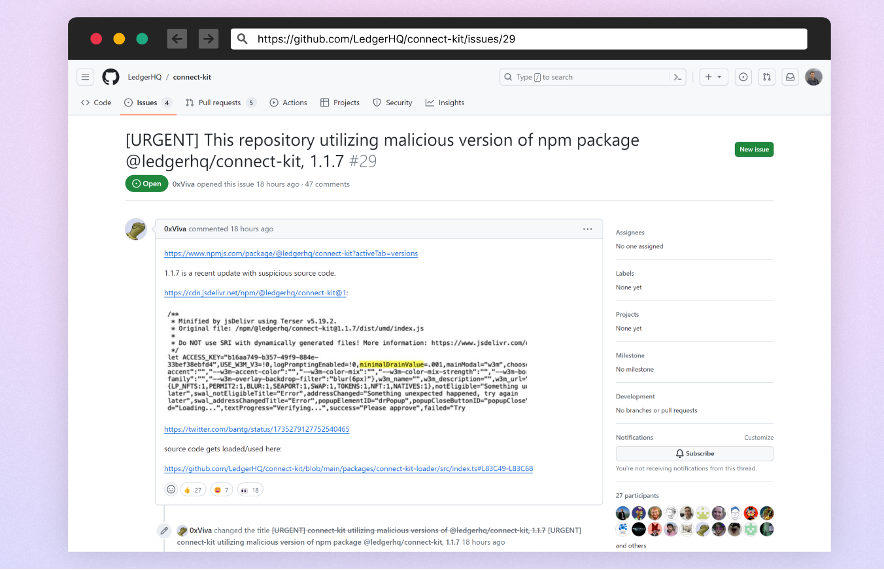
Notifying customers of the assault
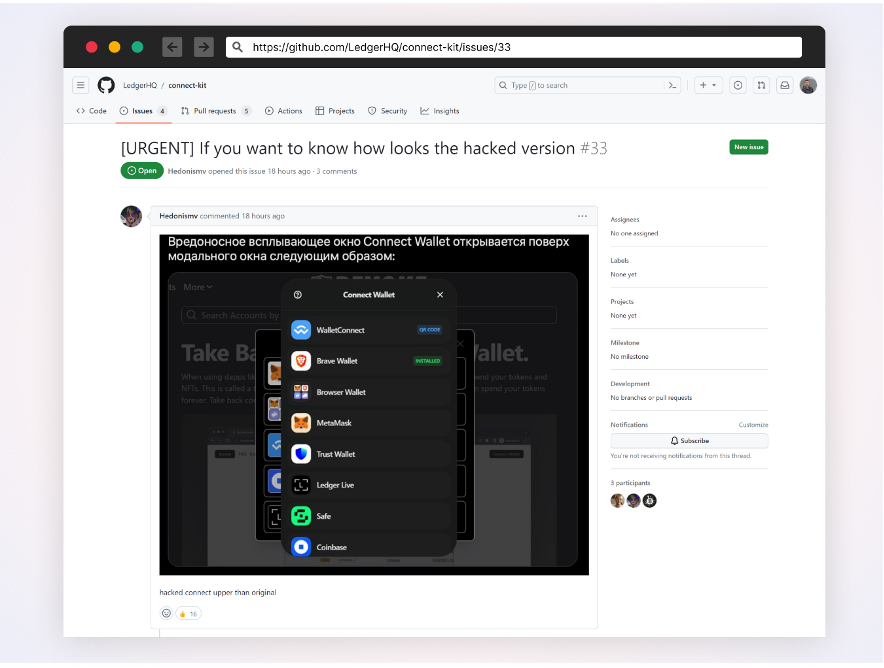
Notifying customers of the assault
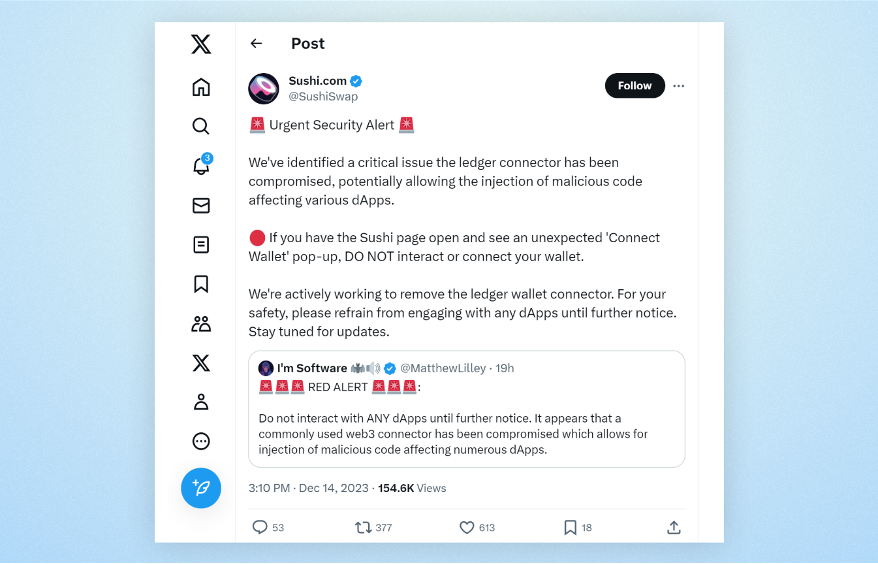
Apps affected, warning their customers
Tactic Used: Account Takeover
Central to this assault was a well-crafted social engineering technique that led to the compromise of a former Ledger worker’s npmjs account credentials. This breach then led to unauthorized releases of the Ledger Join Package. Account takeovers are significantly harmful since they permit attackers to bypass many conventional safety checks, immediately inserting malicious code into trusted software program. Phishing assaults in opposition to contributors have been a rising development for greater than a 12 months.
A vital, and infrequently missed, indicator of such an assault is the discrepancy in bundle variations between the bundle supervisor (npm) and the model management system (Git). We will clearly see on this assault that there have been no adjustments and no tags or releases on the Ledger git akin to the malicious variations on the NPM bundle supervisor.
When a challenge works effectively it maintains consistency between these platforms, with every npm launch akin to a Git tag. That is both finished robotically or manually. Nonetheless, on this case, the variations launched on npm lacked matching tags on Git. This mismatch serves as an indicator of suspicious exercise, significantly for initiatives recognized for his or her orderly launch processes as seen in earlier assault circumstances.
Monitoring for such inconsistencies is usually a essential a part of early detection methods for account takeovers and unauthorized bundle releases. Instruments and practices that hold monitor of this alignment can rapidly flag discrepancies, prompting an instantaneous investigation and doubtlessly stopping widespread impression.
Fast Response and Remediation
Upon discovering the breach, Ledger’s crew acted swiftly, releasing model 1.1.8 of the Ledger Join Package to patch the vulnerability inside 40 minutes of detection. Regardless of their fast response, the malicious variations have been energetic for about 5 hours, with a vital window of lower than two hours the place funds have been actively drained.
Impression
The monetary repercussions have gotten more and more obvious. As of the most recent experiences, over $700,000 has been stolen on account of this safety breach.
However I take advantage of SBOMs, so I am good – proper?
Whereas a Software program Invoice of Supplies (SBOM) is a vital instrument for enhancing transparency and safety in software program provide chains, its effectiveness is proscribed in sure forms of assaults. An SBOM successfully lists all parts utilized in a software program product, however it primarily addresses points associated to recognized vulnerabilities in these parts, not essentially the safety of the distribution mechanism itself.
Within the case of the Ledger Join Package assault, the first challenge was not with the parts themselves however with the compromised distribution course of on account of an account takeover. The attacker printed malicious variations of the bundle via a reputable channel, which might not essentially be flagged by an SBOM. Because the SBOM would listing parts as normal, it wouldn’t determine the malicious code launched by the attacker within the compromised variations.
So, whereas SBOMs are important for part transparency, they have to be complemented with quick, proactive scanning mechanisms that may detect unauthorized adjustments or malicious actions in real-time, past simply part itemizing.
Conclusion
This breach highlights the potential domino impact of a single compromised ingredient in interconnected digital platforms. The reliance on third-party parts, provides layers of vulnerability, making each participant within the chain a possible goal and contributor to a larger-scale compromise. Subsequently, it’s essential to make sure that efficient safety methods are in place which entails issues like rigorous vetting of third-party parts, implementing strong inner safety measures, and fostering a tradition of cybersecurity consciousness.
As a part of the Checkmarx Provide Chain Safety resolution, our analysis crew repeatedly displays suspicious actions within the open-source software program ecosystem. We monitor and flag “signals” which will point out foul play and promptly alert our clients to assist defend them.
Checkmarx clients are protected in opposition to this assault.