In November 2024, provide chain assaults featured two key traits: attackers’ persistent use of “legitimate-first” package deal methods and inventive approaches like exploiting official documentation. Cryptocurrency remained the first goal by means of each credential theft and mining operations.
Let’s delve into among the most putting occasions of November:
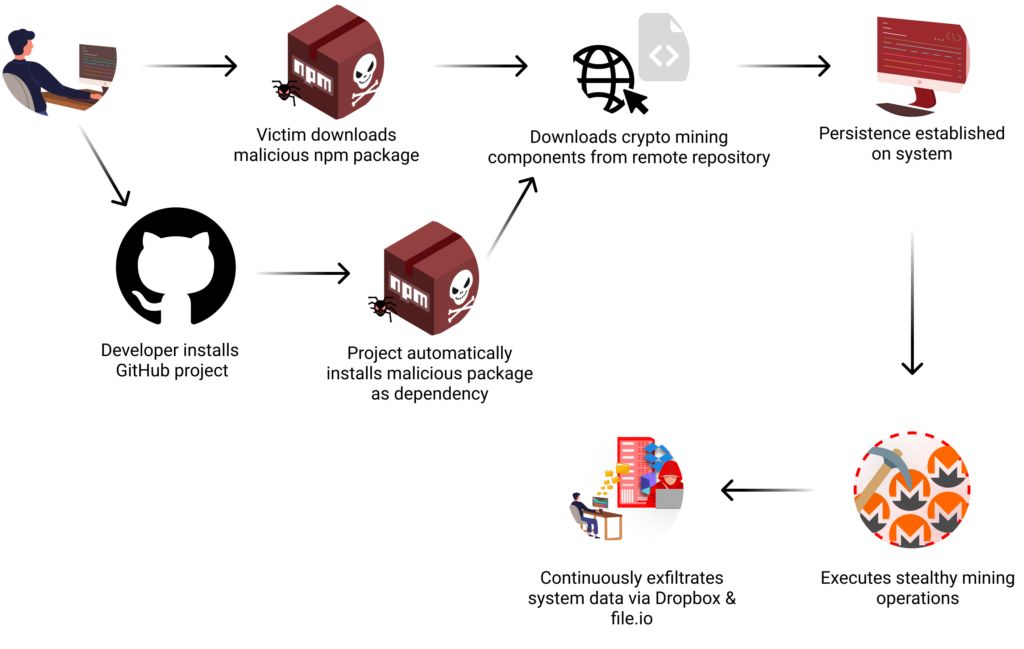
Dozens of Machines Contaminated: Yr-Lengthy NPM Provide Chain Assault Combines Crypto Mining and Information Theft
A malicious NPM package deal, masquerading as a professional XML-RPC implementation, operated for over a yr—stealing knowledge and mining cryptocurrency. Dozens of techniques have been affected. (Hyperlink to report).
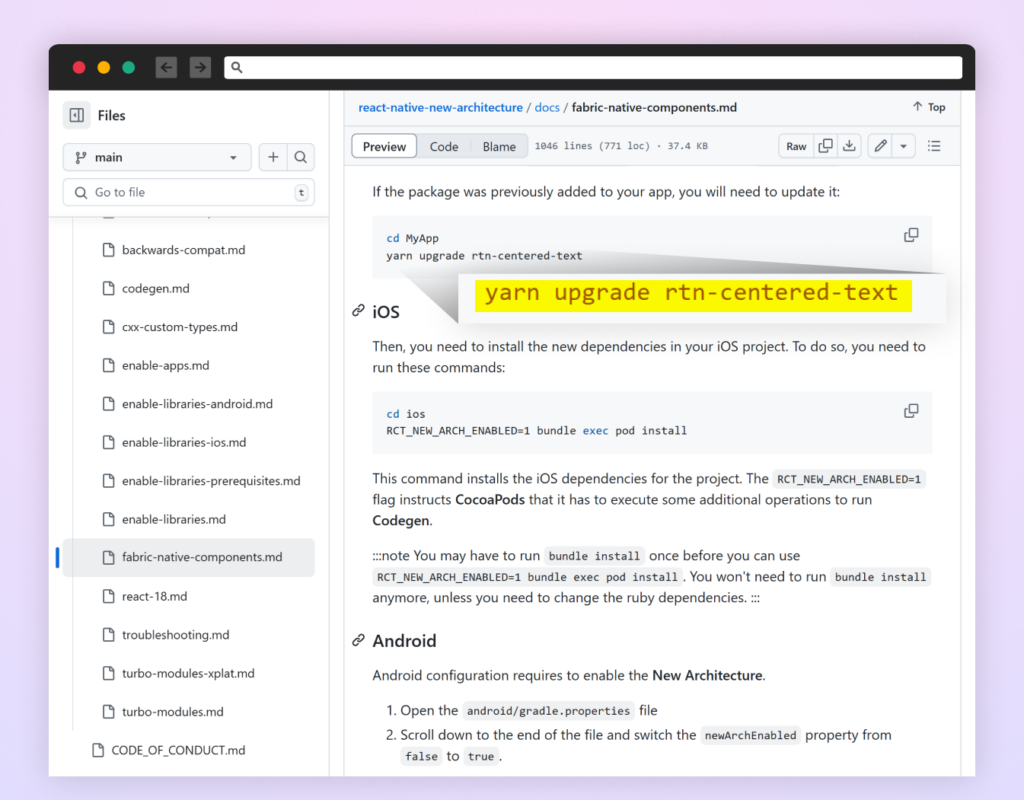
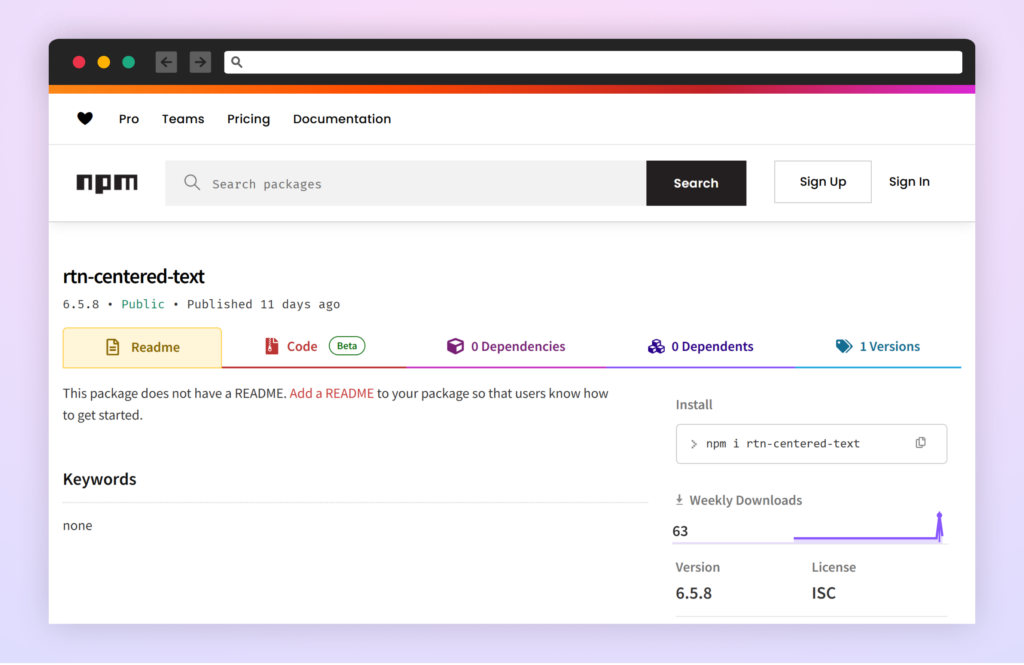
Malicious NPM Bundle Exploits React Native Documentation Instance
An attacker printed a malicious NPM package deal that mirrors an instance from React Native’s official documentation, in an try and trick builders following the official information. This highlights the necessity for cautious package deal verification even when following official guides. (Hyperlink to report).
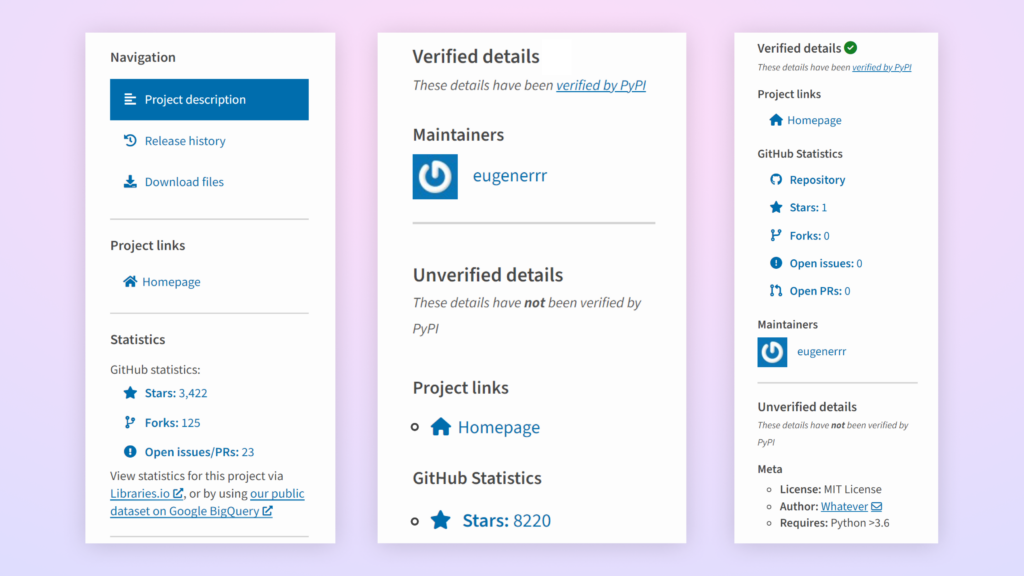
Falling Stars
Two years after the invention of StarJacking, an evaluation of 21 package deal repositories reveals improved safety measures towards this menace—although the chance nonetheless persists in some repositories. (Hyperlink to report).
“aiocpa” Python Bundle Transforms From Legit Bundle to Crypto Thief
In November 2024, PyPI printed an advisory in regards to the aiocpa package deal, which was compromised when variations 0.1.13 and 0.1.14 launched obfuscated malware designed to steal cryptocurrency credentials through Telegram. The assault was notable for its endurance – the attacker maintained a professional package deal for months earlier than including malware, whereas holding the GitHub repository clear. With hundreds of downloads in its closing month, aiocpa joins a rising pattern the place attackers set up professional packages earlier than weaponizing them, normally to focus on cryptocurrency property.
* * *
Our staff will proceed to hunt, squash assaults, and take away malicious packages in our effort to maintain the open-source ecosystem protected.
I encourage you to remain updated with the newest traits and ways in software program provide chain safety by tuning into our future posts and studying how one can defend towards potential threats.
Keep tuned…
Checkmarx Provide Chain Safety,
Working to Preserve the Open Supply Ecosystem Secure