North Korean state-sponsored menace group, Jumpy Pisces, collaborated with the Play ransomware group to hold out cyberattacks. Be taught concerning the instruments and strategies used, the impression of the assault, and methods to defend your group from comparable threats.
A latest incident response case by Palo Alto Networks Unit 42 sheds gentle on a regarding improvement– a collaboration between a North Korean state-sponsored group and a financially motivated ransomware gang.
Jumpy Pisces, also referred to as Onyx Sleet and Andariel (also referred to as the “Guardians of Peace” APT which was behind the notorious HBO information breach), has a historical past of cyberespionage, monetary crimes, and deploying custom-made ransomware like Maui. Unit 42’s investigation revealed a change in Jumpy Pisces’ ways, suggesting they might be more and more concerned in ransomware assaults.
The incident concerned an assault utilizing Play ransomware, a menace first recognized in mid-2022. Whereas the group behind Play, Fiddling Scorpius, is assumed to function beneath a Ransomware-as-a-Service (RaaS) mannequin, they’ve denied this on their leak web site.
The Assault
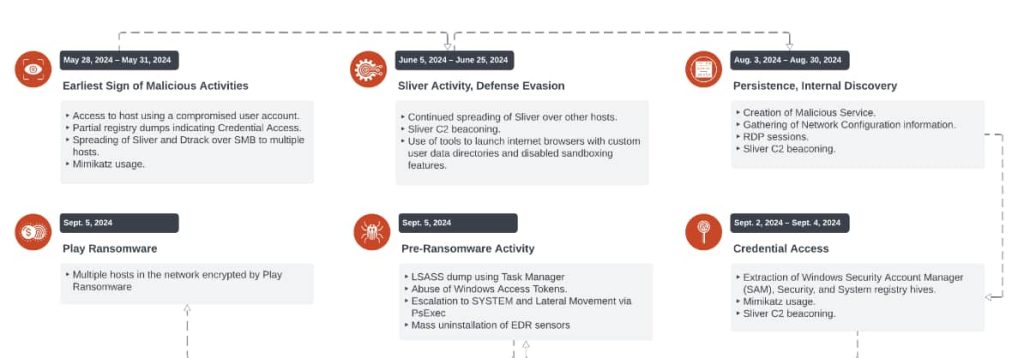
Unit 42’s investigation revealed a sequence of occasions that culminated within the deployment of Play ransomware. In Could 2024, Jumpy Pisces gained preliminary entry utilizing a compromised consumer account. Between Could and September 2024, they utilized instruments such because the open-source Sliver and their {custom} DTrack malware to maneuver laterally and keep persistence throughout the community.
In early September 2024, an unidentified actor accessed the community by means of the identical compromised account, seemingly constructing on Jumpy Pisces’ groundwork. This actor performed pre-ransomware actions, together with credential harvesting and EDR sensor elimination, earlier than deploying the Play ransomware later that month.
The custom-made model of the open-source Sliver C2 Framework enabled them to take care of persistent command and management (C2) communication, permitting distant command execution. The custom-built DTrack malware functioned as an infostealer, accumulating delicate data from affected methods and compressing it into disguised GIF information to keep away from detection.
In line with Palo Alto Networks Unit 42’s report, the attackers used PowerShell scripts to execute instructions, switch information, and work together with the system, whereas Mimikatz facilitated credential dumping by extracting plaintext passwords from reminiscence for extra account entry.
Researchers additionally famous using PsExec, a command-line device that permits the execution of processes on distant methods, supporting lateral motion and privilege escalation. Moreover, TokenPlayer, a device utilized in manipulating and abusing Home windows entry tokens, was utilized to steal tokens, enabling attackers to impersonate privileged customers.
Collaboration or Alternative?
Unit 42 believes that Jumpy Pisces collaborated with the Play ransomware group/Fiddling Scorpius on this assault as a result of the identical compromised account was utilized by each Jumpy Pisces and the Play ransomware actor. Jumpy Pisces ceased exercise simply earlier than the ransomware deployment, and TokenPlayer and PsExec, are generally seen in Play ransomware incidents.
Whether or not Jumpy Pisces acted as an official affiliate of Play ransomware or just bought community entry as an Preliminary Entry Dealer (IAB) stays unclear. Nevertheless, that is the primary documented occasion of such a collaboration, elevating issues concerning the potential for elevated participation of North Korean teams in ransomware campaigns because it poses a better menace to companies and organizations worldwide.
Erich Kron, a safety consciousness advocate at KnowBe4, famous that North Korea’s latest involvement in ransomware reveals strategic collaboration as a consequence of monetary motivations. Though North Korean actors are expert at community entry, their partnership with a longtime group is useful as they’re new to ransomware operations. Kron emphasised the necessity for organizations to concentrate on combating electronic mail phishing, given the heavy reliance of ransomware on social engineering.
RELATED TOPICS
- Faux North Korean IT Staff Infiltrate Western Companies
- Elite North Korean Hackers Breach Russian Missile Developer
- Iranian Hackers Workforce Up with Ransomware Gangs Towards US
- Russian Hackers Shift Techniques, Goal Victims with Paid Malware
- North Korean Hackers Deploy FASTCash Malware for ATM Cashouts