North Korean hackers goal Linux-based cost switches with new FASTCash malware, enabling ATM cashouts. Safe your monetary infrastructure and defend towards these refined assaults with skilled cybersecurity options.
A brand new variant of the FASTCash malware, beforehand recognized to focus on Home windows and AIX programs, has now been recognized focusing on Linux-based cost switches.
FASTCash, first documented by U.S. CISA in 2018, has been linked to a sequence of ATM cashout schemes focusing on banks in Africa and Asia since at the very least 2016, and has been developed by the infamous North Korean state-backed hacking group often called Lazarus (aka Hidden Cobra).
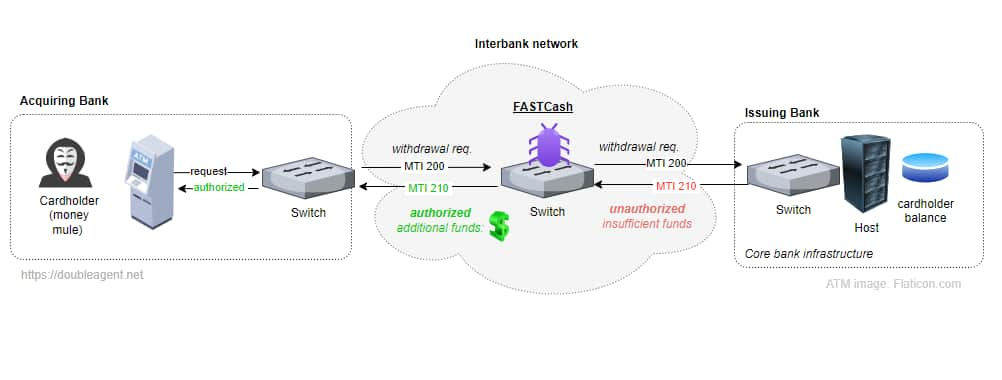
The malware operates by compromising cost change servers, that are essential parts of a financial institution’s infrastructure answerable for processing card transactions. These programs deal with the circulation of transaction knowledge between acquirers (the banks that allow retailers to simply accept funds), issuers (the banks that present playing cards), and card networks like Visa and Mastercard. By focusing on these cost change servers, the malware disrupts your complete transaction course of, making monetary establishments weak to fraud.
FASTCash for Linux makes use of Ubuntu Linux 22.04 (Focal Fossa), C++ programming language, AES-128 CBC encryption, and a hardcoded key to guard the configuration file.
A researcher, utilizing the deal with HaxRob, found two new samples of FASTCash for Linux switches in June 2023, one compiled for Ubuntu Linux 20.04 and sure developed after April 21, 2022, and the opposite probably not used. As of Sunday, solely 4 anti-malware engines detected every pattern.
HaxRob explains that the malware is current within the userspace of an interbank change. When a compromised card is used for fraudulent translation, FASTCash manipulates messages acquired from issuers, inflicting transaction messages for denies to be transformed to approvals.
The Linux variant of FASTCash is disguised as a shared object file named “libMyFc.so.” It particularly targets ISO 8583 messages – the usual format for communication inside cost networks, intercepting declined transaction messages, usually triggered by inadequate funds, for a predetermined record of cardholder accounts.
It then manipulates these messages, authorizing them for a random withdrawal quantity in Turkish Lira, starting from 12,000 to 30,000 Lira ($350 to $875). This modus operandi mirrors a Home windows variant of FASTCash recognized by the Cybersecurity and Infrastructure Safety Company (CISA) in September 2020.
For focused transactions, the malware modifies the authorization response message by:
- Eradicating particular knowledge components to keep away from detection.
- Overwriting the processing code to point approval.
- Including a random quantity of Turkish Lira to the transaction quantity.
This enlargement highlights the rising sophistication and persistence of North Korean cyberattacks geared toward monetary establishments and the necessity for enhanced safety measures in cost change programs.
Organizations ought to implement strong detection capabilities, often replace software program, configure safety controls, patch and replace programs, implement robust community safety, conduct common audits, and educate employees on phishing and social engineering dangers to remain protected.