North Korean menace actors goal Apple macOS methods utilizing trojanized Notepad apps and minesweeper video games created with Flutter, that are signed and notarized by a respectable Apple developer ID.
Because of this the malicious apps, even when briefly, handed Apple’s safety checks, so macOS methods deal with them as verified and permit them to execute with out restrictions.
The app names are centered round cryptocurrency themes, which aligns with North Korean hackers’ pursuits in monetary theft.
In line with Jamf Risk Labs, which found the exercise, the marketing campaign seems extra like an experiment on bypassing macOS safety than a fully-fledged and extremely focused operation.
Notarized apps connecting to DPRK servers
Beginning in November 2024, Jamf found a number of apps on VirusTotal that appeared fully innocuous to all AV scans but showcased “stage one” performance, connecting to servers related to North Korean actors.
All apps had been constructed for macOS utilizing Google’s Flutter framework, which permits builders to create natively compiled apps for various working methods utilizing a single codebase written within the Dart programming language.
“It is not unheard of for actors to embed malware within a Flutter based application, however, this is the first we’ve seen of this attacker using it to go after macOS devices,” defined Jamf researchers Ferdous Saljooki and Jaron Bradley.
This strategy not solely offers the malware authors versatility but in addition makes malicious code tougher to detect as a result of it is embedded inside a dynamic library (dylib), which is loaded by the Flutter engine at runtime.
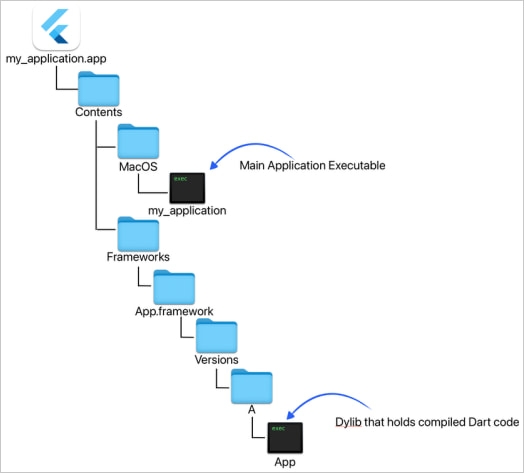
Supply: Jamf
Upon additional evaluation of one of many Flutter-based apps, named ‘New Updates in Crypto Alternate (2024-08-28).app’, Jamf found that the obfuscated code in dylib supported AppleScript execution, enabling it to execute scripts despatched from a command and management (C2) server.
The app opens a Minesweeper sport for macOS, the code of which is freely accessible on GitHub.
5 of the six malicious functions Jamf found had been signed utilizing a respectable developer ID, and the malware had handed notarization, which means the apps had been scanned by Apple’s automated methods and deemed protected.
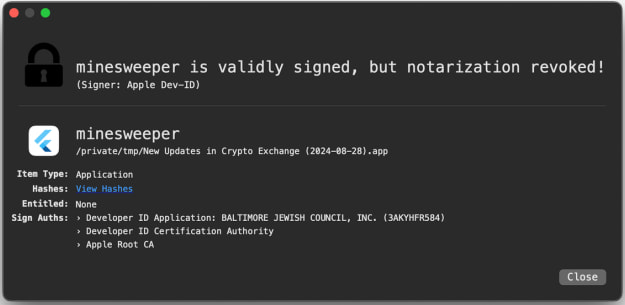
Supply: Jamf
Jamf additionally found Golang and Python-based variants, named ‘New Period for Stablecoins and DeFi, CeFi (Protected).app’ and ‘Runner.app,’ with the latter introduced as a easy Notepad app.
Each made community requests to a identified DPRK-linked area, ‘mbupdate.linkpc[.]internet,’ and featured script execution capabilities.
Apple has since revoked the signatures of the apps Jamf found, so they will not bypass Gatekeeper defenses in the event that they’re loaded on an up-to-date macOS system.
Nevertheless, it’s unclear if these apps had been ever utilized in precise operations or solely in “in-the-wild” testing to judge strategies to bypass safety software program.
The truth that there are a number of variants of the identical underlying apps helps this idea, however for now, the specifics of this operation stay unknown.
