Nokia’s investigation of latest claims of an information breach discovered that the supply code leaked on a hacker discussion board belongs to a 3rd get together and firm and buyer information has not been impacted.
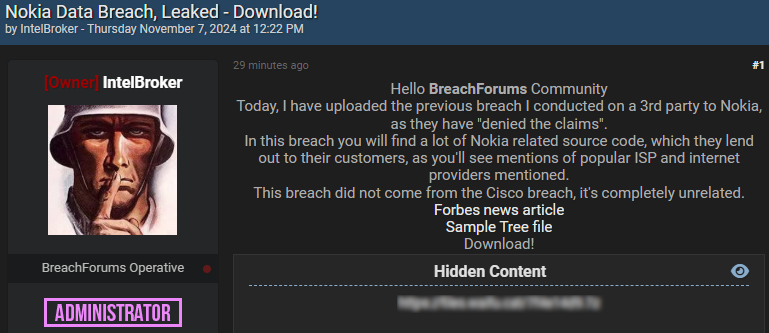
The assertion is available in response to risk actor IntelBroker earlier this week releasing information belonging to Nokia, allegedly stolen after breaching a third-party vendor’s server.
The hacker tried to promote the information, claiming that it consists of SSH keys, supply code, RSA keys, BitBucket logins, SMTP accounts, webhooks, and hardcoded credentials, however they determined to leak it after Nokia denied the breach.
Supply: BleepingComputer
BleepingComputer contacted Nokia for a remark in regards to the incident and an organization spokesperson mentioned that the investigation uncovered a third-party safety breach.
“Our investigation has found no evidence of any of our systems or data being impacted. Our investigations point to a 3rd party security incident, related to a single customized software application” – Nokia
IntelBroker beforehand informed BleepingComputer that they breached a third-party vendor through a poorly protected SonarQube server, which allowed the obtain of information of a number of massive corporations, Nokia amongst them.
“We have found no evidence that this 3rd party incident would in any way endanger critical Nokia systems or data, including source code, customized software, or encryption keys. Our customers are in no way impacted, including their data and networks,” the corporate informed BleepingComputer
The leaked supply code is for an software not developed by the corporate, however by a third-party. The app was constructed to perform solely in a single community, couldn’t perform exterior it, and doesn’t include any Nokia code.
Regardless of having discovered no danger to its programs or information, the Finnish multinational company says that it continues “to closely monitor the situation.”
