Cybersecurity researchers uncovered the “Xiū gǒu” phishing package concentrating on customers within the UK, US, Spain, Australia, and Japan. Lively throughout public, postal, and banking sectors, the package mimics legit companies to reap knowledge.
Cybersecurity researchers at Netcraft have found a brand new phishing package in motion named “Xiū gǒu,” which has been actively concentrating on unsuspecting customers within the UK, US, Spain, Australia, and Japan since September 2024.
This package, notable for its distinctive branding and interactive options, has been recognized in over 2,000 phishing web sites, exposing each people and organizations throughout completely different sectors to the chance of being compromised.
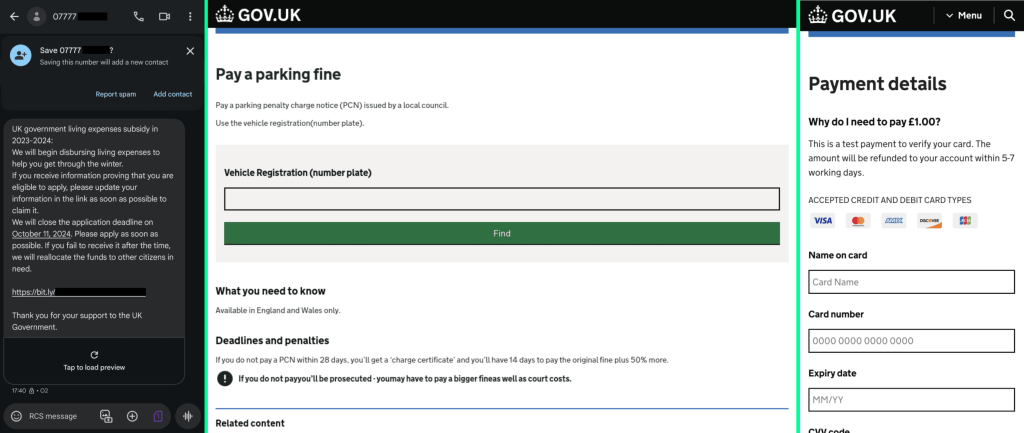
The phishing package, dubbed “Xiū gǒu” (修狗) after the Mandarin Chinese language web slang “xiū gǒu,” which interprets to “doggo,” at present focuses on scams associated to motorists, authorities funds, and postal companies. The admin panel and related Telegram account characteristic a cartoon canine mascot holding a soda bottle, including a component of leisure to the in any other case malicious instrument.
In accordance with the technical weblog submit shared with Hackread.com forward of publishing on Thursday, Xiū gǒu’s entrance finish makes use of Vue.js for each phishing pages and the admin panel, whereas the again finish is powered by Golang by way of the SynPhishServer executable. This mixture permits for a extra lively and harder-to-detect phishing infrastructure.
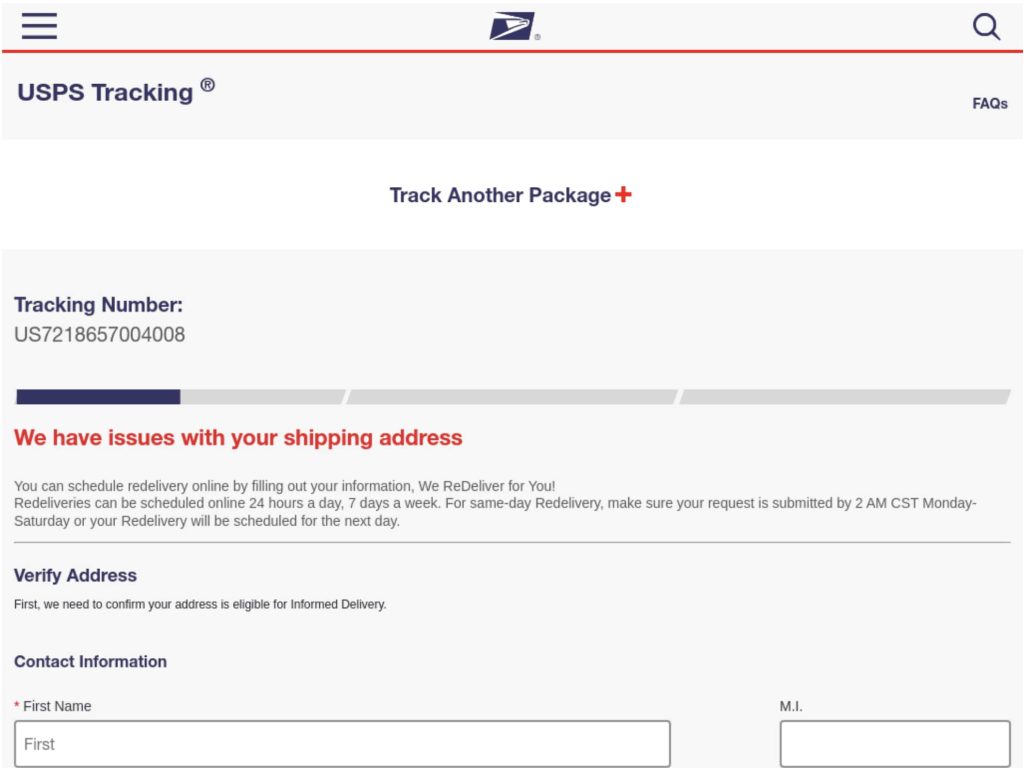
The package has been deployed throughout greater than 1,500 IP addresses and phishing domains, concentrating on victims with scams associated to motorists, authorities funds, and postal companies. Organizations within the public sector, postal, digital companies, and banking sectors have been significantly susceptible. A few of the notable impersonations embody the next:
- Evri
- Linkt
- USPS
- Lloyds
- Providers Australia
- New Zealand Submit
- UK Authorities (gov.uk and DVSA)
Menace actors utilizing Xiū gǒu leverage Cloudflare’s anti-bot and internet hosting obfuscation capabilities to evade detection. They typically register domains with the “.top” top-level area (TLD), selecting names that relate to their scams, comparable to ‘parking’ or ‘living,’ or incorporating components of the goal model’s identify.
The assault move usually begins with a Wealthy Communications Providers (RCS) message containing a shortened hyperlink, which directs victims to a phishing web site designed to imitate legit websites like gov.uk. Bots are redirected to non-malicious websites to additional obfuscate the exercise. As soon as victims enter their private and fee particulars, the data is exfiltrated to Telegram through a bot arrange by the fraudster.
Netcraft’s analysis supplies a window into the minds of the package’s authors stating, “Our analysis supplies an attention-grabbing perspective into the minds and strategies of the authors behind the kits and we are able to see by xiū gǒu’s use of particular scripting languages in addition to the inclusion of person tutorials.“
“The author has also chosen to measure and analyze the use of their kit, most likely so that they can optimize and improve their competitiveness over time. We also get a sense of how—as with the doggo mascot—authors inject personality and humour into their kits, leaving their own distinctive mark.”
The Xiū gǒu phishing package stays lively and is a part of an ongoing international marketing campaign concentrating on each companies and people. To guard your self, use warning with unsolicited messages and observe these steps to keep away from turning into its subsequent sufferer:
- Confirm Hyperlinks Earlier than Clicking: At all times hover over hyperlinks in emails or texts to test the precise URL, and keep away from clicking shortened hyperlinks until verified. Phishing kits typically use deceptive URLs to trick customers.
- Be Cautious with Private Info: Keep away from coming into delicate data on web sites reached by way of unsolicited messages, particularly if the positioning requests private or fee particulars.
- Allow Multi-Issue Authentication (MFA): MFA provides an additional layer of safety. Even when a phishing package collects your credentials, MFA may also help forestall unauthorized entry to your accounts.
- Use Anti-Phishing Software program: Many anti-phishing instruments can detect suspicious websites and forestall you from accessing them, even should you by chance click on on a phishing hyperlink.
- Educate Your self on Phishing Ways: Keep knowledgeable about widespread phishing methods and indicators, like uncommon language or suspicious domains, which may also help you determine threats earlier than they turn out to be points.
RELATED TOPICS
- EvilProxy Phishing Equipment Hits 100+ Corporations as It Bypasses MFA
- Chinese language ‘Smishing Triad’ Group Hits Pakistan with SMS Phishing
- V3B Phishing Equipment Steals Logins and OTPs from EU Banking Customers
- FishXProxy Phishing Equipment Makes Phishing Prepared for Script Kiddies
- EvilProxy Phishing Equipment Targets Microsoft Customers through Certainly.com Flaw
- Russian Hackers Make use of Telekopye Toolkit in Broad Phishing Assaults