A brand new Android backdoor malware named ‘Wpeeper’ has been noticed in no less than two unofficial app shops mimicking the Uptodown App Retailer, a preferred third-party app retailer for Android gadgets with over 220 million downloads.
Wpeeper stands out for its novel use of compromised WordPress websites to behave as relays for its precise command and management (C2) servers, appearing as an evasion mechanism.
The Android malware was found on April 18, 2024, by QAX’s XLab staff whereas inspecting a beforehand unknown ELF file embedded into APKs (Android package deal recordsdata), which had zero detections on Virus Complete.
The analysts report that the exercise ceased abruptly on April 22, presumably as a part of a strategic determination to take care of a low profile and evade detection by safety professionals and automatic programs.
Based mostly on Google and Passive DNS knowledge, XLab deduced that Wpeeper had already contaminated 1000’s of gadgets by the time of its discovery, however the precise scale of operations stays unknown.
Supply: XLab
Abusing WordPress as a C2
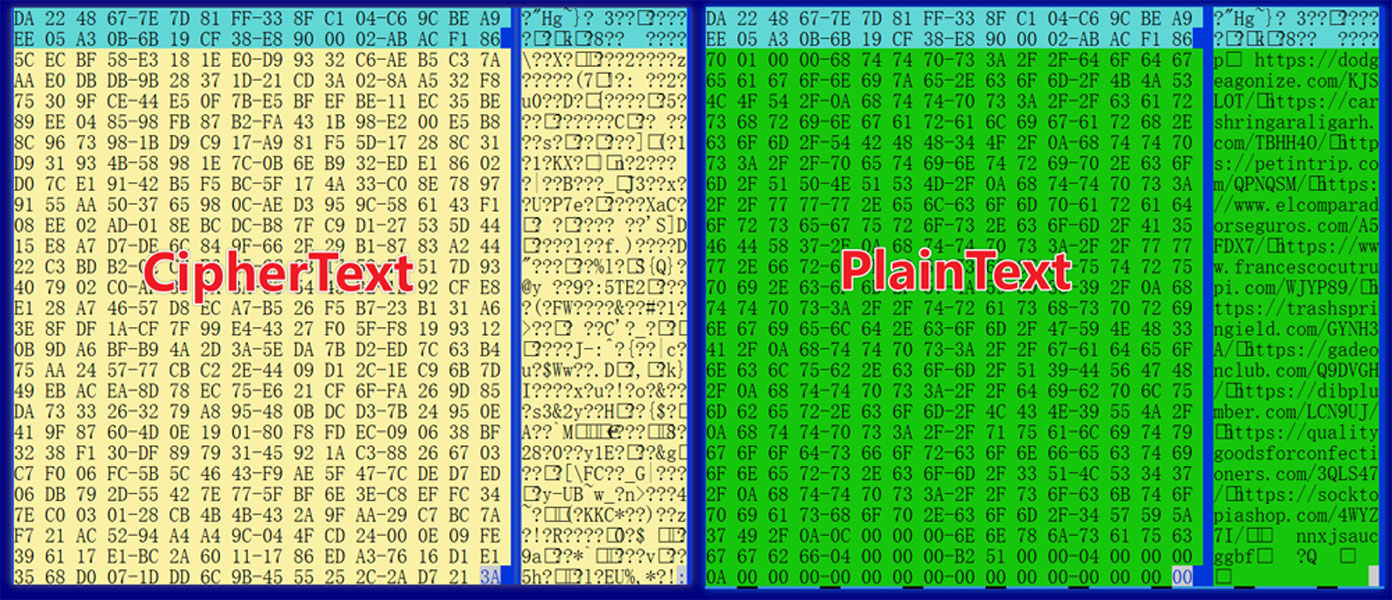
Wpeeper’s novel C2 communication system is structured to leverage compromised WordPress websites and intermediate relay factors, obscuring the situation and identification of its precise C2 servers.
Any instructions despatched from the C2 to the bots are forwarded through these websites, and they’re moreover AES encrypted and signed by an elliptic curve signature to stop takeover by unauthorized third events.
Supply: XLab
Wpeeper can replace its C2 servers dynamically via the reception of a associated command, so if a WordPress website is cleaned, new relaying factors on completely different websites could be despatched out to the botnet.
Utilizing a number of compromised websites throughout completely different hosts and areas provides resilience to the C2 mechanism, making it onerous to close down the operation and even disrupt the info trade on a single contaminated Android gadget.
Malware capabilities
Wpeeper’s main performance revolves round stealing knowledge, facilitated by its in depth set of instructions that includes 13 distinct capabilities.
The supported instructions within the backdoor malware are:
- Retrieve detailed details about the contaminated gadget, resembling {hardware} specs and working system particulars
- Collect an inventory of all put in purposes on the gadget
- Obtain new C2 server addresses to replace the bot’s record of command sources
- Modify the frequency of communication with the C2 server
- Obtain a brand new public key for verifying command signatures
- Obtain arbitrary recordsdata from the C2 server
- Retrieve details about particular recordsdata saved on the gadget
- Collect details about particular directories on the gadget
- Run instructions within the gadget’s shell
- Obtain a file and execute it
- Replace the malware and execute a file
- Delete the malware from the gadget
- Obtain a file from a specified URL and execute it
Because the operators of Wpeeper and the marketing campaign’s motives are unknown, it is not clear how the stolen knowledge is used, however potential dangers embrace account hijacking, community infiltration, intelligence assortment, identification theft, and monetary fraud.
To keep away from dangers like Wpeeper, it is strongly recommended that you simply solely set up purposes from Android’s official app retailer, Google Play, and be sure that the OS’s built-in anti-malware device, Play Shield, is lively in your gadget.
