A complicated malware known as Winos4.0 is being disguised as innocent gaming functions to infiltrate Home windows-based programs. Study concerning the multi-stage assault, information theft dangers, and tips on how to defend your self from this rising menace.
Cybersecurity researchers at Fortinet’s FortiGuard Labs have recognized a brand new malicious marketing campaign leveraging game-related functions to focus on Microsoft Home windows customers and ship Winos4.0, a brand new and superior malware framework much like Cobalt Strike and Sliver.
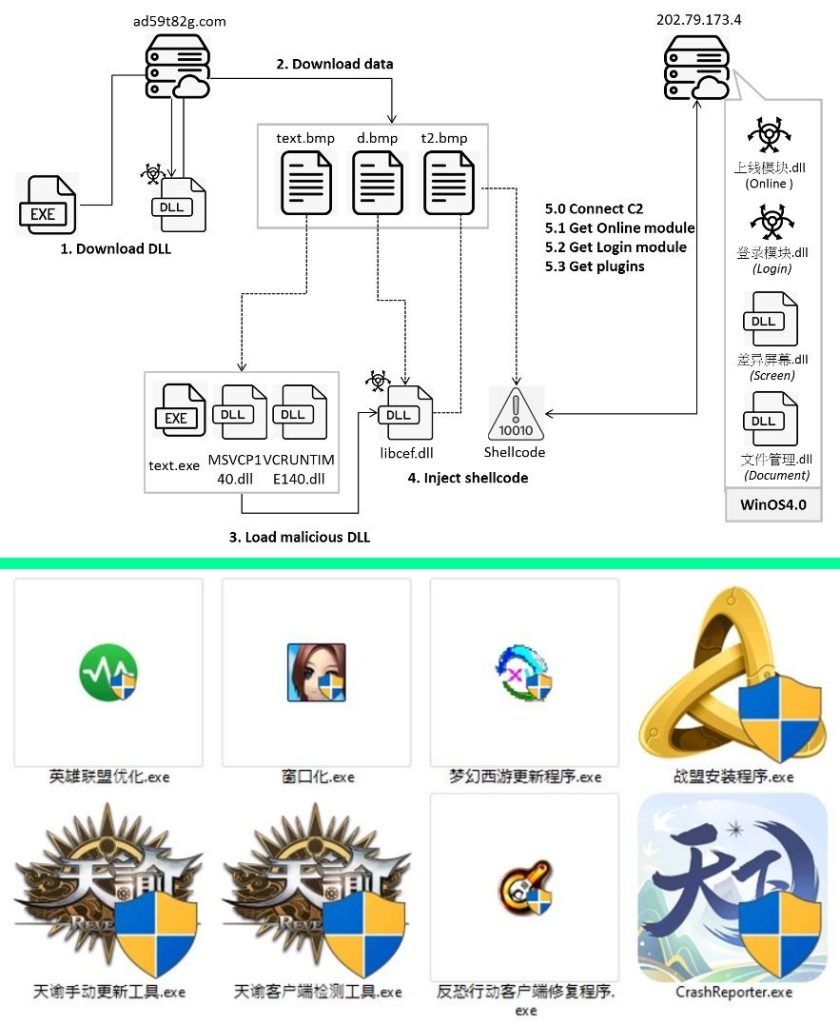
As soon as downloaded and executed, these apps act as Trojan horses, downloading and putting in the Winos4.0 framework.
The corporate’s findings shared with Hackread.com forward of publishing on Wednesday, Nov 6, recognized a number of samples of this malware hidden inside gaming-related functions, together with set up instruments, pace boosters, and optimization utilities. By analyzing the decoded DLL file, they discovered concerning the potential focusing on of the schooling sector, as indicated by its file description, “校园政务” (Campus Administration).
Winos4.0 framework provides complete performance, a secure structure, and environment friendly management over quite a few on-line endpoints. It’s rebuilt from Gh0stRat, a robust distant entry trojan created by the Chinese language hacking group C. Rufus Safety Workforce in 2008. Furthermore, it consists of a number of modular parts, every dealing with distinct capabilities. Given its capabilities, Winos4.0 has already been deployed in a number of assault campaigns like Silver Fox.
This multi-stage assault begins with retrieving a pretend BMP file from a distant server, which is then XOR-decoded, extracting a DLL file named “you.dll”. This file is loaded via its export operate “you” to proceed to the subsequent stage.
“You.dll” downloads three information from a distant path after making a folder with a random identify, extracts one to disclose clear information (u72kOdQ.exe, MSVCP140.dll, and VCRUNTIME140.dll), and one other to disclose the primary malicious file, “libcef.dll”. The extracted information then load “libcef.dll” to inject shellcode and decode one other file utilizing an XOR key.
The injected shellcode masses APIs and retrieves configuration information to ascertain a connection utilizing TCP protocol, sending a string to the C2 server, which responds with encrypted information. The information is decrypted utilizing XOR, and a module is executed. The module (上线模块.dll) downloads information from the C2 server and information its tackle within the registry, setting the stage for the assault’s remaining part.
The final stage launches the 登录模块.dll file, which performs duties like enabling crash restart, recording clipboard content material, checking window title bar for particular functions, amassing system info, checking for crypto pockets extensions, checking for anti-virus home equipment, sending login messages, and sustaining connection to its C2server with heartbeats.
The capabilities of Winos4.0 present that it’s a highly effective framework that can be utilized to simply management compromised programs. Researchers suggest that customers ought to concentrate on the supply of any new software and solely obtain software program from certified sources.
Due to this fact, chorus from downloading functions and software program from third-party app shops and web sites. Earlier than executing them, scan URLs and downloaded information on VirusTotal. Repeatedly scan your units, particularly after downloading new information. In workplace environments, block programs from downloading apps on workstations.
RELATED TOPICS
- Android Malware Poses as WhatsApp and Instagram to Steal Information
- TodoSwift Malware Targets macOS, Disguised as Bitcoin PDF App
- Octo2 Malware Makes use of Pretend NordVPN Apps to Infect Android Telephones
- SideWinder hackers hit Android customers with malware apps on Play Retailer
- New BingoMod Android Malware Posing as Safety Apps, Wipes Information