A never-before-seen Home windows malware named ‘Warmcookie’ is distributed by way of pretend job supply phishing campaigns to breach company networks.
In response to Elastic Safety Labs, which found the brand new menace, Warmcookie is able to intensive machine fingerprinting, screenshot capturing, and the deployment of further payloads.
The marketing campaign is at the moment underway, and the menace actors create new domains weekly to assist their malicious operations, utilizing compromised infrastructure to ship phishing emails.
Pretend job affords push malware
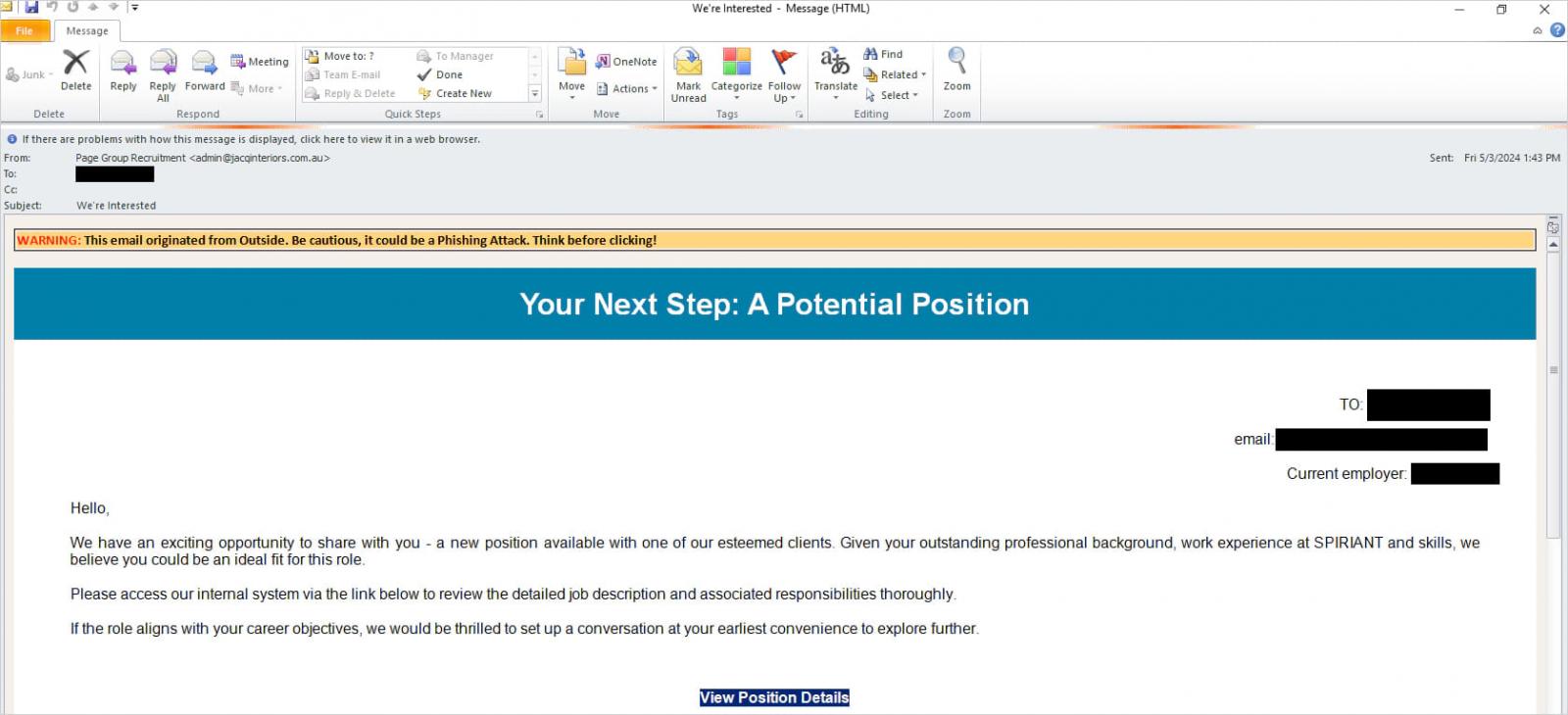
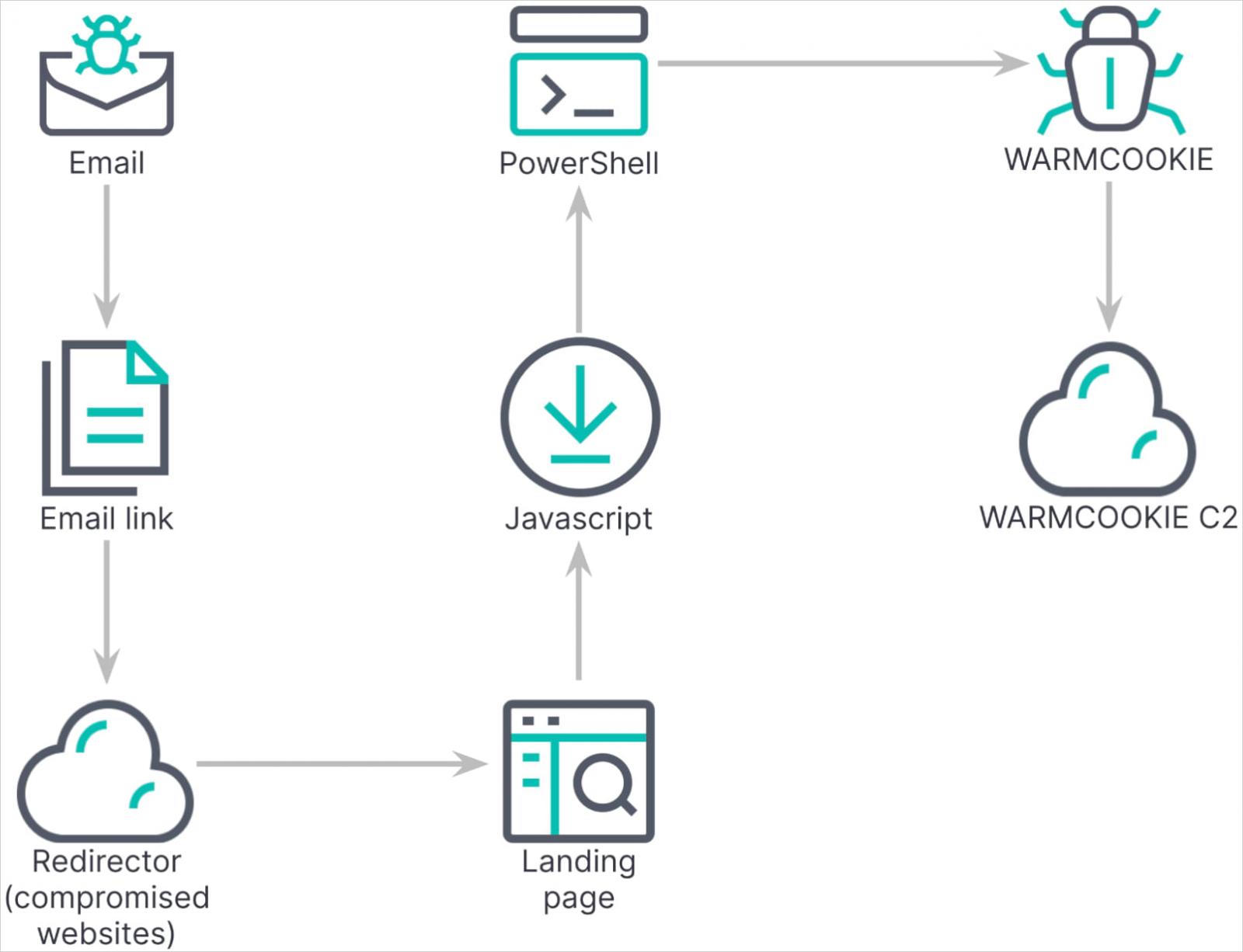
The phishing marketing campaign makes use of pretend job and recruitment affords despatched by way of emails with attention-grabbing topics. They aim people with touches of personalization, utilizing their names and people of their present employers.
Supply: Elastic
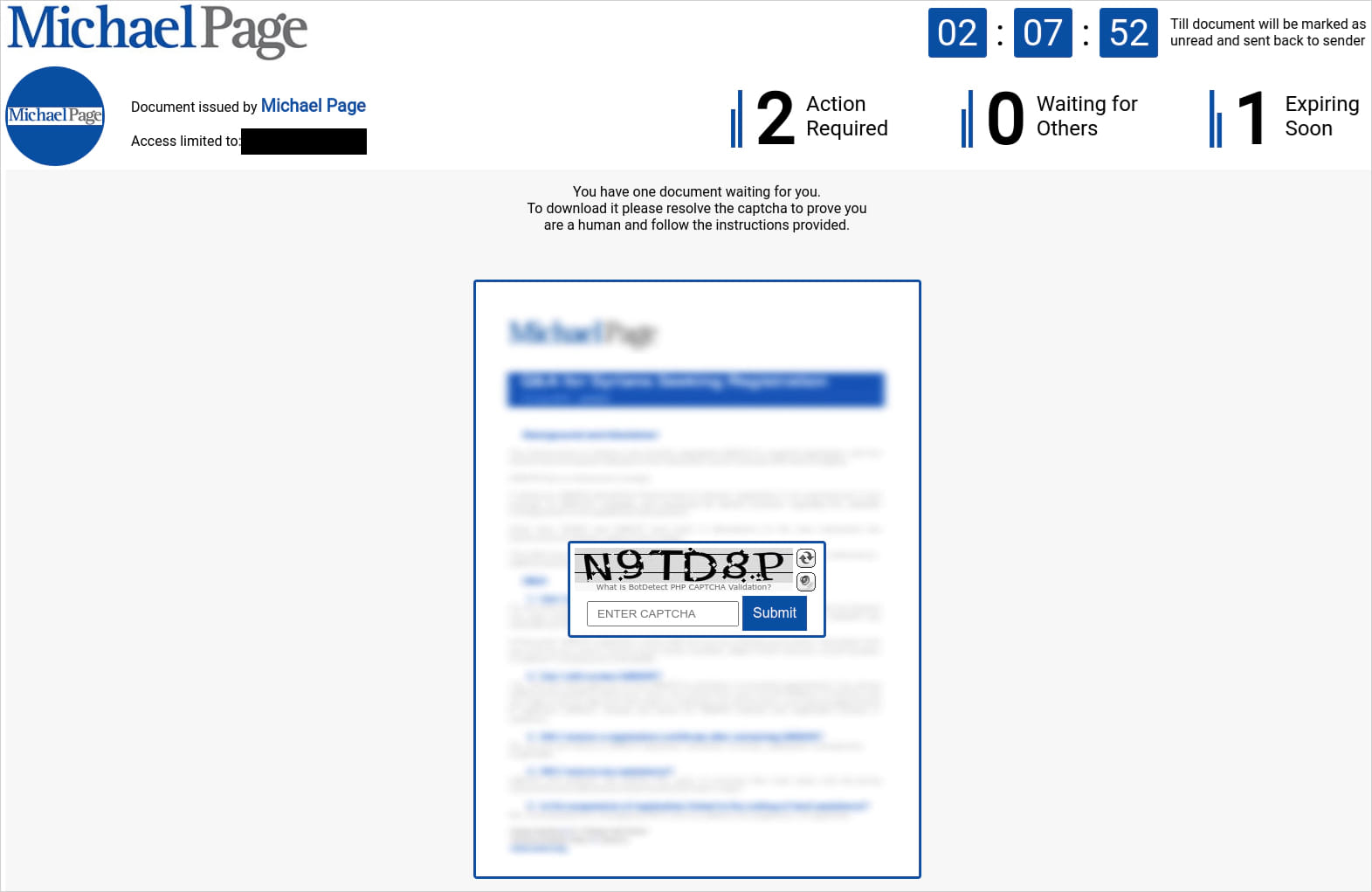
The emails comprise a hyperlink that claims to be for an inner recruitment platform the place the job description could be considered however redirects the person to touchdown pages mimicking respectable platforms.
Supply: Elastic
So as to add legitimacy, these pretend pages immediate the sufferer to resolve a CAPTCHA earlier than they obtain a closely obfuscated JavaScript file named much like ‘Update_23_04_2024_5689382’.
When executed, the JS script executes a PowerShell script that makes use of the Background Clever Switch Service (BITS) to obtain the Warmcookie DLL file from a specified URL and execute it by way of rundll32.exe.
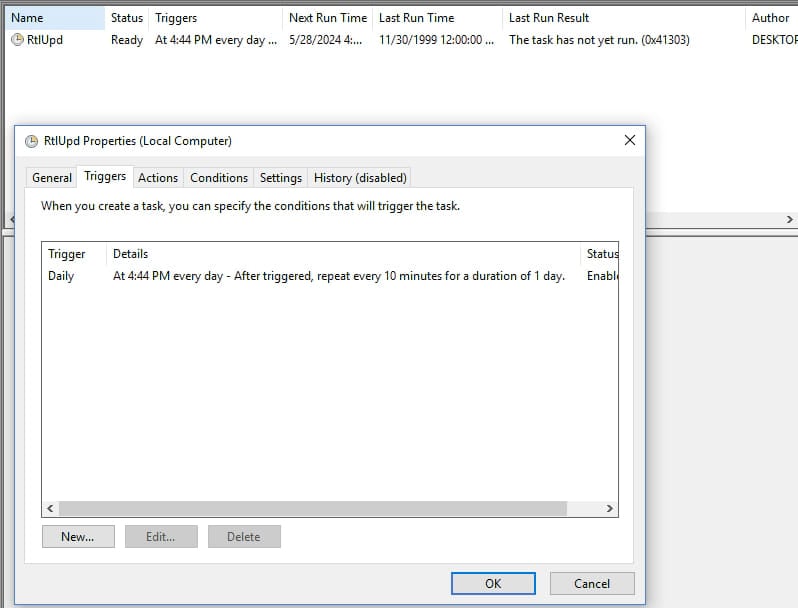
The Warmcookie payload is copied to C:ProgramDataRtlUpdRtlUpd.dll, and upon first execution, it creates a scheduled activity named ‘RtlUpd’ that runs each 10 minutes.
Supply: Elastic
Within the ultimate setup section, Warmcookie establishes communication with its command and management (C2) server and begins fingerprinting the sufferer’s machine.
Supply: Elastic
Warmcookie capabilities
Warmcookie is a backdoor malware with varied capabilities designed to infiltrate, persist, and collect intelligence from sufferer techniques.
Within the first stage of its operation, it collects key details about the contaminated host, together with quantity serial quantity, DNS area, pc identify, and username, after which encrypts and sends the information to the C2 by way of the HTTP cookie parameter.
Warmcookie’s fundamental capabilities are:
- Retrieve sufferer data comparable to IP deal with and CPU particulars
- Seize screenshots utilizing Home windows native instruments
- Enumerate put in applications by way of the registry key
- Execute arbitrary instructions utilizing ‘cmd.exe’ and ship output to the C2
- Drop recordsdata on specified directories/paths
- Learn the contents of specified recordsdata and ship content material to C2
Supply: Elastic
All acquired instructions are processed by way of an integrity examine utilizing CRC32 checksums to make sure they have not been tampered with.
Additionally, the malware will not run if the variety of CPU processors and bodily/digital reminiscence values are under sure thresholds to evade evaluation environments.
Elastic’s analysts remark that regardless of Warmcookie being a brand new backdoor with loads of room for enchancment, it’s already completely able to inflicting important injury to its targets, particularly given its functionality to introduce further payloads.
