Morphisec uncovers a brand new ValleyRAT malware variant with superior evasion techniques, multi-stage an infection chains, and novel supply strategies focusing on programs.
Cybersecurity researchers at Morphisec Menace Lab have found a brand new model of the delicate ValleyRAT malware distributed by numerous channels together with phishing emails, prompt messaging platforms and compromised web sites. ValleyRAT is a multi-stage malware, linked to the infamous Silver Fox APT group.
Based on Morphisec’s investigation, shared with Hackread.com, the important thing targets of this marketing campaign are high-value people inside organizations, particularly these in finance, accounting, and gross sales, and the target is to steal delicate knowledge.
Earlier ValleyRAT variations utilized PowerShell scripts disguised as respectable software program installers, which frequently employed DLL hijacking to inject their payload into signed executables from packages like WPS Workplace and even Firefox. In August 2024, Hackread.com reported a couple of ValleyRAT model utilizing shellcode to inject malware elements instantly into the reminiscence.
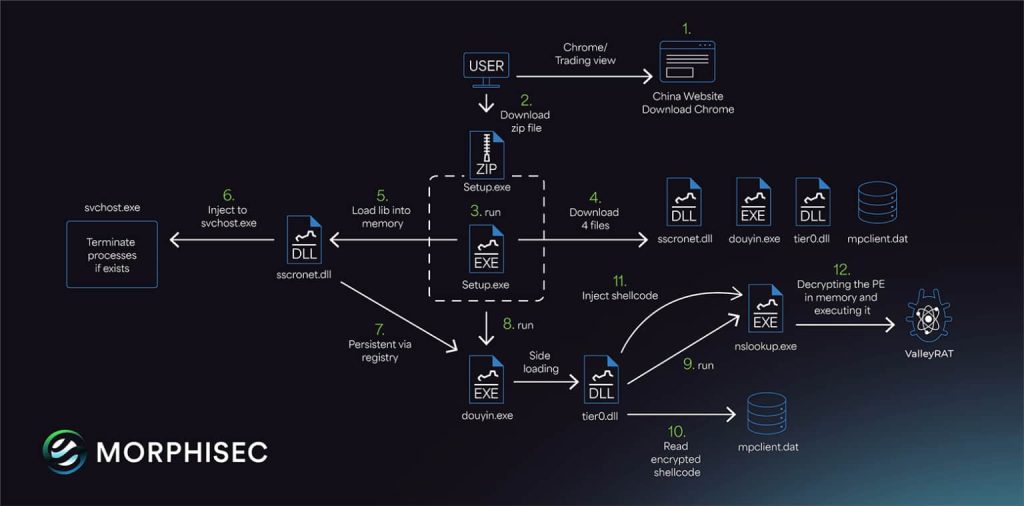
Conversely, the present model makes use of a pretend Chinese language telecom firm “Karlos” web site (karlostclub/) to distribute the malware, which downloads a collection of recordsdata, together with a .NET executable that checks for administrator privileges and downloads further elements, together with a DLL file.
“Interestingly, the actor reused the same URL for both the older and newer versions of their attack,” researchers wrote within the weblog submit.
Based on researchers, a pretend Chrome browser obtain from anizomcom/ is the preliminary an infection vector within the assault chain, tricking the sufferer into downloading and executing the malware. The sscronet.dll file, intentionally named with a legitimate-sounding identifier to keep away from suspicion, injects code into the respectable svchost.exe course of, performing as a monitor, terminating any processes on a predefined exclusion checklist to forestall interference with the malware’s operation.
Subsequent, the malware makes use of a modified model of the Douyin (Chinese language TikTok) executable for DLL side-loading and a respectable Tier0.dll from Valve video games (particularly Left 4 Lifeless 2 and Killing Ground 2) to execute code hidden inside the nslookup.exe course of. This course of retrieves and decrypts the primary ValleyRAT payload from mpclient.dat.
The decrypted payload makes use of the Donut shellcode to execute the malware in reminiscence, bypassing conventional disk-based detection strategies. It additionally tries to disable safety mechanisms like AMSI and ETW.
In your info, ValleyRAT is a C++-based distant entry trojan with primary RAT functionalities similar to accessing the WinSta0 window station for display, keyboard, and mouse interplay and monitoring the sufferer’s display. It incorporates intensive anti-VMware checks to evade detection in virtualized environments and connects with its C2 server utilizing IP addresses and ports which might be initialized inside its code throughout set up.
“If the malware does not detect that it is running inside a virtual machine (VM), it attempts to establish a connection to baidu.com as part of its network communication check,” researchers famous.
The Silver Fox APT group’s altering techniques/evasion methods present the rising sophistication of recent assaults. Organizations ought to undertake a correct safety technique, together with stricter endpoint safety, worker coaching, and steady monitoring, to mitigate dangers.