A complicated ValleyRAT marketing campaign is concentrating on Chinese language Home windows customers. Be taught in regards to the malware’s multi-stage assault, its means to evade detection, and the potential influence on compromised methods. Perceive the risk actor’s ways and the dangers posed to people and organizations.
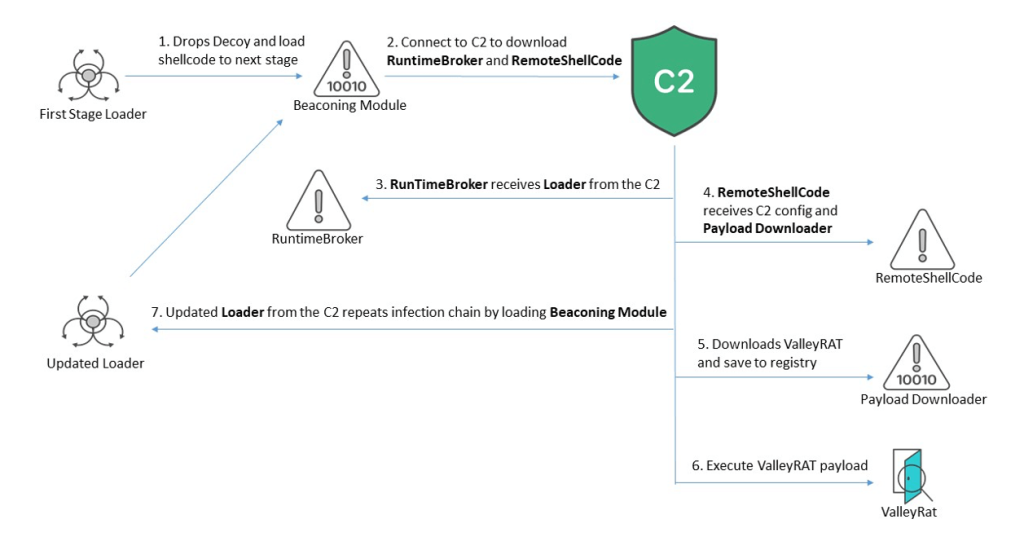
A brand new analysis report from FortiGuard Labs exposes a complicated marketing campaign particularly concentrating on Chinese language Home windows customers with ValleyRAT malware. It is a multi-stage malware concentrating on e-commerce, finance, gross sales, and administration enterprises.
Preliminary An infection:
The assault begins with a misleading lure, typically disguised as a legit doc associated to finance or enterprise, utilizing icons of legit purposes, like Microsoft Workplace. It creates an empty file and executes the default software for opening Microsoft Workplace Phrase paperwork.
If no default software is about, it shows an error message. As soon as executed, the malware establishes persistence on the system by making a mutex and modifying registry entries. It additionally makes an attempt to evade detection by checking for digital environments and using obfuscation strategies.
Payload Supply and Execution:
A key ingredient of this assault is using shellcode. This permits the malware to load its parts instantly into reminiscence, bypassing conventional file-based detection strategies. The malware then communicates with a command-and-control (C2) server to obtain further parts, together with the core ValleyRAT payload.
Based on FortiGuard Labs’ weblog submit shared with Hackread.com forward of publication on Thursday, ValleyRAT malware is attributed to the suspected APT group “Silver Fox.” It focuses on graphically monitoring person actions and delivering plugins and malware to the sufferer system.
Evasion Methods:
To extend its probabilities of success, the malware employs a number of evasion ways. These embrace disabling antivirus software program, modifying registry settings to hinder safety purposes, and utilizing sleep obfuscation to hinder evaluation, evade reminiscence scanners and encode its shellcode with an XOR operation.
Payload Capabilities:
The core ValleyRAT payload grants attackers in depth management over the compromised system. As soon as within the system, it helps instructions to watch actions and ship arbitrary plugins to additional the risk actors’ intentions.
Moreover, ValleyRAT screens person exercise, steals knowledge, and probably deploys further malicious payloads. It accomplishes this by means of a sequence of instructions, together with the potential to load plugins, seize screenshots, execute recordsdata, manipulate the registry, and management system capabilities like restarts, shutdowns, and logoffs.
The marketing campaign’s concentrating on of Chinese language customers is obvious in its use of Chinese language-language lures and its give attention to evading standard Chinese language antivirus merchandise. The malware’s persistence and skill to execute instructions remotely make it a big risk to affected methods.
That is an evolving marketing campaign. Hackread.com will replace readers relating to any new findings. In the meantime, customers are suggested to take care of up to date safety software program and train warning when opening surprising recordsdata or hyperlinks.
RELATED TOPICS
- Faux Sizzling Repair for CrowdStrike Spreads Remcos RAT
- TicTacToe Dropper Steals Knowledge from Home windows Units
- New Injector Drops XWorm, Remcos RAT in Multi-Stage Assault
- Multi-platform SysJoker backdoor Hits Home windows, macOS, Linux
- P2Pinfect Botnet Targets Servers with Ransomware, Cryptominer