Cybercriminals are exploiting Unicode QR codes in a brand new wave of phishing assaults. This subtle method bypasses conventional safety measures, making customers susceptible to malicious web sites and knowledge theft.
Cybercriminals are consistently innovating, and their newest trick includes QR codes. SlashNext has found a harmful new phishing method referred to as “Unicode QR Code Phishing” that bypasses conventional safety measures and calls for instant consideration.
QR codes have change into a standard a part of our digital lives, providing a fast and straightforward solution to entry data or web sites. Sadly, this comfort has additionally made them a goal for cybercriminals, as QR code phishing assaults have skyrocketed, making an attempt to lure victims out of safe e-mail environments and into susceptible cellular contexts the place safety is weaker.
Hackread reported a 587% surge in QR code phishing in early 2024 as Verify Level Software program Applied sciences recognized 20,000 cases of assaults throughout the first two weeks of 2024, highlighting the vulnerability of QR codes to cybercriminals.
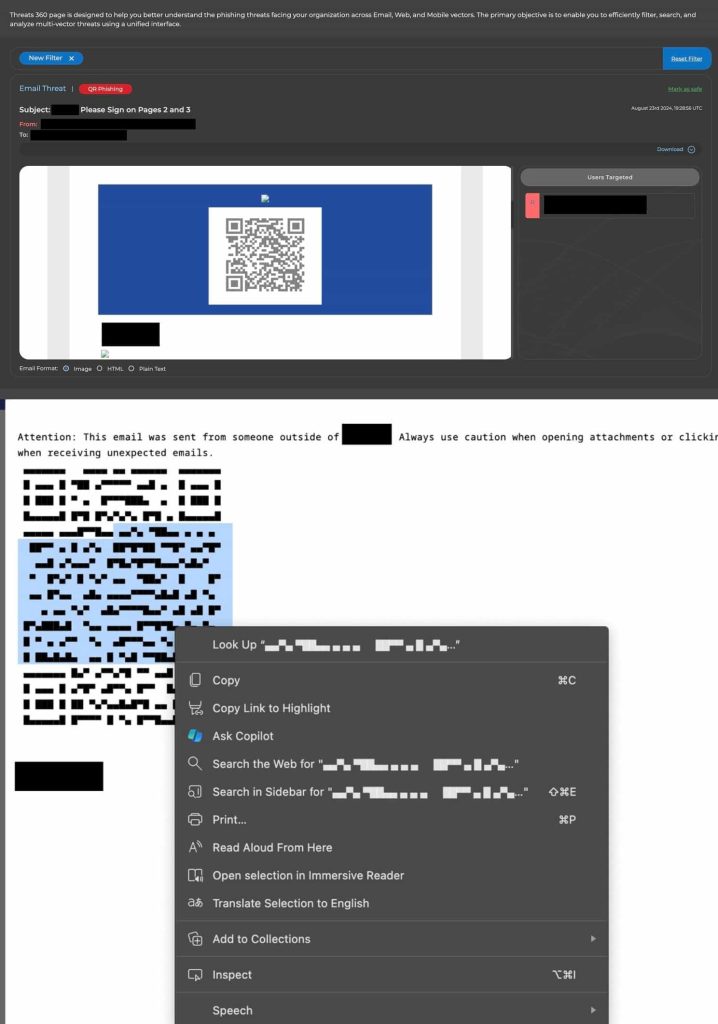
Historically, QR code phishing includes embedding image-based QR codes in emails or different messages. These codes, when scanned, would redirect customers to malicious web sites or set off dangerous actions. Many safety distributors have developed efficient strategies to detect and block these image-based threats. Nevertheless, risk actors have give you a intelligent new solution to entice unsuspecting customers by crafting QR codes utilizing Unicode textual content characters as an alternative of photos.
This new method, referred to as “Unicode QR Code Phishing,” presents a big problem to standard safety measures as a result of most safety instruments are designed to scan for suspicious photos whereas Unicode QR codes bypass this scrutiny as these are text-based.
Furthermore, these codes are simply readable by smartphone cameras regardless of being text-based and the identical code can seem a lot totally different when considered in plain textual content in comparison with when rendered on a display screen, making detection even tougher.
This distinctive method has important implications for safety professionals and end-users alike. Many present QR code detection mechanisms might change into ineffective in opposition to Unicode QR code phishing assaults. Which means even customers who’re cautious about scanning QR codes could also be in danger.
SlashNext’s analysis highlights the necessity for a complete method to safety. Phishing assaults are not confined to emails and might happen throughout numerous platforms. To successfully shield in opposition to these threats, organizations should undertake a multi-layered safety technique.
Finish-users should keep away from scanning QR codes from unknown sources, particularly these in emails or messages and confirm the supply of the data offered by the code in public locations earlier than scanning. We recommend contemplating investing in cellular safety purposes or browser extensions for real-time safety in opposition to web-based threats.
RELATED ARTICLES
- Scammers Rake in $600K with Deepfakes and QR Codes
- New Vishing Assault Spreading FakeCalls Android Malware
- The Forms of Phishing Assaults and The best way to Dodge All of Them
- Ringless Voicemail As A Personalised Buyer Engagement Software
- Hackers Exploit QR Codes with QRLJacking for Malware Distribution