The APT33 Iranian hacking group has used new Tickler malware to backdoor the networks of organizations within the authorities, protection, satellite tv for pc, oil and gasoline sectors in the US and the United Arab Emirates.
As Microsoft safety researchers noticed, the menace group (additionally tracked as Peach Sandstorm and Refined Kitten), which operates on behalf of the Iranian Islamic Revolutionary Guard Corps (IRGC), used this new malware as a part of an intelligence assortment marketing campaign between April and July 2024.
All through these assaults, the menace actors leveraged Microsoft Azure infrastructure for command-and-control (C2), utilizing fraudulent, attacker-controlled Azure subscriptions that the corporate has since disrupted.
APT33 breached focused organizations within the protection, house, schooling, and authorities sectors following profitable password spray assaults between April and Could 2024. In these assaults, they tried to realize entry to many accounts utilizing a small variety of generally used passwords to keep away from triggering account lockouts.
“While the password spray activity appeared consistently across sectors, Microsoft observed Peach Sandstorm exclusively leveraging compromised user accounts in the education sector to procure operational infrastructure. In these cases, the threat actor accessed existing Azure subscriptions or created one using the compromised account to host their infrastructure,” Microsoft mentioned.
The Azure infrastructure they gained management of was utilized in subsequent operations focusing on the federal government, protection, and house sectors.
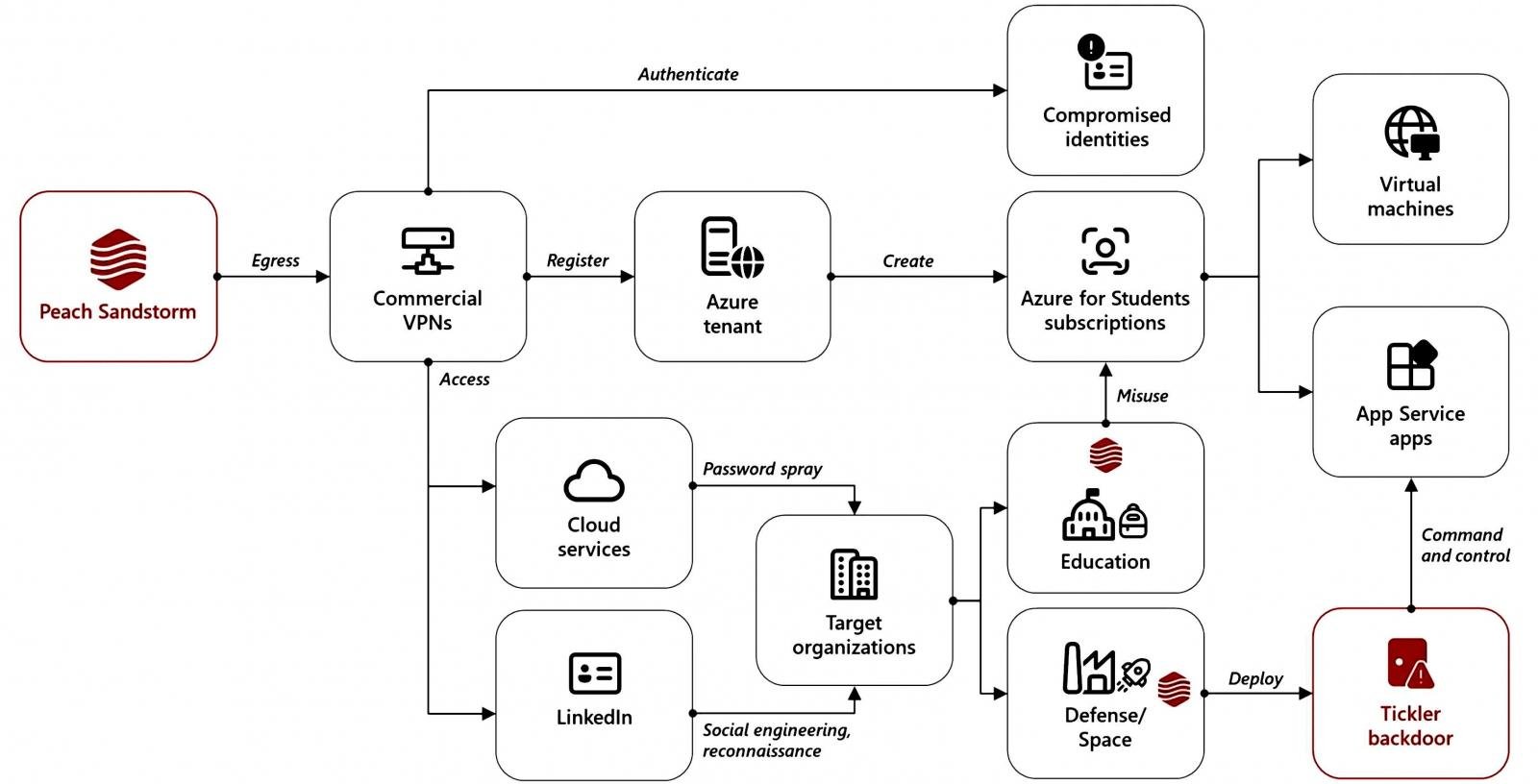
“In the past year, Peach Sandstorm has successfully compromised several organizations, primarily in the aforementioned sectors, using bespoke tooling,” Microsoft added.
The Iranian menace group additionally used this tactic in November 2023 to compromise the networks of protection contractors worldwide and deploy FalseFont backdoor malware.
In September, Microsoft warned of one other APT33 marketing campaign that had focused 1000’s of organizations worldwide in in depth password spray assaults since February 2023, resulting in breaches within the protection, satellite tv for pc, and pharmaceutical sectors.
Microsoft has introduced that beginning October 15, multi-factor authentication (MFA) will probably be necessary for all Azure sign-in makes an attempt to guard Azure accounts in opposition to phishing and hijacking makes an attempt.
The corporate has beforehand discovered that MFA permits 99.99% of MFA-enabled accounts to withstand hacking makes an attempt and reduces the danger of compromise by 98.56%, even when attackers try and breach accounts utilizing beforehand compromised credentials.
