ESET Analysis discovered the Telekopye rip-off community focusing on Reserving.com and Airbnb. Scammers use phishing pages through compromised accounts to steal private and fee particulars from vacationers.
A current investigation by ESET Analysis into the Telekopye rip-off toolkit community has highlighted a problematic development- the community’s growth to focus on well-liked lodging reserving platforms like Reserving.com and Airbnb.
ESET researchers reported a considerable improve in accommodation-themed scams in July 2024, surpassing Telekopye’s authentic marketplace-targeted scams for the primary time. By leveraging compromised accounts of professional accommodations and lodging suppliers, these scammers create extremely convincing phishing pages designed to steal private and monetary data from unsuspecting vacationers.
What’s the Telekopye Toolkit?
Telekopye is a classy toolkit that permits cybercriminals to launch on-line market scams at scale. Operated by organized teams with 1000’s of members, Telekopye supplies scammers with the instruments and infrastructure wanted to execute their fraudulent schemes effectively.
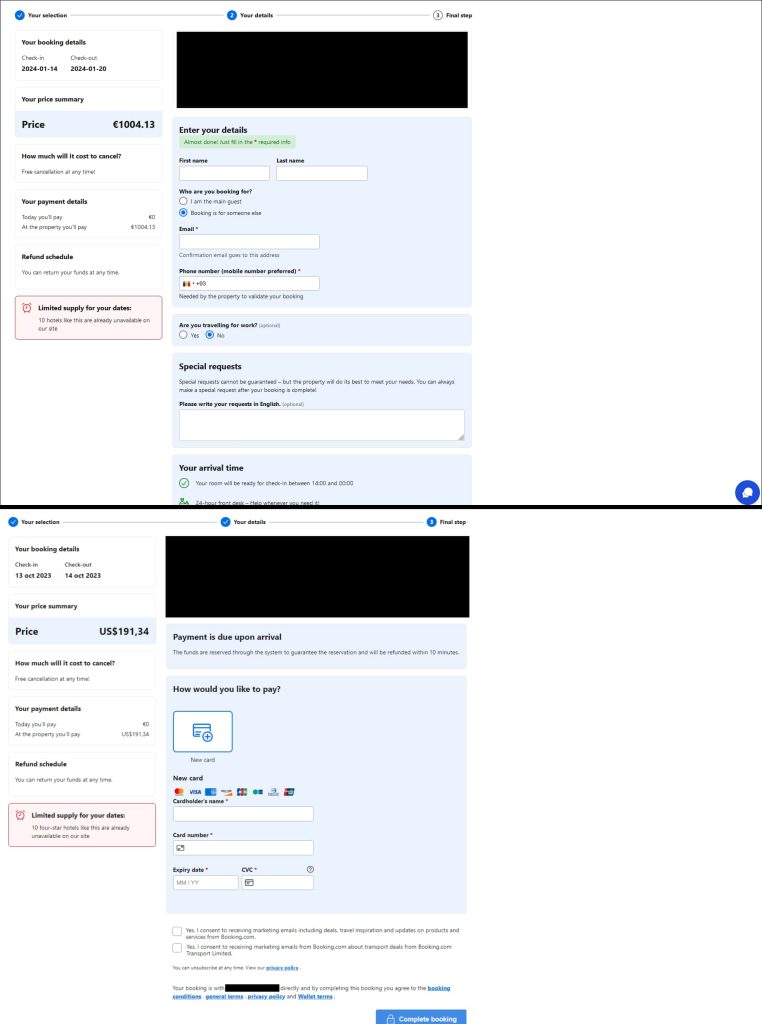
Telekopye scammers, referred to as “Neanderthals,” are focusing on lodging reserving platforms by means of a wide range of misleading methods. This consists of compromised accounts, focused emails, customized phishing pages, and stolen fee data.
Neanderthals purchase professional lodging supplier accounts, doubtless by means of stolen credentials bought on cybercriminal boards. Utilizing these accounts, they ship emails to customers (Mammoths) with current bookings, claiming a fee problem.
In keeping with ESET’s report shared with Hackread.com, the e-mail incorporates a hyperlink to a seemingly professional webpage mimicking the reserving platform. The web page consists of pre-filled details about the person’s particular reserving, making it extremely plausible. As soon as victims click on on the phishing hyperlink, they’re directed to a web page designed to steal their private and monetary data, together with bank card particulars.
“Throughout our tracking of Telekopye, we’ve observed that different Telegram groups implement their own advanced features into the toolkit, aimed at speeding up the scam process, improving communication with targets, protecting phishing websites against disruption by competitors, and other goals.”
Jakub Souček and Radek Jizba -C ybersecurity researchers – ESET
The Rising Risk
Telekopye scams have seen a notable surge in exercise, significantly focusing on Reserving.com and Airbnb customers in the course of the summer season vacation season. This means a rising development and the necessity for elevated consideration from vacationers.
It’s price noting that in late 2023, Czech and Ukrainian police arrested tens of cybercriminals utilizing Telekopye, together with key gamers, in two joint operations following ESET Analysis’s collection. The operations focused an unspecified variety of Telekopye teams, which had amassed no less than €5 million /US$ 5.5 million since 2021.
The arrests helped determine their recruitment and employment practices, indicating that it was primarily managed by middle-aged males from Japanese Europe and West and Central Asia.
To guard your self from Telekopye scams, at all times confirm platform communication with official representatives and keep away from clicking on exterior hyperlinks. Be cautious of bizarre requests for fee or extra data.
Moreover, use sturdy safety practices, corresponding to sturdy passwords and two-factor authentication. By understanding the Telekopye menace and implementing these protecting measures, vacationers can considerably cut back their danger of falling sufferer to those refined scams.
RELATED TOPICS
- RIG Exploit Toolkit Drops CeidPageLock Malware to Hijack Browsers
- New GEOBOX Device Hijacks Raspberry Pi, Lets Hackers Faux Location
- Telegram Android Vulnerability “EvilVideo” Sends Malware as Movies
- FishXProxy Phishing Package Making Phishing Accessible to Script Kiddies
- New V3B Phishing Package Steals Logins and OTPs from EU Banking Customers