A brand new marketing campaign performed by the TA558 hacking group is concealing malicious code inside pictures utilizing steganography to ship numerous malware instruments onto focused methods.
Steganography is the strategy of hiding knowledge inside seemingly innocuous recordsdata to make them undetectable by customers and safety merchandise.
TA558 is a menace actor that has been lively since 2018, recognized for focusing on hospitality and tourism organizations worldwide, specializing in Latin America.
The group’s newest marketing campaign, dubbed “SteganoAmor” because of the intensive use of steganography, was uncovered by Constructive Applied sciences. The researchers recognized over 320 assaults on this marketing campaign that affected numerous sectors and international locations.
SteganoAmor assaults
The assaults start with malicious emails containing seemingly innocuous doc attachments (Excel and Phrase recordsdata) that exploit the CVE-2017-11882 flaw, a generally focused Microsoft Workplace Equation Editor vulnerability fastened in 2017.
Supply: Constructive Applied sciences
The emails are despatched from compromised SMTP servers to reduce the probabilities of the messages getting blocked as they arrive from legit domains.
If an outdated model of Microsoft Workplace is put in, the exploit will obtain a Visible Primary Script (VBS) from the legit ‘paste upon opening the file. ee’ service. This script is then executed to fetch a picture file (JPG) containing a base-64 encoded payload.
Supply: Constructive Applied sciences
PowerShell code contained in the script contained within the picture downloads the ultimate payload hidden inside a textual content file within the type of a reversed base64-encoded executable.
Supply: Constructive Applied sciences
Constructive Applied sciences has noticed a number of variants of the assault chain, delivering a various array of malware households, together with:
- AgentTesla – Spy ware that features as a keylogger and a credential stealer, capturing keystrokes, system clipboard knowledge, taking screenshots, and exfiltrating different delicate data.
- FormBook – Infostealer malware that harvests credentials from numerous net browsers, collects screenshots, screens and logs keystrokes, and may obtain and execute recordsdata in line with the instructions it receives.
- Remcos – Malware that enables the attacker to remotely handle a compromised machine, executing instructions, capturing keystrokes, and turning on the webcam and microphone for surveillance.
- LokiBot – Data-stealer that targets knowledge reminiscent of usernames, passwords, and different data associated to many generally used functions.
- Guloader – Downloader that’s used to distribute secondary payloads, usually packed to evade antivirus detection.
- Snake Keylogger – Information-stealing malware that logs keystrokes, collects system clipboard knowledge, captures screenshots, and harvests credentials from net browsers.
- XWorm – Distant Entry Trojan (RAT) that offers the attacker distant management over the contaminated pc.
The ultimate payloads and malicious scripts are sometimes saved in legit cloud companies like Google Drive, benefiting from their good status to evade getting flagged by AV instruments.
Stolen data is shipped to compromised legit FTP servers used as command and management (C2) infrastructure to make the site visitors seem regular.
Constructive Applied sciences found over 320 assaults, most targeted in Latin American international locations, however the focusing on scope extends worldwide.
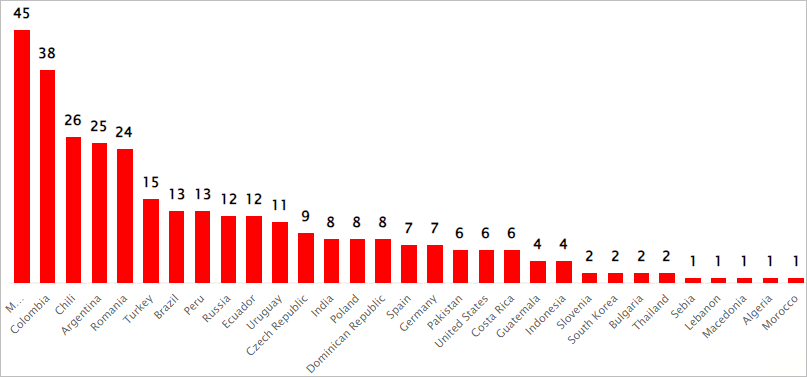
Supply: Constructive Applied sciences
Utilizing a seven-year bug in TA558’s assault chain makes it pretty simple to defend in opposition to SteganoAmor, as updating Microsoft Workplace to a more moderen model would render these assaults ineffective.
An entire record of the symptoms of compromise (IoCs) is offered on the backside of the report.
