SteelFox malware targets software program pirates by means of pretend activation instruments, stealing bank card knowledge and deploying crypto miners. Find out about this new risk affecting customers worldwide and how one can shield your self from this refined cybercrime marketing campaign.
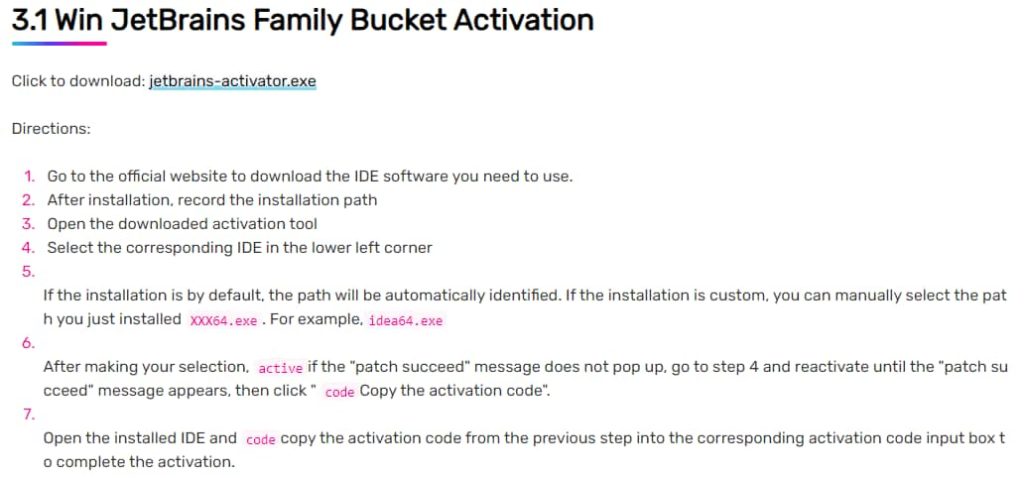
Cybersecurity researchers at Securelist have recognized a brand new sort of malware that has been spreading by means of on-line boards, torrent trackers, and blogs, posing as reputable software program like Foxit PDF Editor, AutoCAD, and JetBrains.
Dubbed “SteelFox” by researchers; the malware’s most important targets are these Microsft Home windows customers who’re concerned in downloading pirated software program and pretend software program activation instruments (cracks).
The marketing campaign, which started in February 2023, combines cryptocurrency mining and knowledge stealing capabilities by means of pretend software program activation instruments. Up to now, the malware has contaminated over 11,000 customers worldwide.
In line with Securelist’s weblog submit shared with Hackread.com forward of publishing, SteelFox is a full-featured “crimeware bundle“ that extracts delicate knowledge from contaminated units, together with bank card info, searching historical past, and login credentials. It additionally collects system info, similar to put in software program, operating providers, and community configurations.
The malware’s preliminary assault vector entails pretend software program activators, that are marketed on on-line boards and torrent trackers as a method to activate reputable software program without cost. As soon as put in, the malware creates a service that stays on the system, even after reboots and makes use of a susceptible driver to advance its privileges.
The malware operates by means of a multi-stage assault chain, starting with a dropper that requires administrator privileges. As soon as executed, it installs itself as a Home windows service and makes use of AES-128 encryption to cover its parts. The malware achieves system-level entry by exploiting susceptible drivers and implements TLS 1.3 with SSL pinning for safe communication with its command servers.
“SteelFox’s Highly sophisticated usage of modern C++ combined with external libraries grants this malware formidable power. Usage of TLSv1.3 and SSL pinning ensures secure communication and harvesting of sensitive data.”
Securelist
International Affect
SteelFox doesn’t seem to focus on particular people or organizations, as a substitute working on a bigger scale to contaminate as many customers as doable. The malware has already contaminated customers in over 10 international locations, together with the next:
- UAE
- India
- Brazil
- China
- Russia
- Egypt
- Algeria
- Mexico
- Vietnam
- Sri Lanka
James McQuiggan, a safety consciousness advocate at KnowBe4, emphasised the significance of organizations being cautious in regards to the sources of their software program downloads. He additionally highlighted the need of coaching staff by means of cybersecurity consciousness packages.
“The dual functionality of SteelFox’s droppers—providing both software “cracks” and malware signifies the advanced instruments utilized by cybercriminals and utilizing an outdated driver for privilege escalation highlights the vital want for organizations to make sure they’re implementing patches.”
“Organizations must ensure they verify software sources, maintain the least user privilege access control, and leverage endpoint protection to detect suspicious installation behaviours,” James defined.
“Furthermore and more importantly, ensure that cybersecurity awareness programs are provided to users about the dangers of unverified software, like open source software or these common applications. Allow for an IT-managed software solution to install and monitor all applications,” he suggested.
Defending Your self from SteelFox
To keep away from turning into victims of SteelFox, customers ought to solely obtain software program from official sources and use a dependable safety answer that may detect and stop the set up of contaminated software program. Moreover, customers must be cautious when clicking hyperlinks or downloading attachments from unknown sources, as these can usually be used to unfold malware.
RELATED TOPICS
- Winos4.0 Malware Concentrating on Home windows through Pretend Gaming Apps
- Fabrice Malware on PyPI Stealing AWS Credentials for 3 Years
- SideWinder hit Android customers with malware apps on Play Retailer
- TodoSwift Malware Targets macOS, Disguised as Bitcoin PDF App
- Octo2 Malware Makes use of Pretend NordVPN Apps to Infect Android Telephones