Bitdefender has launched a decryptor for the ‘ShrinkLocker’ ransomware pressure, which makes use of Home windows’ built-in BitLocker drive encryption software to lock sufferer’s recordsdata.
Found in Might 2024 by researchers at cybersecurity firm Kaspersky, ShrinkLocker lacks the sophistication of different ransomware households however integrates options that may maximize the harm of an assault.
In accordance with Bitdefender’s evaluation, the malware seems to have been repurposed from benign ten-year-old code, utilizing VBScript, and leverages typically outdated methods.
The researchers be aware that ShrinkLocker’s operators appear to be low-skilled, utilizing redundant code and typos, forsaking reconnaissance logs within the type of textual content recordsdata, and depend on available instruments.
Nonetheless, the menace actor has had profitable assaults on company targets.
In a report at the moment, Bitdefender highlights a ShrinkLocker assault towards a healthcare group the place attackers encrypted Home windows 10, Home windows 11, and Home windows Server units throughout the community, together with backups.
The encryption course of completed in 2.5 hours and the group misplaced entry to essential techniques, probably dealing with difficulties in offering affected person care.
Bitdefender is releasing a free decryption software that may assist ShrinkLocker victims get well their recordsdata.
ShrinkLocker assaults
As an alternative of utilizing customized encryption implementations like conventional ransomware, ShrinkLocker makes use of Home windows BitLocker with a randomly generated password that’s despatched to the attacker.
The malware first runs a Home windows Administration Instrumentation (WMI) question to checks if BitLocker is accessible on the goal system, and installs the software if not current.
Subsequent, it removes all default protections that preserve the drive from being encrypted accidentally. For velocity, it makes use of the ‘-UsedSpaceOnly’ flag to have BitLocker solely encrypt occupied area on the disk.
The random password is generated utilizing community visitors and reminiscence utilization knowledge, so there aren’t any patterns to make brute-forcing possible.
The ShrinkLocker script may also delete and reconfigure all BitLocker protectors, to make harder the restoration of the encryption keys.
“Protectors are mechanisms used by BitLocker to protect the encryption key. They can include hardware protectors like TPMs or software protectors like passwords or recovery keys. By deleting all protectors, the script aims to make it impossible for the victim to recover their data or decrypt the drive,” Bitdefender explains.
For propagation, ShrinkLocker makes use of Group Coverage Objects (GPOs) and scheduled duties, modifies Group Coverage settings on Lively Listing area controllers, and creates duties for all domain-joined machines to make sure the encryption of all drives on the compromised community.
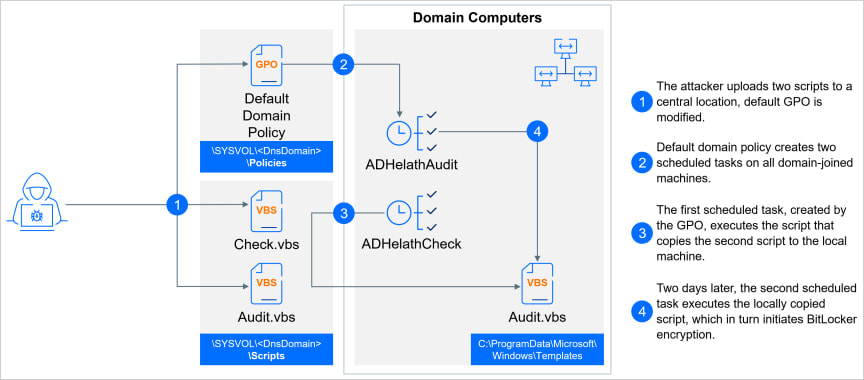
Supply: Bitdefender
After reboot, victims see a BitLocker password display that additionally consists of the menace actor’s contact particulars.
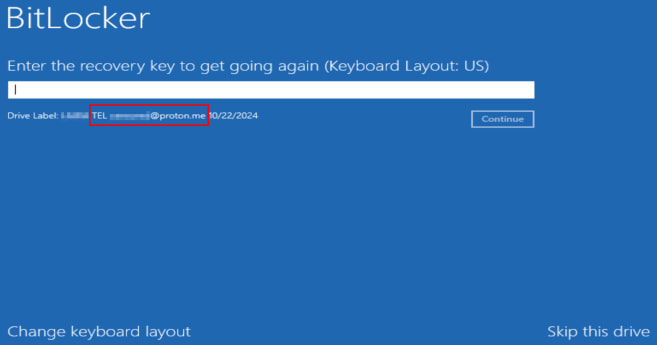
Supply: Bitdefender
Bitdefender releases decryptor
Bitdefender created and launched a decryptor that reverses the sequence during which ShrinkLocker deletes and reconfigures BitLocker’s protectors.
The researchers say that they recognized “a specific window of opportunity for data recovery immediately after the removal of protectors from BitLocker-encrypted disks,” which permits them to decrypt and get well the password set by the attacker.
This makes it doable to reverse the encryption course of and convey the drives again to their earlier, unencrypted state.
ShrinkLocker victims can obtain the software and use it from a USB drive linked to the impacted techniques. When the BitLocker restoration display reveals, customers ought to enter BitLocker Restoration Mode and skip all of the steps to get to Superior choices, which gives a command immediate that permits launching the decryption software.
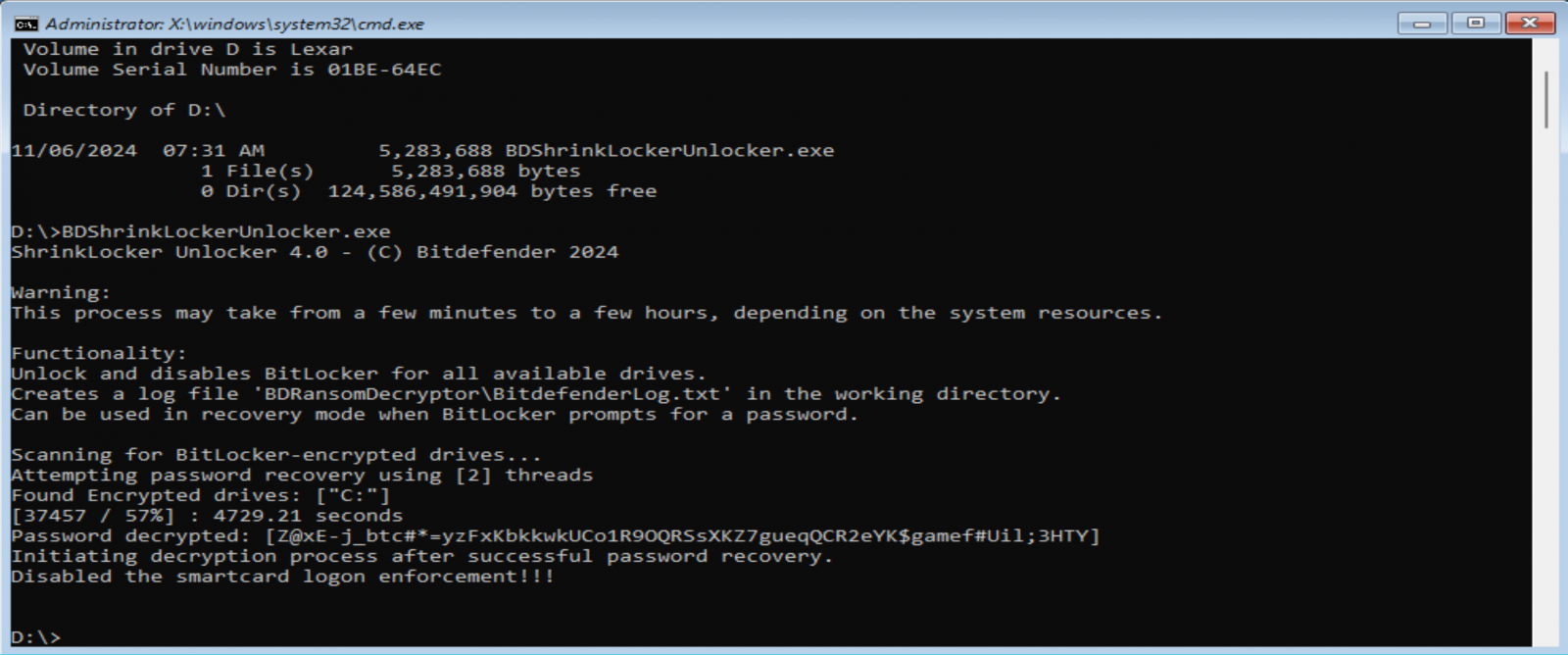
Supply: Bitdefender
The researchers warn that the time to decrypt the info depends upon the system’s {hardware} and the complexity of the encryption and will take a while.
When executed, the decryptor will unlock the drive and disable good card-based authentication.
Bitdefender notes that the decryptor solely works on Home windows 10, Home windows 11, and up to date Home windows Server variations and is simplest when used shortly after the ransomware assault, when BitLocker’s configurations will not be absolutely overridden but and will be recovered.
Sadly, this methodology is not going to work to get well BitLocker passwords created utilizing different strategies.
