Researchers have found two methods that might allow attackers to bypass audit logs or generate much less extreme entries when downloading information from SharePoint.
Microsoft SharePoint is a web-based collaborative platform that integrates with Microsoft Workplace and 365, primarily as a doc administration and knowledge storage system.
Many corporations use it for doc administration and collaboration, creating web sites and company intranets, automating complicated workflows, and enterprise content material administration functions.
As a result of sensitivity of SharePoint knowledge, many corporations audit delicate occasions, just like the downloading of knowledge, to set off alerts in cloud entry safety instruments, knowledge loss prevention instruments, and safety info and occasion administration platforms (SIEMs).
Supply: Varonis
Researchers on the Varonis Menace Labs have devised two easy methods that allow customers to bypass audit logs or generate much less delicate occasions by downloading knowledge a sure means or disguising it as knowledge syncing actions.
Silent knowledge exfiltration
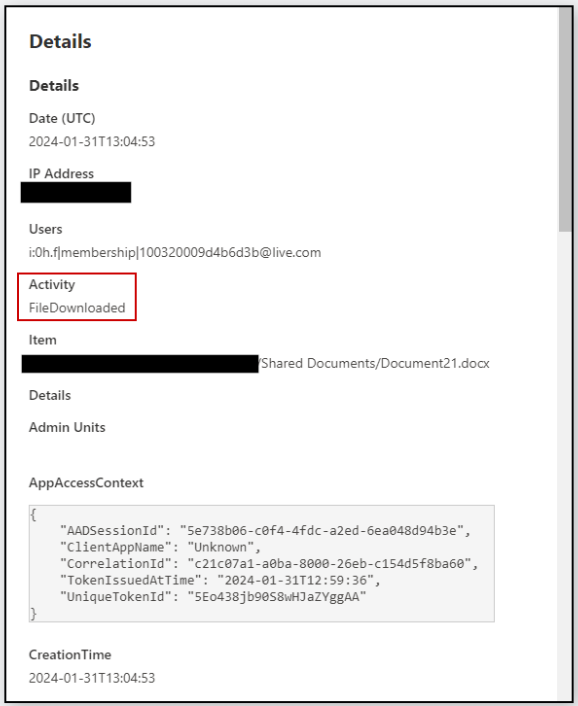
The primary method described in Varonis’ report takes benefit of SharePoint’s “Open in App” characteristic, which permits customers to open paperwork with functions like Microsoft Phrase as an alternative of utilizing the online browser, which is the default choice.
Using this characteristic doesn’t generate a “FileDownloaded” occasion in SharePoint’s audit logs however as an alternative creates an “Access” occasion that directors might ignore.
Supply: Varonis
Opening the file from a cloud location creates a shell command with the non-expiring URL from the file’s location on the cloud endpoint, which somebody can use to obtain the file with out restrictions.
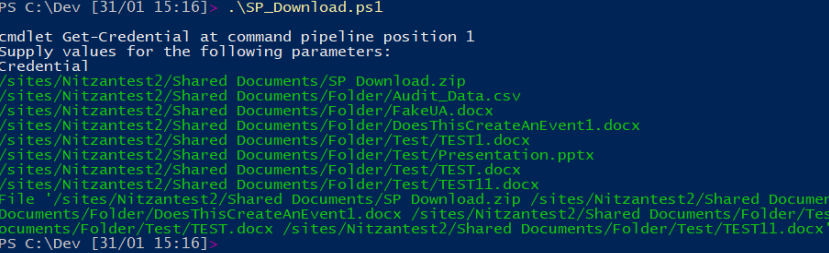
Varonis additionally notes that misuse of “Open in App” may be each guide and automatic, utilizing a customized PowerShell script that might allow somebody to exfiltrate massive lists of information shortly.
Supply: Varonis
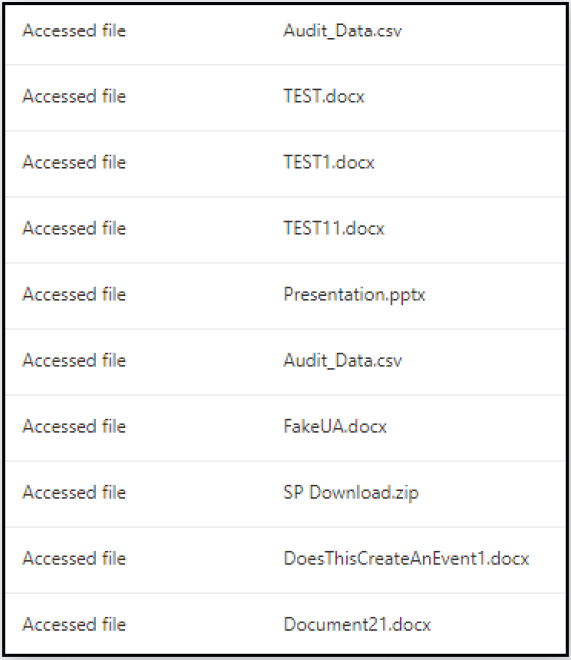
The second method includes spoofing the Person-Agent string of the file entry requests to imitate Microsoft SkyDriveSync, a service used for file synchronization between SharePoint and a person’s native pc.
This trick makes the file downloads carried out through the browser or Microsoft Graph API seem within the logs as knowledge syncing occasions (“FileSyncDownloadedFull”), lowering the chance of scrutiny by safety groups.
On this case, too, the alteration of the Person-Agent string and subsequent file exfiltration may be accomplished manually or through a PowerShell script to automate the method.
Mitigation
Varonis disclosed these bugs in November 2023, and Microsoft added the failings to a patch backlog for future fixing.
Nevertheless, the problems have been rated as average severity, so they will not obtain instant fixes. Subsequently, SharePoint admins ought to pay attention to these dangers and be taught to establish and mitigate them till patches grow to be out there.
Varonis recommends monitoring for prime volumes of entry exercise inside a brief timeframe and the introduction of recent gadgets from uncommon places, which could possibly be indicators of unauthorized knowledge exfiltration.
Furthermore, safety groups are advisable to scrutinize sync occasions for anomalies in frequency and knowledge volumes and attempt to establish uncommon exercise patterns.
BleepingComputer has reached out to Microsoft to be taught extra about their plans for addressing the problems offered by Varonis, however we’ve got but to obtain a remark.
