A brand new, extra subtle variant of the FakeCall malware is focusing on Android gadgets. Study in regards to the superior options that make this malware a severe menace, together with display capturing and remote-control capabilities.
Cybersecurity researchers at Zimperium’s zLabs have recognized a “Scary” new variant of the FakeCall malware. This malware tips victims into calling fraudulent telephone numbers, resulting in id theft and monetary loss. FakeCall is a vishing (voice phishing) malware which, as soon as put in, can take nearly full management of a focused Android telephone.
The most recent variant displays a number of new functionalities together with the flexibility to determine, compress, and add picture thumbnails, selectively add particular photos, remotely management the display, simulate consumer actions, seize and transmit stay video feeds, and remotely unlock the gadget. These options can seize delicate paperwork or private images.
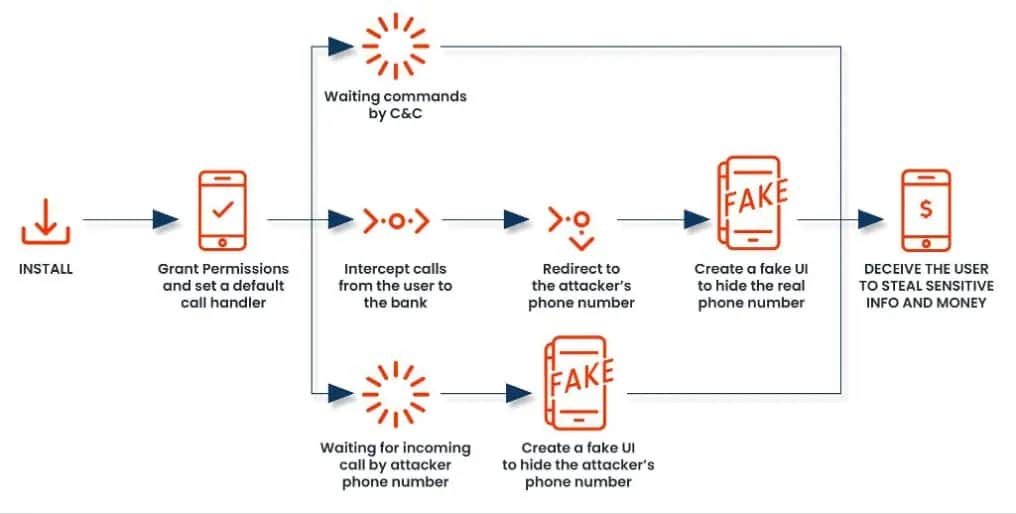
The FakeCall malware usually infiltrates a tool by a malicious app downloaded from a compromised web site or a phishing e mail. The app requests permission to turn out to be the default name handler. If granted, the malware positive aspects intensive privileges.
In response to Zimperium’s weblog submit shared with Hackread.com forward of publishing on Wednesday, attackers are utilizing a service known as “The Phone Listener Service” of their assault. The truth is, this service is a crucial part of the malware, enabling it to control the gadget’s calling capabilities permitting it to intercept and management all incoming and outgoing and seize delicate data, resembling one-time passwords (OTP) or account verification codes.
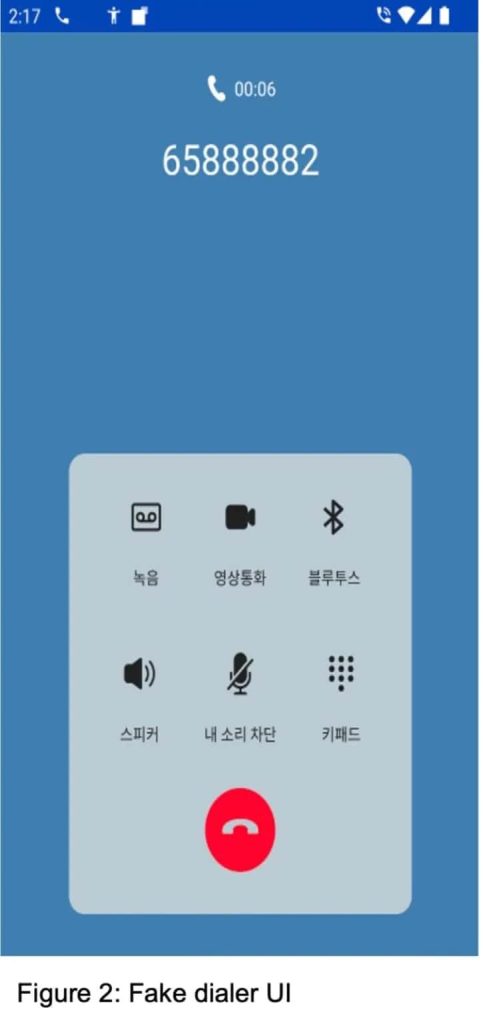
As well as, the malware can manipulate the gadget’s show to indicate faux name interfaces, tricking victims into offering delicate data. Moreover, it could manipulate name logs to cover its malicious exercise and management the period of calls. These capabilities permit attackers to deceive victims into revealing delicate data or transferring funds.
The malware additionally exploits the Android Accessibility Service to seize display content material and manipulate the gadget’s show to create a misleading consumer interface whereas mimicking the professional telephone app. This trick permits attackers to steal delicate data, conduct surveillance, and even remotely management the gadget.
It displays occasions from the inventory dialer app and detects permission prompts from the system permission supervisor and system UI. Upon detecting particular occasions, it could grant permissions for the malware, bypassing consumer consent. The malware permits distant attackers to regulate the sufferer’s gadget UI, permitting them to simulate consumer interactions and manipulate the gadget with precision.
To guard in opposition to such malware, at all times obtain apps from trusted sources like Google Play Retailer, be cautious about permission requests, and use cellular safety software program with on-device detection capabilities.
RELATED TOPICS
- Unicode QR Code Phishing Rip-off Bypasses Conventional Safety
- Malware Assault Imitates VPN, Safety Apps on Android Telephones
- Antidot Android Malware Poses as Google Replace to Steal Funds
- QR Code Rip-off: Faux Voicemails Hits Customers, 1000 Assaults in 14 Days
- Superior Vishing Assault Marketing campaign “LetsCall” Targets Android Customers