A brand new phishing-as-a-service (PhaaS) platform named ‘Rockstar 2FA’ has emerged, facilitating large-scale adversary-in-the-middle (AiTM) assaults to steal Microsoft 365 credentials.
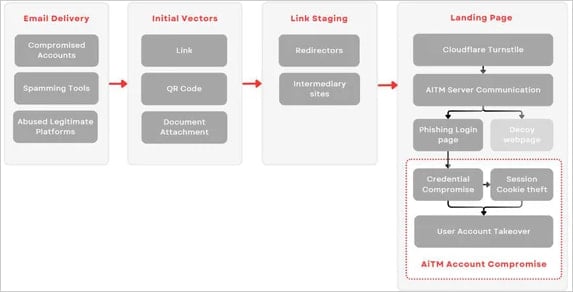
Like different AiTM platforms, Rockstar 2FA allows attackers to bypass multifactor authentication (MFA) protections on focused accounts by intercepting legitimate session cookies.
These assaults work by directing victims to a faux login web page that mimics Microsoft 365 and tricking them into coming into their credentials.
The AiTM server acts as a proxy, forwarding these credentials to Microsoft’s professional service to finish the authentication course of after which captures the cookie when it’s despatched again to the goal’s browser.
This cookie can then be utilized by the risk actors for direct entry to the sufferer’s account, even when it is MFA protected, with the risk actor not needing the credentials in any respect.
Supply: Trustwave
Rise of Rockstar 2FA
Trustwave stories that Rockstar 2FA is definitely an up to date model of the phishing kits DadSec and Phoenix, which gained traction in early and late 2023 respectively.
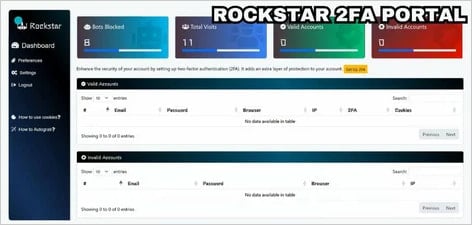
The researchers say Rockstar 2FA has gained important recognition within the cybercrime group since August 2024, promoting for $200 for 2 weeks or $180 for API entry renewal.
Supply: Trustwave
The service is promoted on Telegram, amongst different locations, boasting a protracted record of options like:
- Help for Microsoft 365, Hotmail, Godaddy, SSO
- Randomized supply code and hyperlinks to evade detection
- Cloudflare Turnstile Captcha integration for sufferer screening
- Automated FUD attachments and hyperlinks
- Consumer-friendly admin panel with real-time logs and backup choices
- A number of login web page themes with automated group branding (emblem, background)
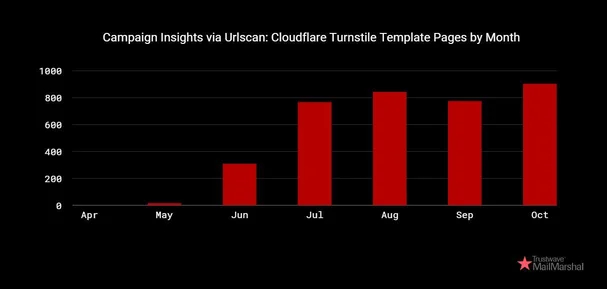
The service has arrange over 5,000 phishing domains since Might 2024, facilitating numerous phishing operations.
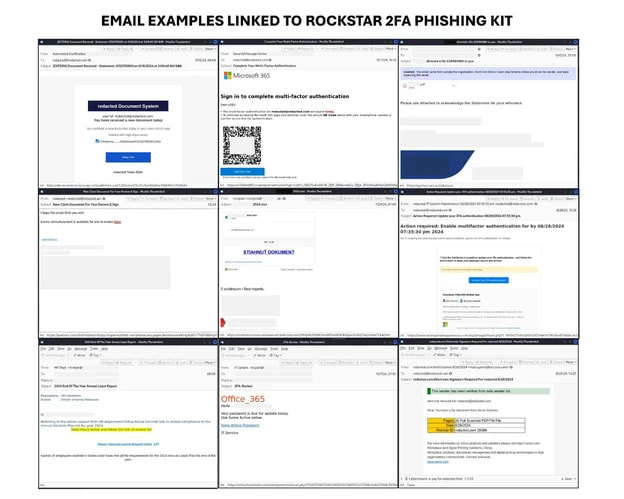
The researchers say that the associated phishing campaigns they noticed abuse professional e-mail advertising platforms or compromised accounts for disseminating malicious messages to targets.
The messages use quite a lot of lures, together with document-sharing notifications, IT division notices, password reset alerts, and payroll-related messages.
Trustwave says these messages make the most of a spread of block evasion strategies together with QR codes, inclusion of hyperlinks from professional shortening companies, and PDF attachments.
Supply: Trustwave
A Cloudflare turnstile problem is used to filter out bots, whereas the assault additionally doubtless contains IP checks earlier than legitimate targets are directed to a Microsoft 365 login phishing web page.
Supply: Turstwave
If the customer is deemed a bot, safety researcher, or an out-of-scope goal usually, they’re redirected to a innocent car-themed decoy web page as an alternative.
The JavaScript on the touchdown web page decrypts and retrieves both the phishing web page or the car-themed decoy primarily based on the AiTM server’s analysis of the customer.
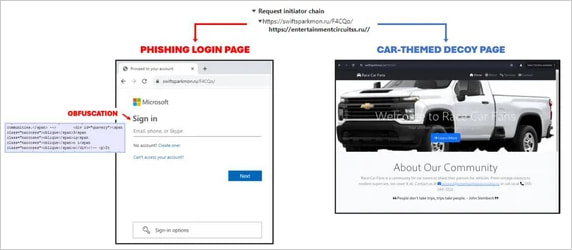
Supply: Trustwave
The emergence and proliferation of Rockstar 2FA replicate the persistence of phishing operators, who proceed to supply illicit companies regardless of important legislation enforcement operations taking down one of many largest PhaaS platforms lately and arresting its operators.
So long as these commodity instruments proceed to be accessible for cybercriminals at a low value, the chance of large-scale efficient phishing operations stays important.
