A brand new phishing equipment has been launched that enables crimson teamers and cybercriminals to create progressive net Apps (PWAs) that show convincing company login kinds to steal credentials.
A PWA is a web-based app created utilizing HTML, CSS, and JavaScript that may be put in from an internet site like a daily desktop software. As soon as put in, the working system will create a PWA shortcut and add it to Add or Take away Packages in Home windows and beneath the /Customers/<account>/Functions/ folder in macOS.
When launched, a progressive net app will run within the browser you put in it from however be displayed as a desktop software with all the usual browser controls hidden.
Many web sites use a PWA to supply a desktop app expertise, together with X, Instagram, Fb, and TikTok.
Supply: BleepingComputer
Utilizing PWAs to phish for credentials
A brand new phishing toolkit created by safety researcher mr.d0x demonstrates the best way to create PWA apps to show company login kinds, even with a faux tackle bar exhibiting the traditional company login URL to make it look extra convincing.
“PWAs integrate with the OS better (i.e. they have their own app icon, can push notifications) and therefore they can lead to higher engagement for websites,” the researcher explains in a weblog put up concerning the new toolkit.
“The issue with PWAs is that manipulating the UI for phishing purposes is possible as we’ll explore in this blog.”
Whereas the brand new phishing templates would require some convincing to get a person to put in the PWA, there are situations the place it could be simpler to take action.
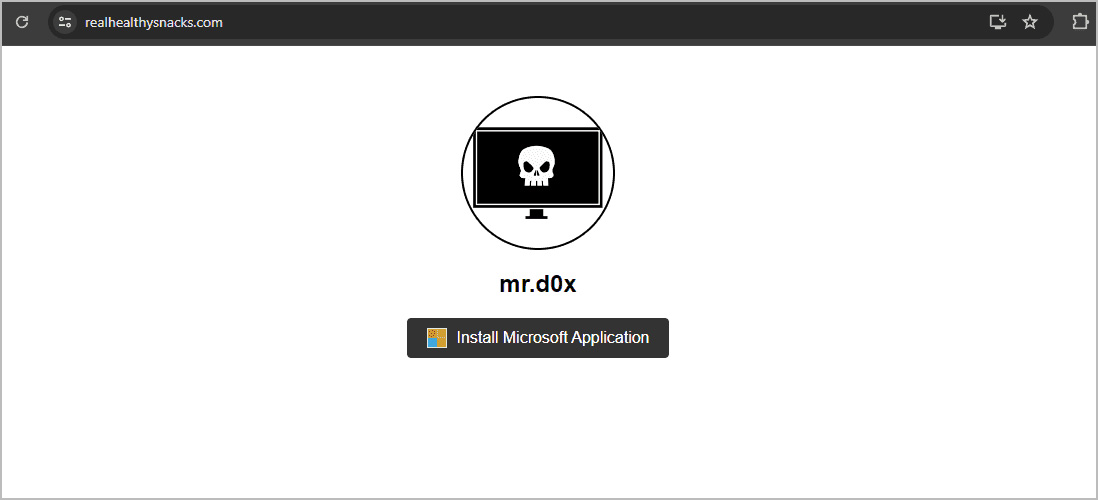
It’s normal for menace actors to create web sites designed to distribute applications that set up malware, as we noticed prior to now with faux NordVPN and ProtonVPN websites and faux Home windows PC cleaners.
In an analogous method, a menace actor can create websites selling faux software program or distant administration instruments that embody a button to put in their software program, as proven beneath.
Supply: mr.d0x
When the customer clicks on the set up button, the browser will set up the PWA and add it to the working system, with Home windows prompting as as to whether you wish to create a shortcut on the Taskbar.
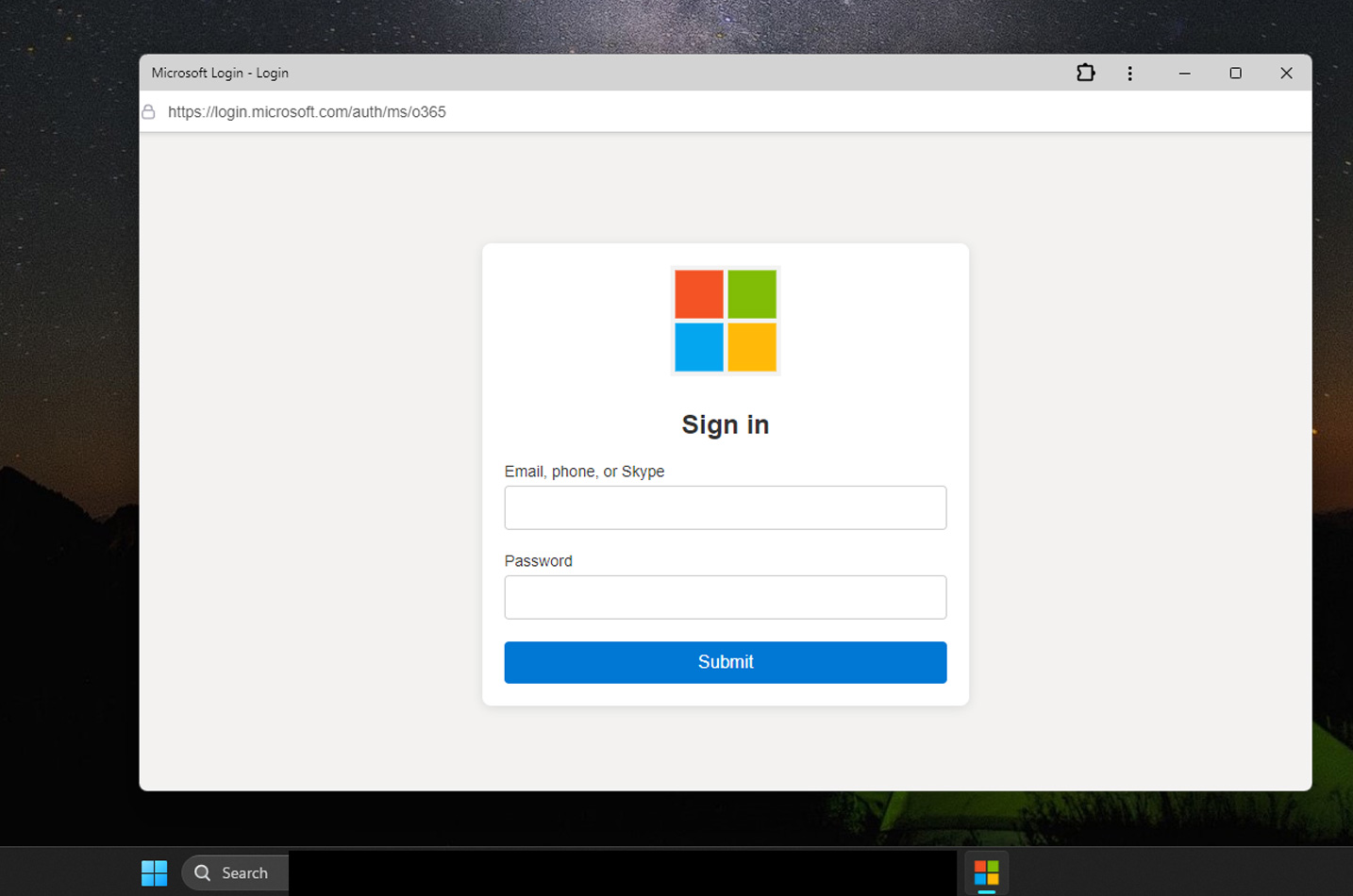
When the PWA robotically launches, although, it should immediate the person to enter their credentials to log in, whether or not these are, for instance, for a VPN product, Microsoft, AWS, or on-line retailer credentials.
This system stands out as a result of mr.d0x illustrates how one can combine a faux tackle bar containing a faux URL within the PWA, much like the way it was carried out within the Browser-in-the-Browser method. This may trigger the login kind to seem extra authentic to the goal.
Supply: mr.d0x
The researcher has launched the PWA phishing templates on GitHub, permitting anybody to check or modify them for their very own situations.
“Users that don’t use PWAs often may be more suspectible to this technique as they might be unaware that PWAs should not have a URL bar. Even though Chrome appears to have taken measures against this by periodically showing the real domain in the title bar, I think people’s habits of “checking the URL” will render that measure much less helpful.
Moreover, what number of safety consciousness applications right now point out PWA phishing? I can solely communicate from private expertise and I have not seen firms point out this of their coaching. The dearth of familiarity with PWA and the hazard they will probably pose would possibly make this method simpler.
I can see this method being utilized by attackers to request customers to put in a software program after which within the PWA window the phishing occurs. This was demonstrated within the demo video I offered.
Lastly, one factor to remember is that Home windows actively prompts the person to pin the PWA to the duty bar. The following time the window is opened it should robotically open the URL talked about within the “start_url” parameter within the manifest file. This may occasionally trigger the person to pin the PWA and use it greater than as soon as, offering the attacker with extra outcomes.”
❖ mr.d0x advised BleepingComputer
The researcher is thought for his earlier phishing toolkits that show faux file archivers within the browser, use VNC to bypass MFA, and the infamous Browser within the Browser templates, which have been abused by ransomware gangs and to steal Steam credentials.
Whereas this new PWA phishing technique would require extra convincing to get targets to put in the app, it received’t be stunning if we discover menace actors using this method in some unspecified time in the future sooner or later.
Sadly, no current group insurance policies can forestall the set up of progressive net apps, with current insurance policies solely permitting you to ban particular extension IDs or entry to particular URLs.
In 2018, researchers from the Korea Superior Institute of Science & Know-how (KAIST) launched a paper investigating progressive net apps and their potential safety dangers.
An indication of the PWA phishing equipment will be seen beneath.
