Spanish audio system beware! A brand new marketing campaign utilizing the Agent Tesla RAT targets Spanish-speaking people. Discover ways to defend your self from this and different malware assaults.
FortiGuard Labs has found a phishing marketing campaign concentrating on Spanish-speaking people to unfold a brand new Agent Tesla malware variant. The marketing campaign makes use of numerous methods to focus on Home windows-based methods and ship the core module, together with MS Workplace vulnerabilities, JavaScript code, PowerShell code, and fileless modules, wrote FortiGuard Labs’ researcher Xiapeng Zhang of their report.
Right here is how the assault works:
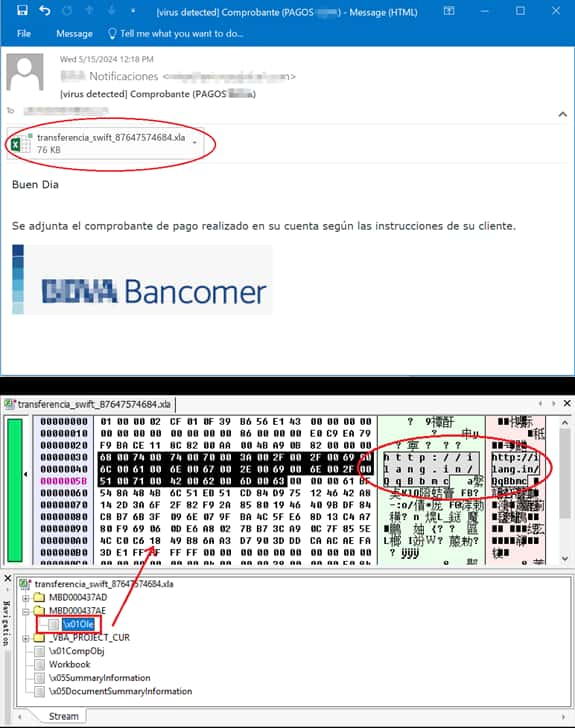
A Spanish-language phishing e-mail posing as a SWIFT switch notification from a big monetary establishment is shipped to MS Home windows customers. The e-mail, translated into English, seems to be a message with a disguised Excel attachment in OLE format with crafted embedded knowledge that exploits the CVE-2017-0199 vulnerability.
The attachment accommodates an embedded OLE hyperlink, opened routinely as soon as the sufferer begins the Excel file. Later, it routinely downloads an RTF doc, which is opened by the Phrase program.
One other vulnerability exploited on this assault is CVE-2017-11882, a Distant Code Execution vulnerability in Microsoft Workplace’s Equation Editor element, permitting attackers to execute arbitrary code on a sufferer’s laptop by overriding a return tackle within the stack.
This Agent Tesla variant is a strong, versatile 32-bit, .NET-based Distant Entry Trojan (RAT) granting attackers full management over contaminated units. As soon as put in, it might probably steal delicate info from 80 software program purposes, specializing in login credentials, banking particulars, and e-mail contacts.
Moreover, it checks if the e-mail consumer is Thunderbird, cookies from a variety of internet browsers akin to Chromium-based and Mozilla-based browsers, system clipboard knowledge, laptop title, OS/CPU/RAM info, and saved credentials. It might additionally spy on you by capturing keystrokes and screenshots. The malware is assigned a important severity stage.
As per the report revealed by FortiGuard Labs, the Agent Tesla core module is a fileless module downloaded by a malicious JavaScript base64-encoded Powershell code as a traditional JPG file from this URL:
uploaddeimagens[.]com[.]br/pictures/004/773/812/unique/js.jpg?1713882778.This module is rarely saved within the native folder, making it troublesome for researchers to detect. Surprisingly, this variant makes use of FTP protocol for knowledge submission, in contrast to previous variants that used HTTP POST and SMTP protocols.
Furthermore, it “detects whether it’s running in an analysis environment, like sandboxes, virtual machines, etc., or where there is AV software running, like Avast, Comodo, etc.,” Zhang famous.
To remain protected, be cautious of phishing emails, replace the working system usually, use sturdy passwords, and spend money on respected anti-malware options.
RELATED TOPICS
- Agent Tesla, Taskun Malware Concentrating on US Schooling Orgs
- Agent Tesla variant steals passwords from, browsers, VPNs
- Konni RAT Exploiting Phrase Docs to Steal Information from Home windows
- Agent Tesla Variant Makes use of Excel Exploit to Infect Home windows PCs
- Hackers Use Phrase paperwork to drop NetSupport Supervisor RAT