SUMMARY
- Phishing Rip-off Targets PayPal: Scammers exploit PayPal’s system to hyperlink sufferer accounts to unauthorized addresses.
- Reliable-Trying Emails: The rip-off makes use of real-looking emails and legitimate PayPal login pages to deceive customers.
- Microsoft365 Exploit: Attackers use MS365 domains to ship PayPal cash requests, bypassing phishing filters.
- Account Takeover: Victims unknowingly hyperlink their PayPal accounts to the scammer, risking monetary loss.
- Keep Secure: Keep away from unsolicited emails, confirm URLs, and allow 2FA to guard your PayPal account.
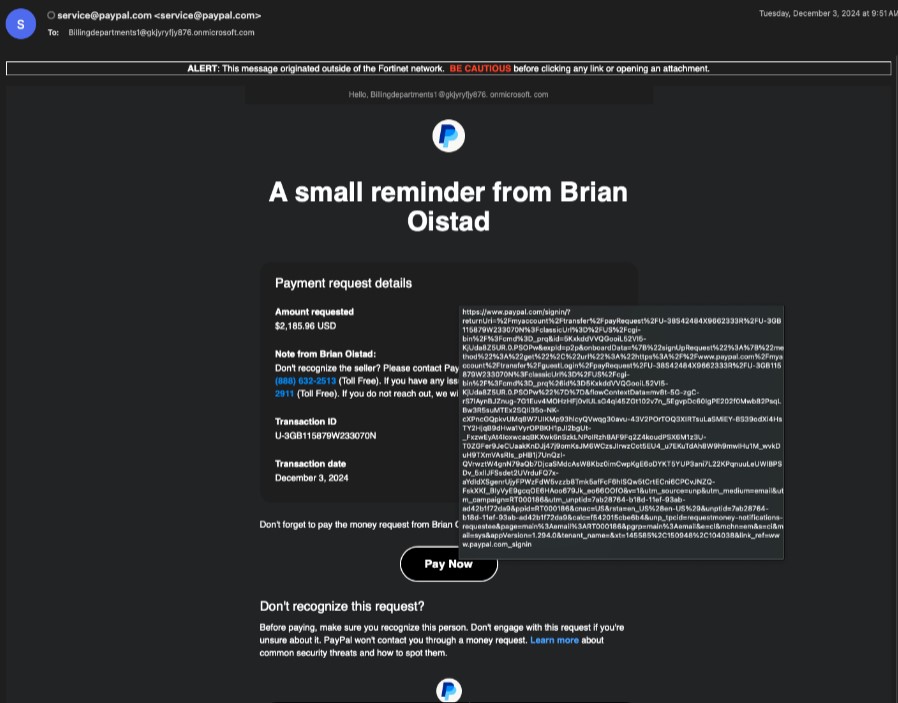
Fortinet’s FortiGuard Labs has recognized a complicated PayPal phishing rip-off concentrating on unsuspecting customers by exploiting a loophole within the platform’s system. In accordance with Fortinet’s CISO (Chief Data Safety Officer) Carl Windsor, the rip-off leverages professional PayPal performance to trick customers into linking their accounts to unauthorized addresses, doubtlessly granting attackers management over their funds.
The assault makes use of a seemingly professional e-mail, usually with a sound sender handle and a genuine-looking URL. Nonetheless, the true hazard lies inside the e-mail’s content material. It directs recipients to a professional PayPal login web page, prompting them to log in to research a supposed cost request.
Additional probing revealed that the scammer registered an MS365 check area and created a Distribution Checklist containing sufferer emails (Billingdepartments1gkjyryfjy876.onmicrosoft.com), then despatched a professional PayPal cash request to all recipients.
They added the listing to the PayPal net portal and distributed it to focused victims. The Microsoft365 SRS rewrite scheme rewrites the sender to cross the SPF/DKIM/DMARC verify. It’s price noting that Microsoft365 SRS (Sender Rewriting Scheme) is a characteristic in Microsoft 365 that rewrites the sender handle of an e-mail message.
As soon as the sufferer logs in, the scammer’s account is linked to the sufferer’s account, permitting them to take management of the sufferer’s PayPal account, a trick that bypasses PayPal’s phishing verify directions.
“The beauty of this attack is that it doesn’t use traditional phishing methods. The email, the URLs, and everything else are perfectly valid. Instead, the best solution is the Human Firewall—someone who has been trained to be aware and cautious of any unsolicited email, regardless of how genuine it may look,” Windsor wrote in a weblog submit.
This new phishing rip-off highlights the significance of cybersecurity consciousness. Customers have to be cautious of unsolicited emails, keep away from clicking on hyperlinks or attachments from unknown senders, hover over hyperlinks to confirm URLs, and by no means enter login credentials on web sites until sure of the authenticity. Enabling two-factor authentication (2FA) on PayPal accounts can additional improve safety.
RELATED TOPICS
- PayPal Notifies 35,000 Customers of Knowledge Breach
- PayPal Customers hit with “Suspicious Activity” Phishing Rip-off
- Microsoft, PayPal, Fb most focused manufacturers in phishing
- World Financial institution SSL Certificates Hacked to Host PayPal Phishing Rip-off
- DocuSign API Abused to Evade Spam Filters with Phishing Invoices