A brand new model of the Octo Android malware, named “Octo2,” has been seen spreading throughout Europe beneath the guise of NordVPN, Google Chrome, and an app known as Europe Enterprise.
The brand new variant, analyzed by ThreatFabric, options higher operational stability, extra superior anti-analysis and anti-detection mechanisms, and a website technology algorithm (DGA) system for resilient command and management (C2) communications.
Finally, its look within the wild confirms that the mission is alive and evolving regardless of the turbulence it went via lately.
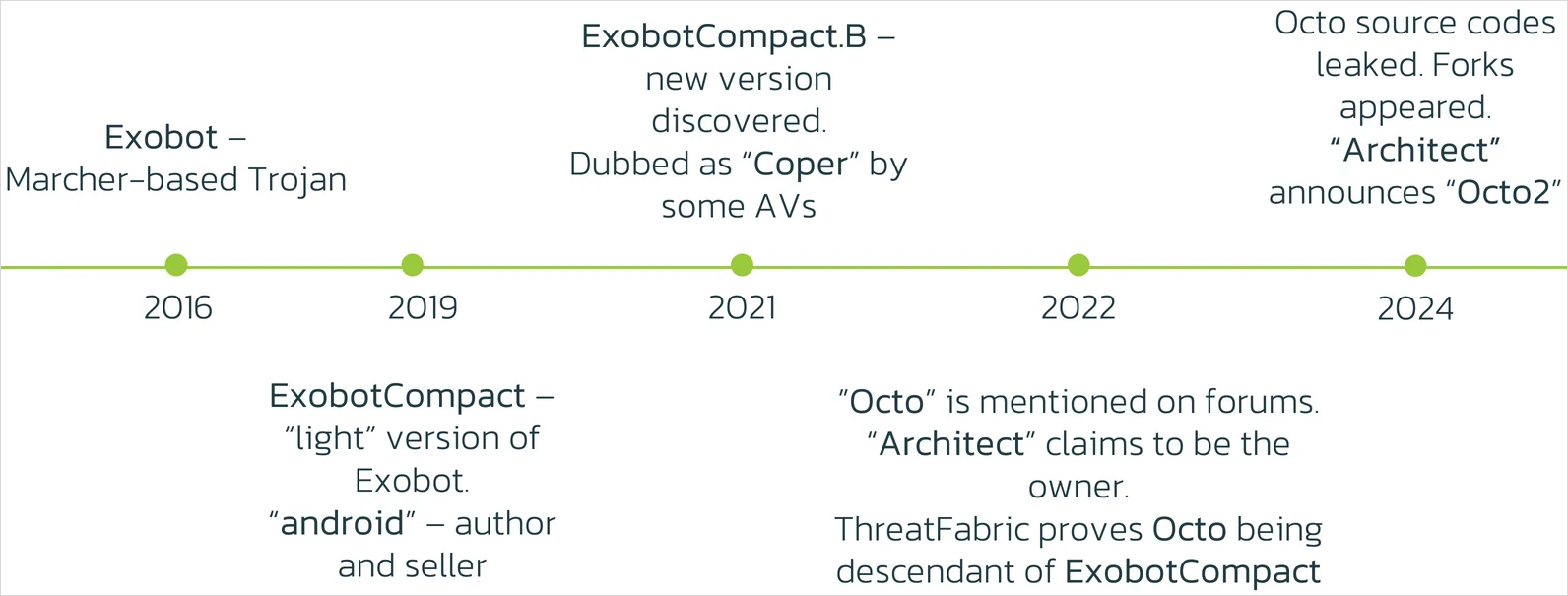
Transient historical past and evolution
Octo is an Android banking trojan that advanced from ExoCompact (2019-2021), which itself was based mostly on the ExoBot trojan that launched in 2016 and had its supply code leaked on-line in the summertime of 2018.
ThreatFabric found the primary model of Octo in April 2022 on faux cleaner apps in Google Play. TF’s report on the time highlighted the malware’s on-device fraud capabilities that allowed its operators in depth entry to the sufferer’s information.
Amongst different issues, Octo v1 supported keylogging, on-device navigation, SMS and push notification interception, system display locking, sound muting, arbitrary app launches, and utilizing contaminated gadgets for SMS distribution.
ThreatFabric says the Octo was leaked this yr, inflicting a number of forks of the malware to look within the wild, presumably making a dent within the gross sales for the unique creator, ‘Architect.’
Following these occasions, Architect introduced Octo2, seemingly as an try to throw an upgraded model into the malware market and spark cybercriminals’ curiosity. The malware’s creator even introduced a particular low cost for patrons of Octo v1.
Supply: ThreatFabric
Octo2 operations in Europe
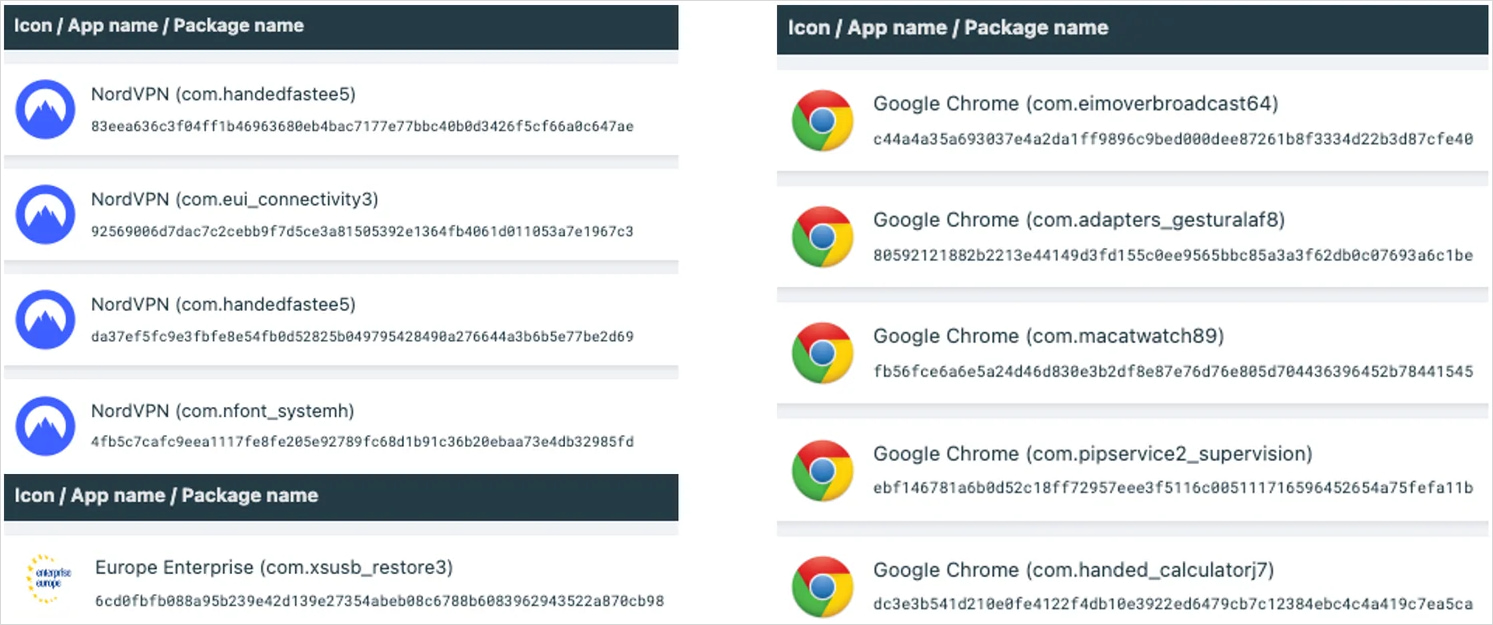
Campaigns at present deploying Octo2 concentrate on Italy, Poland, Moldova, and Hungary. Nevertheless, because the Octo Malware-as-a-Service (MaaS) platform has beforehand facilitated assaults worldwide, together with within the U.S., Canada, Australia, and the Center East, we are going to seemingly see Octo2 campaigns seem in different areas quickly.
In European operations, the menace actors use faux NordVPN and Google Chrome apps, in addition to a Europe Enterprise app, which is probably going a lure utilized in focused assaults.
Octo2 makes use of the Zombider service so as to add the malicious payload into these APKs whereas bypassing Android 13 (and later) safety restrictions.
Supply: ThreatFabric
Extra steady, extra evasive, extra succesful
Octo2 is extra of a rolling improve to the primary model, bettering the malware incrementally fairly than implementing ground-breaking adjustments or rewriting code from scratch.
First, the malware creator launched a brand new low-quality setting on the distant entry software (RAT) module known as “SHIT_QUALITY” that reduces information transmissions to a minimal, permitting extra dependable connectivity when web connection speeds are subpar.
Octo2 additionally decrypts its payload utilizing native code and complicates evaluation by dynamically loading extra libraries throughout execution, additional bettering its already robust evasion capabilities.
Lastly, Octo2 introduces a DGA-based C2 area system that enables the operators to rapidly replace and change to new C2 servers, rendering blocklists ineffective and bettering resilience in opposition to server takedown makes an attempt.
ThreatFabric additionally notes that Octo2 now receives a listing of apps to intercept and block push notifications from, permitting the operators to refine their concentrating on scope.
Octo2 has not been noticed on Google Play, so its distribution is at present believed to be restricted to third-party app shops, which Android customers ought to keep away from.
