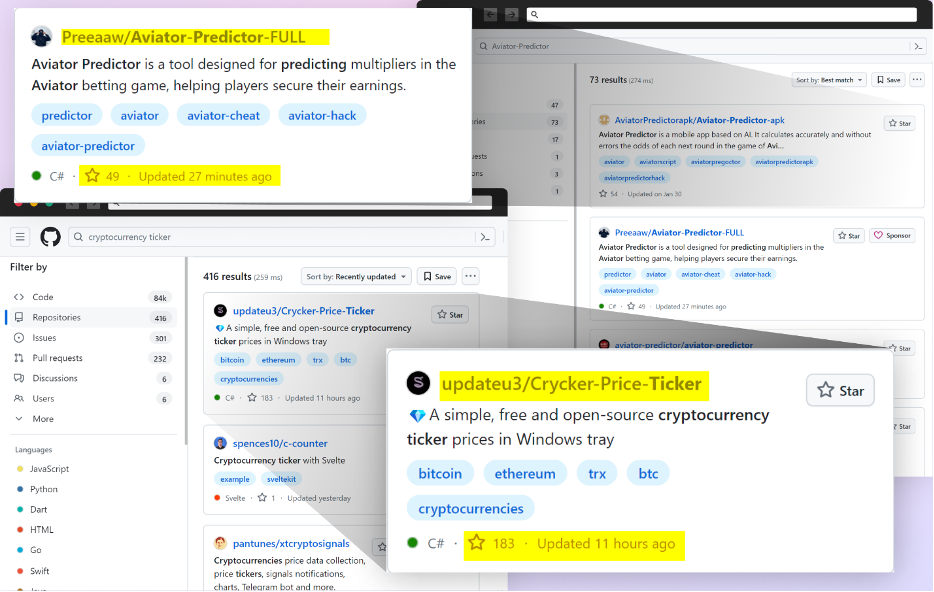
In a current assault marketing campaign, cybercriminals had been found cleverly manipulating GitHub’s search performance, and utilizing meticulously crafted repositories to distribute malware.
Key Factors
- GitHub search manipulation: Attackers create malicious repositories with fashionable names and matters, utilizing strategies like automated updates and pretend stars to spice up search rankings and deceive customers.
- Malicious code is commonly hidden inside Visible Studio venture recordsdata (.csproj or .vcxproj) to evade detection, routinely executing when the venture is constructed.
- The attacker had arrange the stage to change the payload primarily based on the sufferer’s origin, checking particularly if the sufferer is predicated in Russia. At this level, we do not see this potential activated.
- The current malware marketing campaign includes a big, padded executable file that shares similarities with the “Keyzetsu clipper” malware, concentrating on cryptocurrency wallets.
- The malware establishes persistence on contaminated Home windows machines by making a scheduled activity that runs the malicious executable each day at 4AM with out consumer affirmation.
- Builders ought to be cautious when utilizing code from public repositories and look ahead to suspicious repository properties, corresponding to excessive commit frequencies and stargazers with just lately created accounts.
Exploiting GitHub’s Search Performance
Our current findings reveal a menace actor creating GitHub repositories with names and matters which are more likely to be searched by unsuspecting customers. These repositories are cleverly disguised as legit initiatives, usually associated to fashionable video games, cheats, or instruments, making it troublesome for customers to tell apart them from benign code.
To make sure most visibility, the attackers make use of a few intelligent strategies that constantly place their malicious repositories on the prime of GitHub search outcomes.
Automated Updates
By leveraging GitHub Actions, the attackers routinely replace the repositories at a really excessive frequency by modifying a file, often known as “log”, with the present date and time or simply some random small change. This steady exercise artificially boosts the repositories’ visibility, particularly for situations the place customers filter their outcomes by “most recently updated,” growing the probability of unsuspecting customers discovering and accessing them.
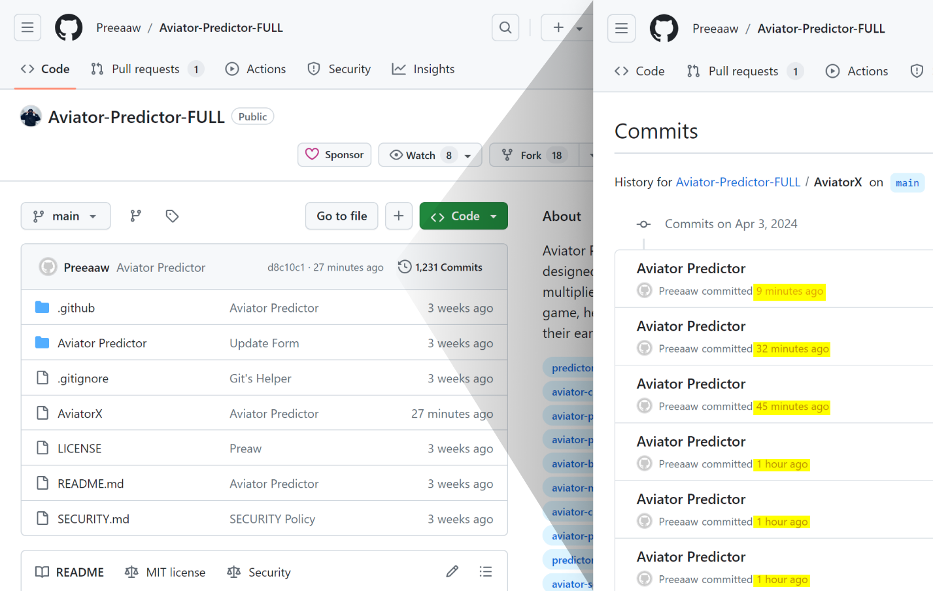
Faking Reputation
Whereas automated updates assist, the attackers mix one other approach to amplify the effectiveness of their repo making it to the highest outcomes.
The attackers employed a number of pretend accounts so as to add bogus stars, creating an phantasm of recognition and trustworthiness. This artificially boosts the repositories’ visibility additional, particularly for situations the place customers filter their outcomes by “most stars.”
In distinction to previous incidents the place attackers had been discovered so as to add tons of or hundreds of stars to their repos, it seems that in these instances, the attackers opted for a extra modest variety of stars, in all probability to keep away from elevating suspicion with an exaggerated quantity.
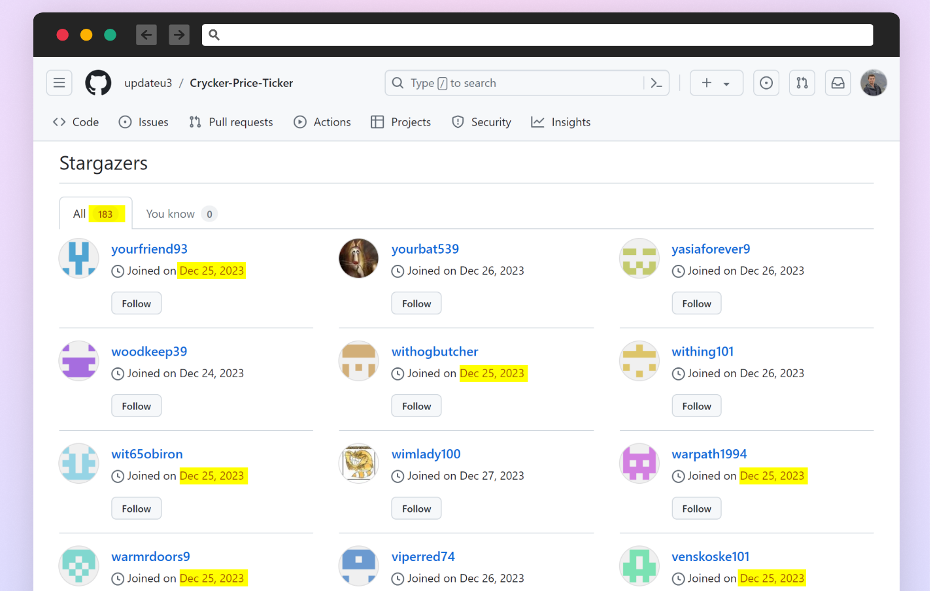
Most of the stargazers are created on the identical date. A purple flag for pretend accounts.
This social engineering approach is designed to govern customers into believing that the repository is broadly used and dependable, preying on the inherent belief customers place in highly-starred repositories.
Unsuspecting customers, usually drawn to the highest search outcomes and repositories with seemingly optimistic engagement, usually tend to click on on these malicious repositories and use the code or instruments they supply, unaware of the hidden risks lurking inside.
For a deeper dive into the tactic of pretend stars, try our current weblog that explores this manipulation approach in better element.
Hidden Malware in Undertaking Information
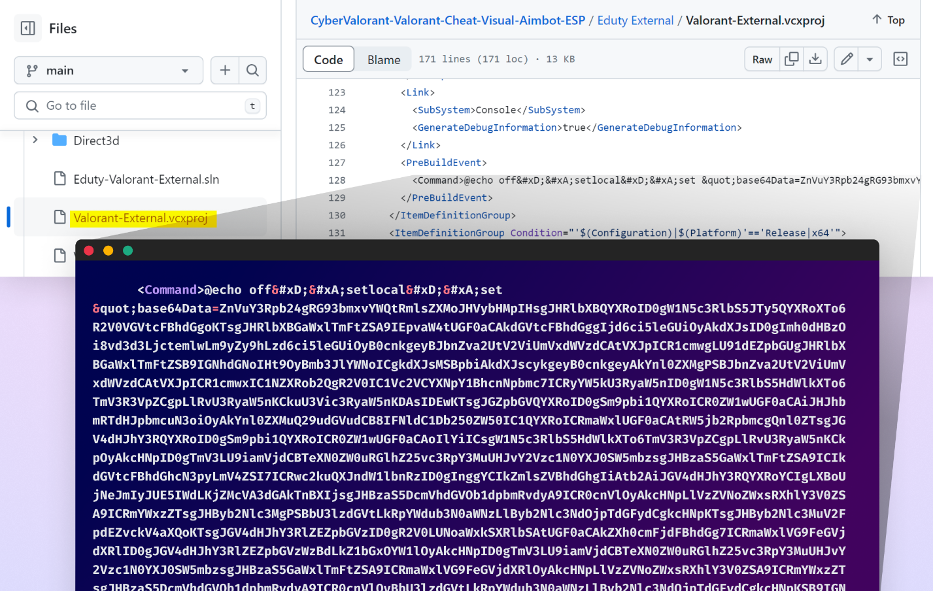
The attackers conceal their malware primarily as obfuscated code deep throughout the .csproj or .vcxproj recordsdata of the repository (recordsdata generally utilized in Visible Studio initiatives) to lower the possibilities of the typical consumer detecting it except they proactively seek for suspicious components.
Nevertheless, it is value noting that there have been a small variety of different detected repos that contained totally different malware inside different recordsdata.
Technical Evaluation of the Frequent Malicious Payload
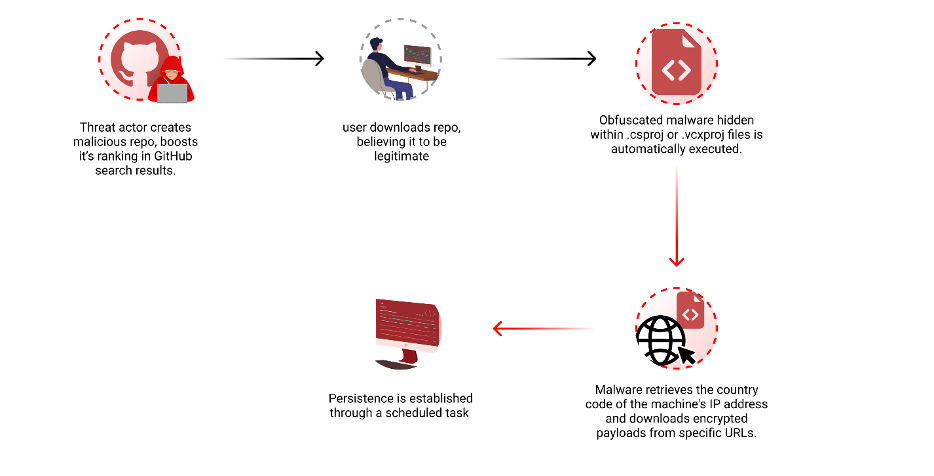
The malicious script is embedded inside a pre-build occasion of a Visible Studio venture file (.vcxproj) and is designed to be executed routinely throughout the construct course of. The script consists of two most important elements:
- A batch script that units up the setting and executes a VBScript file.
- A base64-encoded PowerShell script that’s decoded and executed by the VBScript file.
The batch script creates a brief listing, generates a VBScript file, and decodes the base64-encoded PowerShell script. It then executes the decoded PowerShell script and cleans up the non permanent recordsdata.
The decoded PowerShell script performs the next malicious actions:
- Retrieves the nation code of the machine’s IP tackle, figuring out whether or not the machine is predicated in Russia.
- Downloads content material from particular URLs primarily based on the nation code (content material is repeatedly up to date by the attacker)
- Downloads encrypted recordsdata from every URL, extracts them with a predefined password, and executes the extracted recordsdata.
The script additionally employs error dealing with to silently catch exceptions and proceed execution.
Energetic Marketing campaign
On April third, the attacker up to date the malicious code inside certainly one of their repositories, pointing to a brand new URL that downloads a distinct encrypted .7z file containing an executable named feedbackAPI.exe.
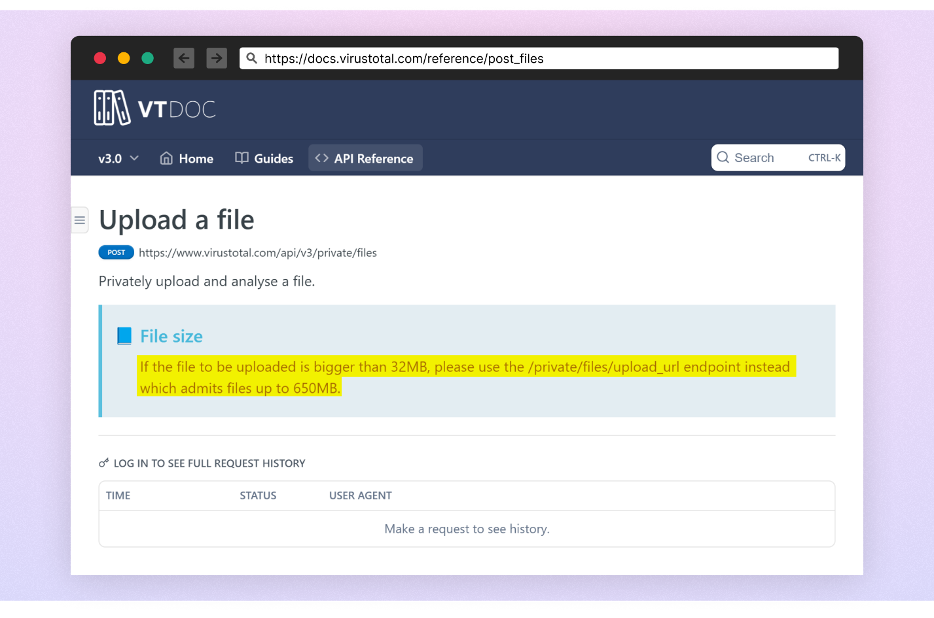
The attacker had padded the executable with many zeros, a way used to artificially enhance the file dimension. As a result of this padding, the file dimension exceeded the edge of many safety options, VirusTotal being a notable one, stopping the potential for it from being scanned. In keeping with VirusTotal’s documentation,
“If the file to be uploaded is larger than 32MB, please use the /non-public/recordsdata/upload_url endpoint as an alternative which admits recordsdata as much as 650MB.”
The padded feedbackAPI.exe file was 750MB in dimension, exceeding even the elevated restrict for the choice endpoint.
The outcomes of our evaluation of this malware counsel that the malware accommodates similarities to the “Keyzetsu clipper” malware, a comparatively new addition to the rising record of crypto pockets clippers generally distributed by means of pirated software program.
This executable file additionally makes an attempt to create persistence on Home windows machines. It achieves this by making a shortcut to the exe file after which establishing a each day scheduled activity named “Feedback_API_VS_Services_Client” that executes the shortcut at 4AM. Notably, this activity is created with none affirmation prompts, making it stealthier and extra more likely to go unnoticed by unsuspecting customers.
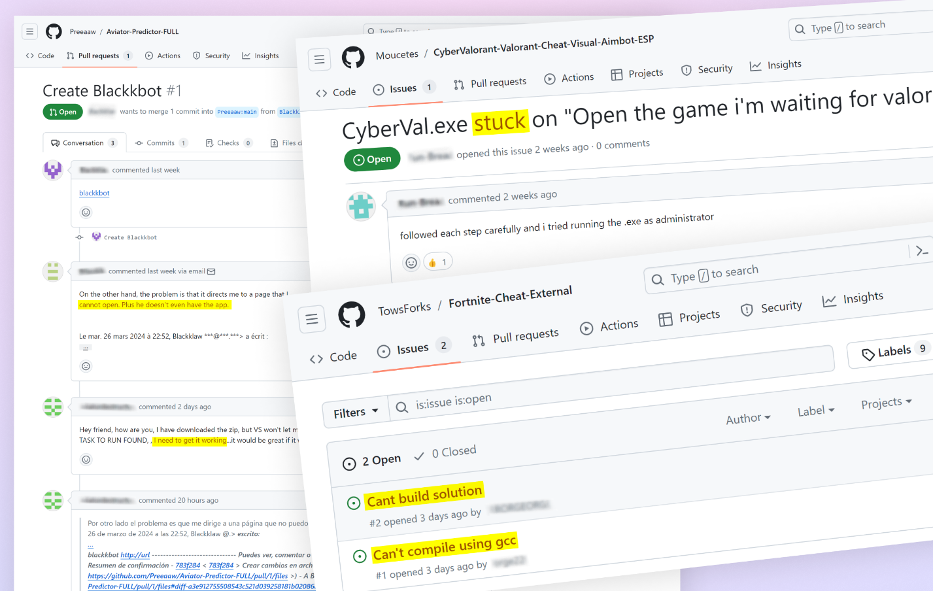
Indicators of Profitable Exploitation
Proof signifies that the attackers’ marketing campaign has efficiently deceived unsuspecting customers. Quite a few malicious repositories have obtained complaints by means of Points and pull requests from customers who skilled issues after downloading and utilizing the code.
Conclusion
The usage of malicious GitHub repositories to distribute malware is an ongoing development that poses a big menace to the open-source ecosystem. By exploiting GitHub’s search performance and manipulating repository properties, attackers can lure unsuspecting customers into downloading and executing malicious code.
To stop falling sufferer to comparable assaults, it is strongly recommended to keep watch over the next suspicious properties of a repo:
- Commit frequency: Does the repo have a unprecedented variety of commits relative to its age? Are these commits altering the identical file with very minor modifications?
- Stargazers: Who’s starring this repo? Do many of the stargazers seem to have had accounts created across the similar time?
By being conscious of those purple flags, customers can higher shield themselves from inadvertently downloading and executing malware.
Within the aftermath of the XZ assault and lots of different current incidents, it will be irresponsible for builders to rely solely on repute as a metric when utilizing open supply code. A developer who blindly takes code additionally blindly takes duty for that code. These incidents spotlight the need for guide code evaluations or the usage of specialised instruments that carry out thorough code inspections for malware. Merely checking for identified vulnerabilities is inadequate.
As a part of Checkmarx’s dedication to provide chain safety, our analysis staff repeatedly displays and detects suspicious actions within the open-source software program ecosystem. We monitor and flag potential indicators of malicious conduct and promptly alert our clients and the group to assist shield them from these evolving threats.
Working collectively to maintain the open supply ecosystem secure.
IOC
- hxxps[:]//cdn.discordapp[.]com/attachments/1192526919577649306/1211404800575537304/VisualStudioEN.7z?ex=6612fda3&is=660088a3&hm=5ae3b1b5d2c7dc91a9c07a65dbf8c61d3822b1f16a2d7c70eb37a039979e8290&
- hxxps[:]//cdn.discordapp[.]com/attachments/1192526919577649306/1211403074799804476/VisualStudioRU.7z?ex=6612fc07&is=66008707&hm=0a7fc9432f5ef58960b1f9a215c3feceb4e7704afd7179753faa93438d7e8f54&
- 08b799d56265e93f6aae4f089808d1cb
- cc9d54b78688ef6f41e4f4d0c8bced3e04bfcedc
- ooocyber[.]keenetic[.]professional
- 188[.]113[.]132[.]109
- https://rentry.co/MuckCompanyMMC/uncooked
- hxxps[:]//rentry[.]co/hwqfx/uncooked
- hxxps[:]//rentry[.]co/q3i7zp/uncooked
- hxxps[:]//rentry[.]co/tvfwh/uncooked
- hxxps[:]//cdn[.]discordapp.com/attachments/1193658583947149322/1218876343232630844/most important.exe?ex=6609420d&is=65f6cd0d&hm=f5a0af7499e892637935c3e4071f2dc59d48214f56a1c1d7aedc3392f58176db&
- hxxps[:]//paste[.]fo/uncooked/dd6cd76eb5a0
- hxxps[:]//paste[.]fo/uncooked/efda79f59c55
- hxxps[:]//rentry[.]co/4543t/uncooked
- hxxps[:]//rentry[.]co/a2edp
- hxxps[:]//textbin[.]internet/uncooked/gr2vzmwcvt