New Linux malware ‘Perfctl’ is concentrating on tens of millions worldwide, mimicking system information to evade detection. This subtle malware compromises Linux servers, exploiting vulnerabilities for cryptomining and system useful resource hijacking.
Cybersecurity researchers at Aqua Nautilus have found a brand new Linux malware that has focused tens of millions worldwide, exploiting over 20,000 misconfigurations. The malware has been lurking for a while, however lately attacked a Nautilus honeypot, offering a possibility to detect and look at this risk that may put any Linux server in danger.
In response to Aqua Nautilus, this subtle Linux malware dubbed “perfctl” has been quietly concentrating on servers worldwide over the previous few years. This extremely persistent and evasive risk has been actively in search of vulnerabilities and misconfigurations to compromise programs.
The malware’s title comes from the cryptominer course of, which drains system sources and causes vital points for Linux builders. Within the firm’s technical analysis, shared completely with Hackread.com forward of publishing on October 3 Thursday, there have been quite a few incident studies and discussions in on-line communities pointing to the widespread prevalence of perfctl.
The malware’s impression has been felt throughout numerous developer boards, together with Reddit, Stack Overflow, and others. “Usually in some of these posts, you can find replies with links to reports about the malware written by researchers. But in this case, however, none of these had links to such reports,” famous Assaf Morag and Idan Revivo of their analysis.
One other regarding development highlighted by researchers is that Perfctl makes use of rootkits and evasion methods to cover its presence from normal system instruments and monitoring processes. It quickly suspends its actions when new customers log in, making it tougher to detect. As well as, Perfctl makes use of Unix sockets for inner communication and the Tor community for exterior connections, making it tough to trace its actions.
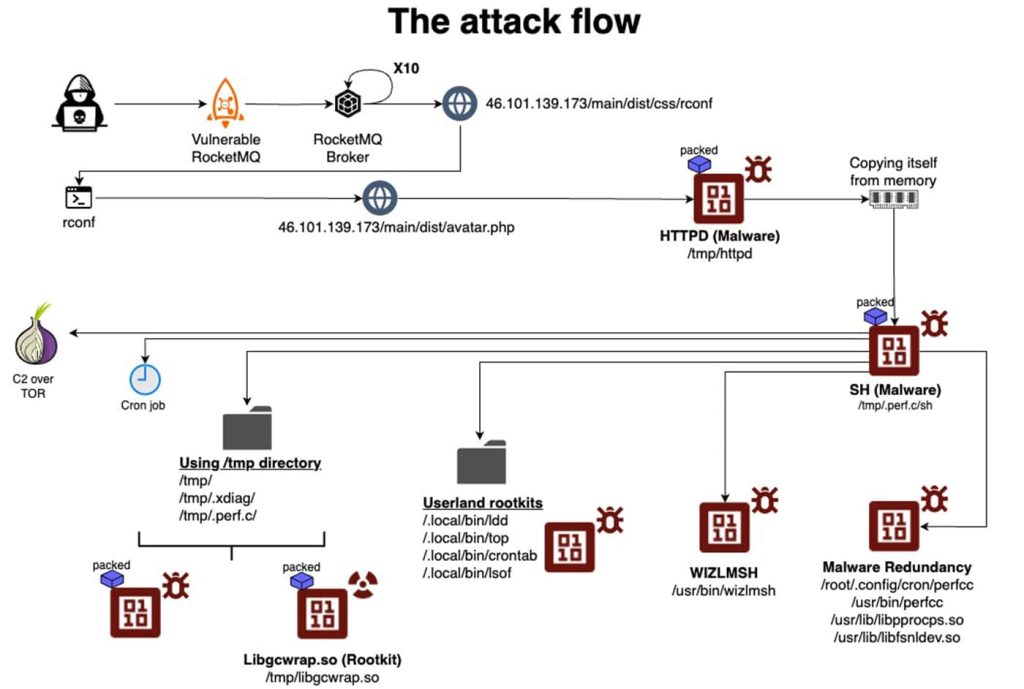
The assault begins with the malware downloading a foremost payload from an attacker-controlled HTTP server managed, named “httpd”. This payload has a number of layers of execution, guaranteeing persistence and evading detection. The malware copies itself to a brand new location, runs a brand new binary, terminates the unique course of, and deletes the preliminary binary.
It then executes the principle payload below a special title, selecting the method’s title to look much less suspicious. The malware is executed by ‘sh’, altering its title from httpd to sh.
This malware positive aspects persistence by self-replicating and utilizing misleading filenames that resemble reliable system information. Perfctl copies itself to a number of places on the disk, guaranteeing its survival even after system restarts or cleanups.
Perfctl’s major objective is cryptomining, utilizing contaminated programs for cryptocurrency era. It has additionally been noticed partaking in proxy-jacking, and hijacking server sources for malicious functions. Perfctl makes an attempt to take advantage of the Polkit vulnerability (CVE-2021-4043) to realize root privileges, granting it larger entry and management over the system.
“Given the scale, we strongly believe the attackers targeted millions worldwide with a potential number of victims of thousands, it appears that with this malware any Linux server could be at risk.”
Aqua Nautilus
Perfctl’s rootkit and evasion methods make detection difficult, whereas its misleading filenames and behavior could make it seem reliable. Its dynamic behaviour also can hinder detection efforts.
To guard your Linux programs from Perfctl, commonly replace your working system and software program with the most recent safety patches, conduct vulnerability assessments, implement strong community safety measures like firewalls and intrusion detection programs, monitor system exercise for uncommon behaviour, and use safety instruments like endpoint safety options.