A comparatively new malware known as Latrodectus is believed to be an evolution of the IcedID loader, seen in malicious e-mail campaigns since November 2023.
The malware was noticed by researchers at Proofpoint and Group Cymru, who labored collectively to doc its capabilities, that are nonetheless unstable and experimental.
IcedID is a malware household first recognized in 2017 that was initially labeled as a modular banking trojan designed to steal monetary info from contaminated computer systems. Over time, it grew to become extra refined, including evasion and command execution capabilities.
Lately, it has acted as a loader that may ship different varieties of malware, together with ransomware, onto contaminated programs.
Beginning in 2022, a number of IcedID campaigns demonstrated diversified supply techniques, however the major distribution methodology remained malicious emails. In late 2022, new variants of the malware have been utilized in assaults, which experimented with varied evasion tips and new assault units.
In February 2024, one of many leaders behind the IcedID operation pleaded responsible in the USA, going through 40 years of imprisonment.
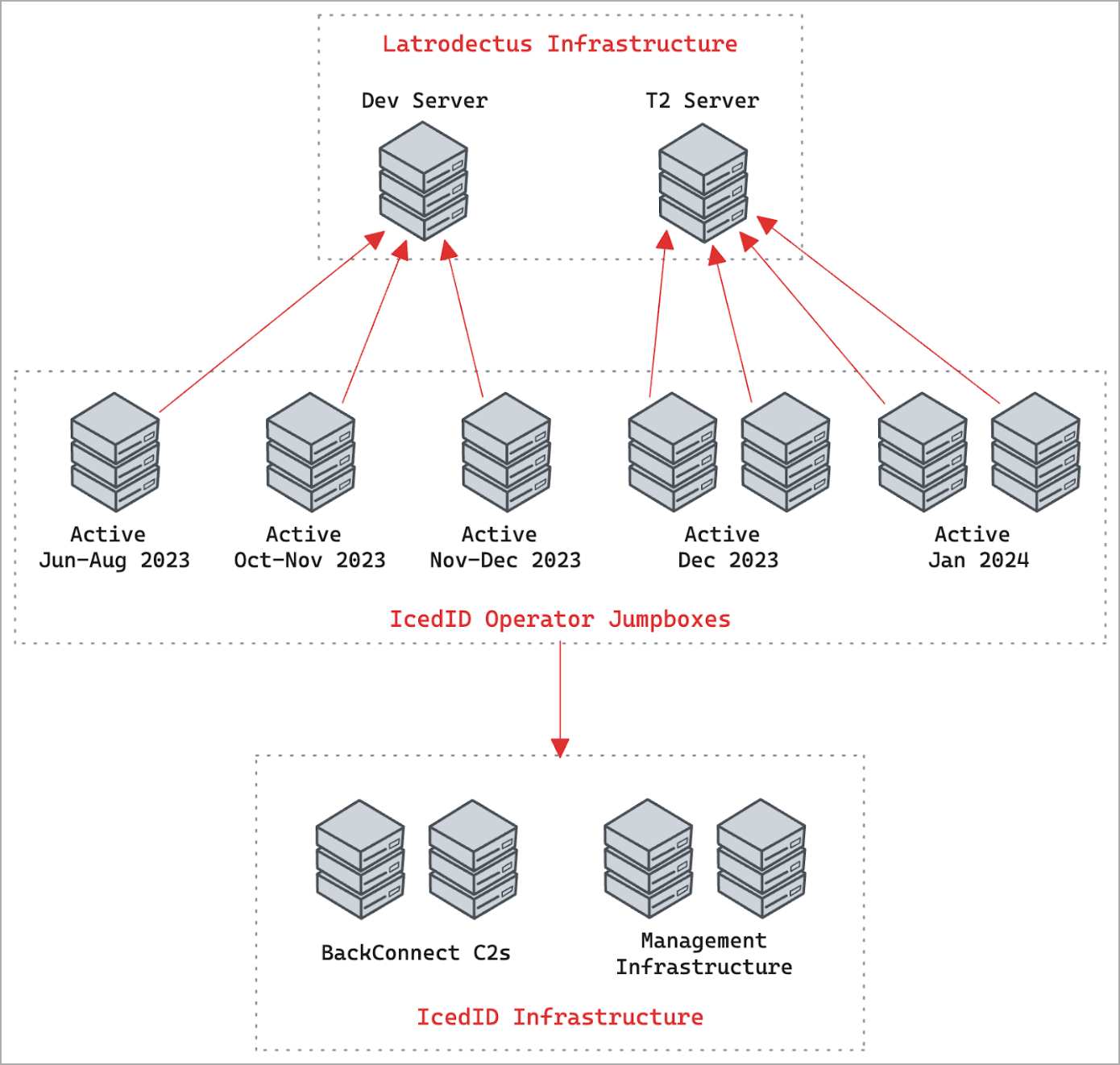
Researchers from Proofpoint and Group Cymru now imagine that the builders of IcedID created Latrodectus after noting they shared infrastructure and operational overlaps.
Whether or not Latrodectus will finally change IcedID is simply too quickly to inform. Nonetheless, the researchers say that preliminary entry brokers (TA577 and TA578) who beforehand distributed IcedID have now begun to more and more distribute Latrodectus in phishing campaigns.
New Latrodectus malware
Latrodectus was noticed in November 2023, utilized by risk actors tracked as TA577 and TA578, with a notable enhance in noticed deployments in February and March 2024.
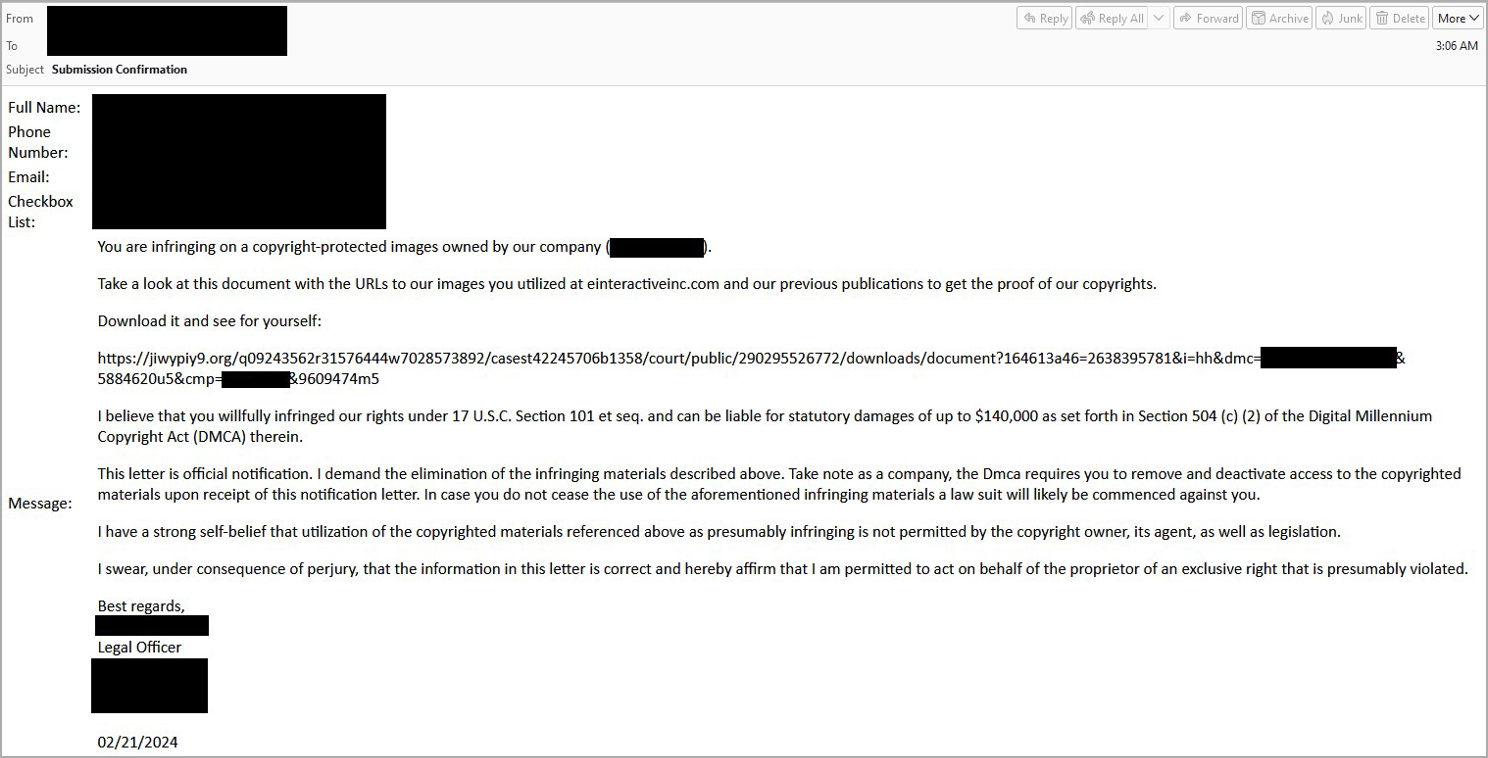
The risk actor initiates the assault by filling out on-line contact kinds to ship pretend copyright infringement notices to the focused organizations.
BleepingComputer beforehand reported on related campaigns in the previous, and for website house owners unfamiliar with this phishing assault, they are often tense to obtain and should scare recipients into clicking on embedded hyperlinks.
The hyperlink within the newest campaigns takes the sufferer to a Google Firebase URL that drops a JavaScript file. When executed, the JS file makes use of Home windows installer (MSIEXEC) to run an MSI file from a WebDAV share, which incorporates the Latrodecturs DLL payload.
In contrast to its predecessor, IcedID, Latrodectus performs varied sandbox evasion checks earlier than operating on the machine to keep away from detection and evaluation by safety researchers.
The checks embrace:
- If Home windows 10 or newer, have a minimum of 75 operating processes
- If sooner than Home windows 10, have a minimum of 50 operating processes
- Make sure the 64-bit utility is operating on a 64-bit host
- Make sure the host has a sound MAC tackle
After the required surroundings and mutex checks, the malware initializes by sending a sufferer registration report back to its operators.
Latrodectus is a downloader able to retrieving additional malicious payloads primarily based on directions obtained from a command and management (C2) server.
The instructions Latrodectus helps are the next:
- Get the filenames of information on the desktop
- Get the record of operating processes
- Ship further system info
- Execute an executable file
- Execute a DLL with a given export
- Go a string to cmd and execute it
- Replace the bot and set off a restart
- Shutdown the operating course of
- Obtain “bp.dat” and execute it
- Set a flag to reset the timing of the communications
- Reset the counter variable utilized in communications
The malware’s infrastructure is separated into two distinct tiers that comply with a dynamic operation strategy relating to marketing campaign involvement and lifespan, with most new C2 coming on-line in the direction of the top of the week earlier than the assaults.
Proofpoint concludes with a warning about Latrodectus, estimating a excessive likelihood of the malware getting used sooner or later by a number of risk actors who beforehand distributed IcedID.
