A brand new malware risk named Latrodectus has emerged, bypassing detection strategies and linked to the builders behind IcedID. This downloader malware empowers cybercriminals (together with notorious actors like TA577 and TA588) to breach programs and deploy varied malicious payloads.
Cybersecurity researchers at Proofpoint have recognized a brand new malware risk dubbed “Latrodectus.” First noticed in November 2023, Latrodectus is a downloader malware utilized by cybercriminals to realize preliminary entry to sufferer programs and deploy additional malicious payloads.
This malware poses a significant risk resulting from its potential to evade detection strategies generally employed in sandboxes, that are safety environments used to research suspicious code.
Latrodectus: A New Participant with Acquainted Traits
Preliminary evaluation instructed Latrodectus is likely to be a variant of the infamous IcedID malware. Nevertheless, additional investigation revealed it to be a completely new pressure, seemingly created by the identical builders behind IcedID. This connection is supported by shared infrastructure and code traits.
Preliminary Entry Brokers Leverage Latrodectus
Proofpoint report shared with Hackread.com on Thursday 04, 2024 forward of publication on Tuesday attributes Latrodectus to 2 particular risk actors: TA577 and TA578. It’s value mentioning that TA578 is understood for delivering malware threats like BazaLoader, Cobalt Strike, Ursnif, and KPOT Stealer.
However, TA577 is notorious for having served as a key affiliate of the Qbot community till its latest disruption. TA577 has been linked by Proofpoint to numerous campaigns, with subsequent ransomware infections reminiscent of Black Basta being notably attributed to them.
These actors are categorised as Preliminary Entry Brokers (IABs), specializing in gaining preliminary footholds inside sufferer networks. Latrodectus serves as their instrument to ascertain a foothold and probably deploy ransomware or different malicious instruments.
Commenting on this, Ken Dunham, Cyber Menace Director at Qualys Menace Analysis Unit instructed Hackread.com, “Battling eCrime is just like transferring a sofa the place roaches dwell, they merely run to a different piece of furnishings or room close by to hunt harbour and proceed enterprise as regular, regardless of any actions taken by the house owner.“
“Latrodectus has highly effective elements upon its emergence, able to defeating sandboxes, use of RC4 encrypted command and management communications, and extra,“ Ken warned. “It seems seemingly that actors behind QBot felt the warmth from takedowns final 12 months, migrating to this new code base and infrastructure within the fall of 2023.“
Whereas Latrodectus exercise dropped in December 2023 and January 2024, Proofpoint stories a surge in campaigns all through February and March 2024. This means a rising adoption of Latrodectus by cybercriminals.
The particular payloads delivered by Latrodectus stay unknown, however its downloader performance permits attackers to deploy a variety of instruments by way of malicious emails relying on their aims.
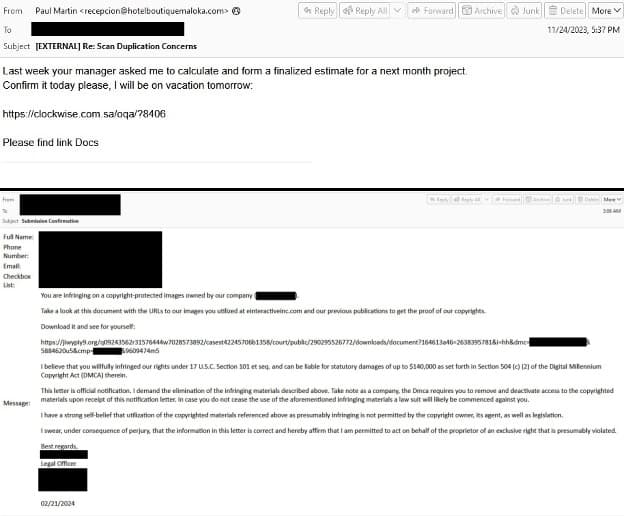
Whereas technical particulars of Latrodectus’s modus operandi can be found in Proofpoint’s weblog submit, listed below are some to mitigate the chance of Latrodectus:
- Preserve sturdy cybersecurity hygiene: Repeatedly replace software program and firmware on all units. Make the most of sturdy safety options with superior malware detection capabilities.
- Be cautious of suspicious emails: Phishing emails are a typical methodology for distributing malware. Be cautious of unsolicited attachments and hyperlinks.
- Educate staff: Practice staff on cybersecurity finest practices, together with electronic mail safety consciousness and the significance of reporting suspicious exercise.
