Roughly 16,500 Ivanti Join Safe and Poly Safe gateways uncovered on the web are possible susceptible to a distant code execution (RCE) flaw the seller addressed earlier this week.
The flaw is tracked as CVE-2024-21894 and is a high-severity heap overflow within the IPSec part of Ivanti Join Safe 9.x and 22.x, doubtlessly permitting unauthenticated customers to trigger denial of service (DoS) or obtain RCE by sending specifically crafted requests.
Upon disclosure, on April 3, 2024, the web search engine Shodan confirmed 29,000 internet-exposed situations, whereas risk monitoring service Shadowserver reported seeing roughly 18,000.
On the time, Ivanti acknowledged that it had seen no indicators of energetic exploitation in any of its prospects however urged system directors to use the updates as quickly as doable.
Two days later, Shadowserver added CVE-2024-21894 into its scanning capabilities, reporting that about 16,500 situations are susceptible to the RCE flaw.
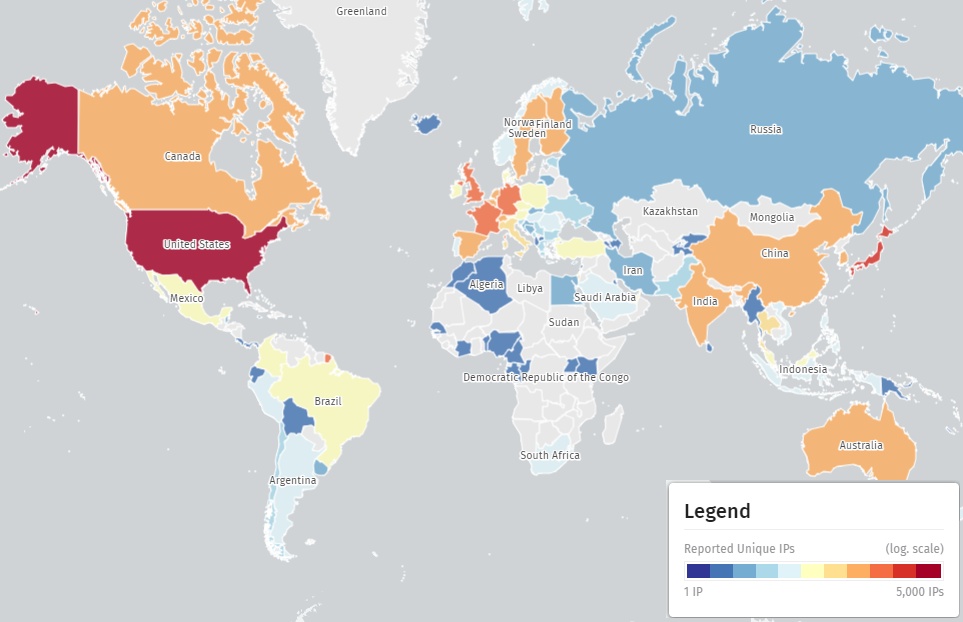
Most of these situations (4,700) are in the US, with Japan (2,000), the UK (1,000), Germany (900), France (900), China (500), the Netherlands (500), Spain (500), Canada (330), India (330), and Sweden (320) following with important stage of publicity too.
Excessive-risk vulnerabilities in Ivanti merchandise typically act as a degree of breach for organizations worldwide.
Earlier this 12 months, it was revealed that state-sponsored risk actors leveraged a number of flaws in Ivanti merchandise, particularly CVE-2023-46805, CVE-2024-21887, CVE-2024-22024, and CVE-2024-21893, whereas they had been zero-days, that means the seller did not know in regards to the flaws and no fixes had been out there.
This exercise was adopted by a number of hacking teams exploiting widespread exploitation to deploy customized internet shells to backdoor units.
A report revealed right this moment by Mandiant dives deeper into high-profile current bug exploitation circumstances concentrating on Ivanti endpoints, specializing in Chinese language hackers from 5 distinct exercise clusters and a malware household named ‘SPAWN’ utilized in these assaults.
System directors who haven’t utilized the out there mitigations and fixes for CVE-2024-21894 are suggested to observe the seller’s directions on this data base article.
