SlashNext researchers have found a brand new, refined phishing software GoIssue focusing on GitHub builders. Find out about its capabilities, the influence in case of profitable assaults, and the best way to defend your self from this rising menace.
Cybersecurity researchers at SlashNext have recognized a brand new menace known as GoIssue. This superior software, presumably linked to the GitLoker extortion marketing campaign, allows attackers to hold out large-scale phishing assaults aimed toward GitHub customers.
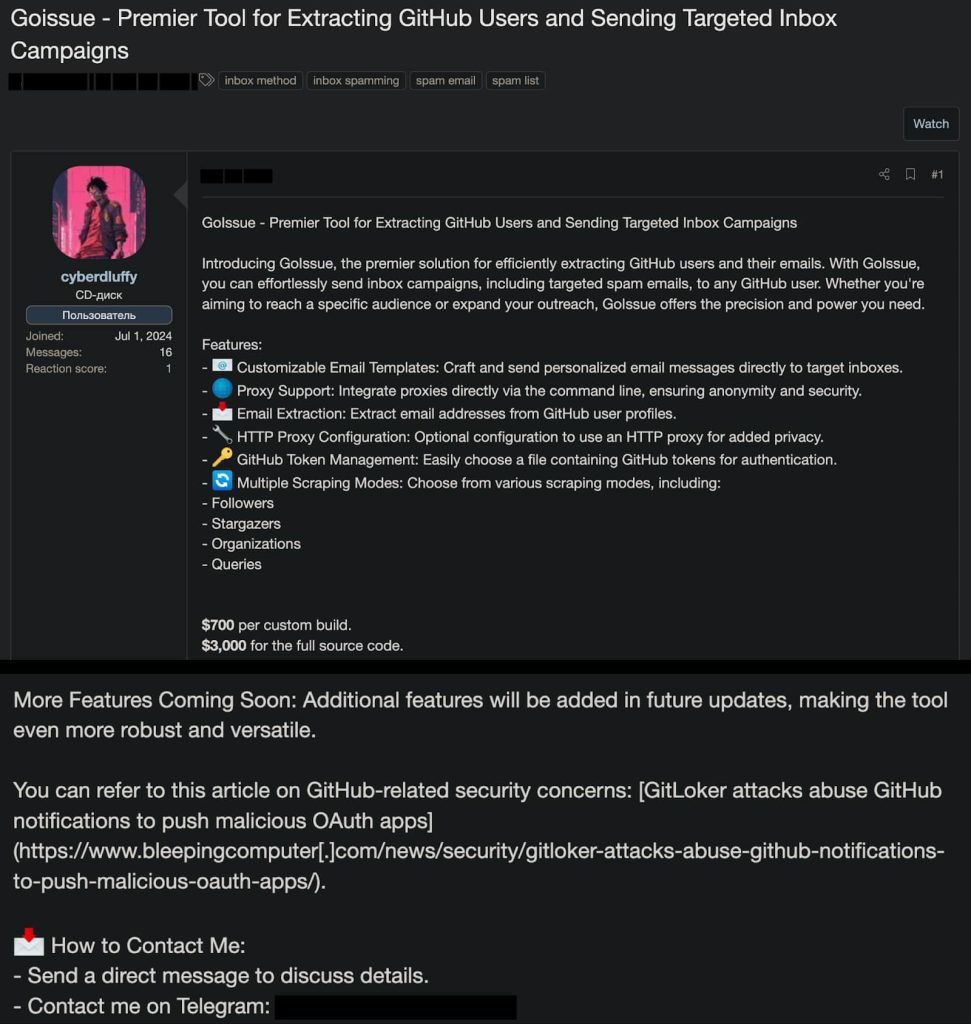
Based on SlashNext’s investigation, shared with Hackread.com forward of publishing on Tuesday, GoIssue may also harvest e mail addresses from public GitHub profiles.
“At its core, the tool systematically harvests email addresses from public GitHub profiles, using automated processes and GitHub tokens to collect data based on various criteria – from organization memberships to stargazer lists,” the weblog submit learn.
GoIssue is priced at $700 for a customized construct or $3,000 for full supply code entry. The attackers can use it to execute complicated, focused campaigns in opposition to the GitHub developer group. They’ll harvest e mail addresses from public profiles and use them in mass phishing campaigns utilizing faux notifications.
This implies the influence of GoIssue-powered assaults might be broad. These campaigns may result in a phishing web page, malware obtain, or a rogue OAuth app authorization immediate, granting entry to non-public repositories and information.
Not solely can particular person builders be compromised, however complete organizations may be in danger. Profitable assaults may result in supply code theft, provide chain assaults, and company community breaches.
Based on SlashNext’s report, Cyberluffy, a member of the GitLoker Staff, has been linked to the GoIssue software, which is believed to be an extension of the GitLoker marketing campaign. The connection between GoIssue and the GitLoker marketing campaign is a trigger for critical concern. Each instruments share a standard goal and make use of related ways, suggesting a possible collaboration or evolution of the identical menace actor.
The Gitloker marketing campaign refers to a current sequence of cyberattacks focusing on GitHub customers, primarily centered on extortion. The attackers, often called “Gitloker” on Telegram, used numerous strategies, together with phishing assaults, to compromise consumer accounts and delicate information.
GitHub customers ought to undertake finest on-line safety practices, resembling robust password hygiene, enabling Two-Issue Authentication (2FA), being cautious of phishing emails, and recurrently reviewing OAuth app permissions and revocation of pointless ones.
These measures assist defend in opposition to potential compromises and make sure the security of all customers, together with GitHub. By understanding the capabilities of GoIssue and the ways employed by attackers, builders can take the mandatory steps to guard themselves and their organizations from doable harm.
Jason Soroko, Senior Fellow at Sectigo weighed in on the scenario calling out GoIssue as a significant menace to not solely GitHub however different developer platforms as nicely.
“The emergence of GoIssue indicators a brand new period the place developer platforms turn out to be high-stakes battlegrounds, and safety defences should evolve quickly to counteract this pervasive menace,“ defined Jason.
“By automating e mail tackle harvesting and executing large-scale, personalized phishing campaigns, this software allows attackers to take advantage of trusted developer environments,“ he warned. “As standard, the attacker’s purpose is credential theft utilizing OAuth-based repository hijacks. The unhealthy guys know what they’re doing. It is a high-impact assault mechanism that particularly preys on the belief and openness of the developer group.“