Attackers are focusing on GitHub repositories, wiping their contents, and asking the victims to achieve out on Telegram for extra info.
These assaults are a part of what appears like an ongoing marketing campaign first noticed on Wednesday by Germán Fernández, a safety researcher at Chilean cybersecurity firm CronUp.
The menace actor behind this marketing campaign—who has the Gitloker deal with on Telegram and is posing as a cyber incident analyst—is probably going compromising targets’ GitHub accounts utilizing stolen credentials.
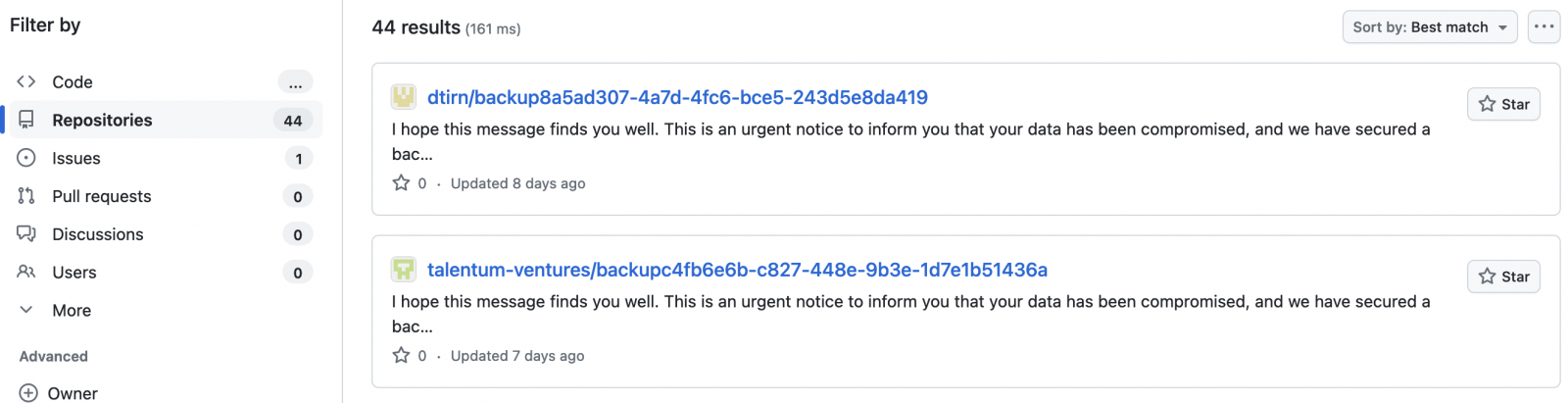
Subsequently, they declare to steal the victims’ information, making a backup that would assist restore the deleted information. They then rename the repository and add a single README.me file, instructing the victims to achieve out on Telegram.
“I hope this message finds you well. This is an urgent notice to inform you that your data has been compromised, and we have secured a backup,” the ransom notes learn.
When BleepingComputer contacted GitHub earlier right this moment for extra particulars relating to the Gitloker extortion marketing campaign, a spokesperson was not instantly accessible for remark.
After earlier assaults in opposition to GitHub customers, the corporate suggested customers to alter their passwords to safe their accounts in opposition to unauthorized entry. This could shield in opposition to malicious actions resembling including new SSH keys, authorizing new apps, or modifying crew members.
To forestall attackers from compromising your GitHub account and detect suspicious exercise, you must also:
- Allow two-factor authentication.
- Add a passkey for safe, passwordless login.
- Evaluate and revoke unauthorized entry to SSH keys, deploy keys, and approved integrations.
- Confirm all e mail addresses related together with your account.
- Evaluate account safety logs to trace repository adjustments.
- Handle webhooks in your repositories.
- Examine for and revoke any new deploy keys.
- Commonly evaluate current commits and collaborators for every repository.
Generally focused in information theft assaults
This is not the primary time GitHub accounts have been compromised to steal information from customers’ personal repositories.
Round March 2020, hackers additionally compromised the account of Microsoft, the developer platform’s mother or father firm since June 2018, stealing greater than 500GB price of recordsdata from Redmond’s personal repositories.
Whereas the stolen recordsdata contained principally code samples, check tasks, and different generic gadgets (nothing important for Microsoft to fret about), safety consultants have been involved that personal API keys or passwords may need additionally unintentionally been uncovered within the breach.
A now-notorious menace actor often called ShinyHunters additionally confirmed the inconsequential nature of the stolen information by leaking it on a hacker discussion board without cost after first planning to promote the stolen recordsdata to the very best bidder.
In September 2020, GitHub warned of a phishing marketing campaign focusing on customers to compromise their accounts. The marketing campaign used emails pushing faux CircleCI notifications to steal their GitHub credentials and two-factor authentication (2FA) codes by relaying them by means of reverse proxies.
GitHub mentioned that the attackers virtually instantly started exfiltrating information from victims’ personal repositories after the compromise, including new person accounts to the organizations to take care of persistence if it used administration permissions.
