A new Microsoft 365 phishing-as-a-service platform referred to as “FlowerStorm” is rising in recognition, filling the void left behind by the sudden shutdown of the Rockstar2FA cybercrime service.
First documented by Trustwave in late November 2024, Rockstar2FA operated as a PhaaS platform facilitating large-scale adversary-in-the-middle (AiTM) assaults focusing on Microsoft 365 credentials.
The service provided superior evasion mechanisms, a user-friendly panel, and quite a few phishing choices, promoting cybercriminals entry for $200/two weeks.
In accordance with Sophos researchers Sean Gallagher and Mark Parsons, Rockstar2FA suffered from a partial infrastructure collapse on November 11, 2024, making lots of the service’s pages unreachable.
Sophos says this doesn’t look like the results of regulation enforcement motion in opposition to the cybercrime platform however reasonably a technical failure.
Just a few weeks later, FlowerStorm, which first appeared on-line in June 2024, began shortly gaining traction.
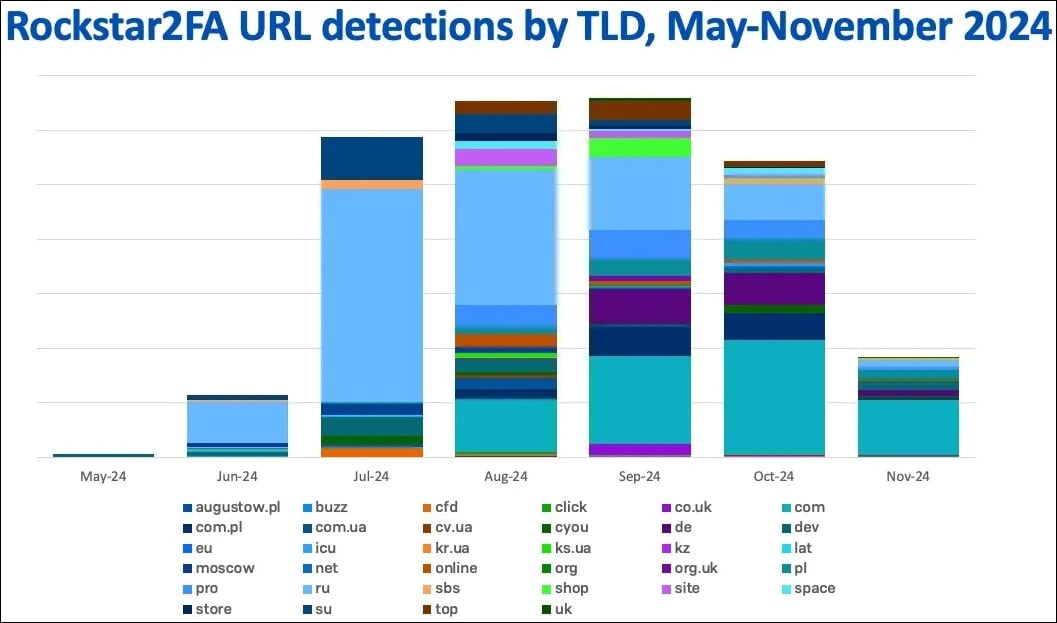
Supply: Sophos
A potential rebrand of Rockstar2FA?
Sophos has discovered that the brand new service, FlowerStorm PhaaS, shares many options beforehand seen in Rockstar2FA, so it’s potential that operators rebranded beneath a brand new title to cut back publicity.
Sophos recognized a number of similarities between Rockstar2FA and FlowerStorm, suggesting a shared ancestry or operational overlap:
- Each platforms use phishing portals mimicking reputable login pages (e.g., Microsoft) to reap credentials and MFA tokens, counting on backend servers hosted on domains like .ru and .com. Rockstar2FA used randomized PHP scripts, whereas FlowerStorm standardized with subsequent.php.
- The HTML construction of their phishing pages is very related, that includes random textual content in feedback, Cloudflare “turnstile” security measures, and prompts like “Initializing browser security protocols.” Rockstar2FA used automotive themes, whereas FlowerStorm shifted to botanical themes, however the underlying design stays constant.
- Credential harvesting strategies align intently, utilizing fields like e-mail, cross, and session monitoring tokens. Each platforms help e-mail validation and MFA authentication by their backend programs.
- Area registration and internet hosting patterns overlap considerably, with heavy use of .ru and .com domains and Cloudflare companies. Their exercise patterns confirmed synchronized rises and falls by late 2024, indicating potential coordination.
- The 2 platforms made operational errors that uncovered backend programs and demonstrated excessive scalability. Rockstar2FA managed over 2,000 domains, whereas FlowerStorm quickly expanded after Rockstar2FA’s collapse, suggesting a shared framework.
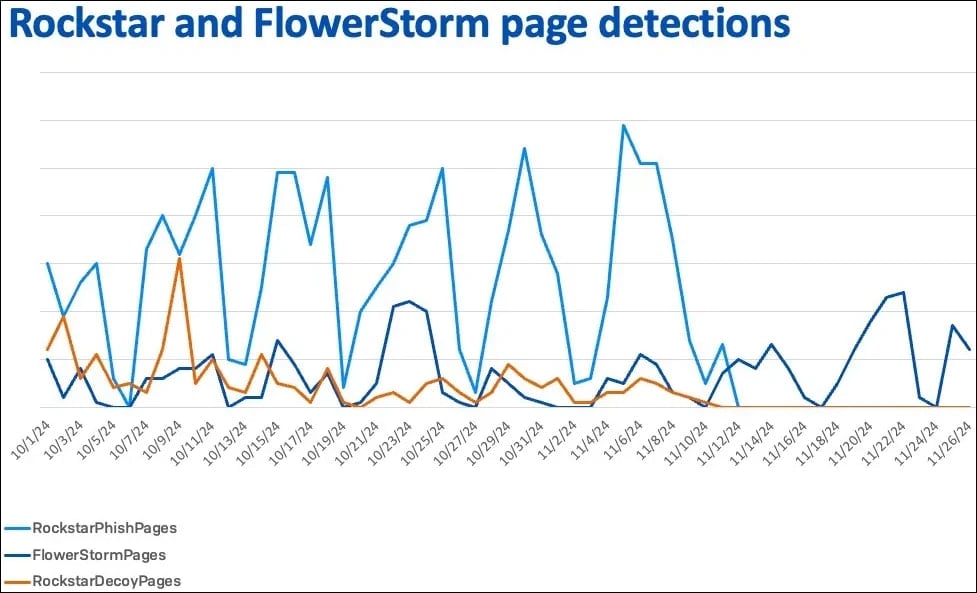
Supply: Sophos
“We cannot with high confidence link Rockstar2FA and FlowerStorm, other than to note that the kits reflect a common ancestry at a minimum due to the similar contents of the kits deployed,” concludes Sophos.
“The similar patterns of domain registration could be a reflection of FlowerStorm and Rockstar working in coordination, though it is also possible that these matching patterns were driven by market forces more than the platforms themselves.”
A brand new hazard rises
Regardless of the story is behind FlowerStorm’s sudden rise, for customers and organizations, it is one more enabler of damaging phishing assaults that might result in full-blown cyberattacks.
Sophos’ telemetry exhibits that roughly 63% of the organizations and 84% of customers focused by FlowerStorm are primarily based in the US.
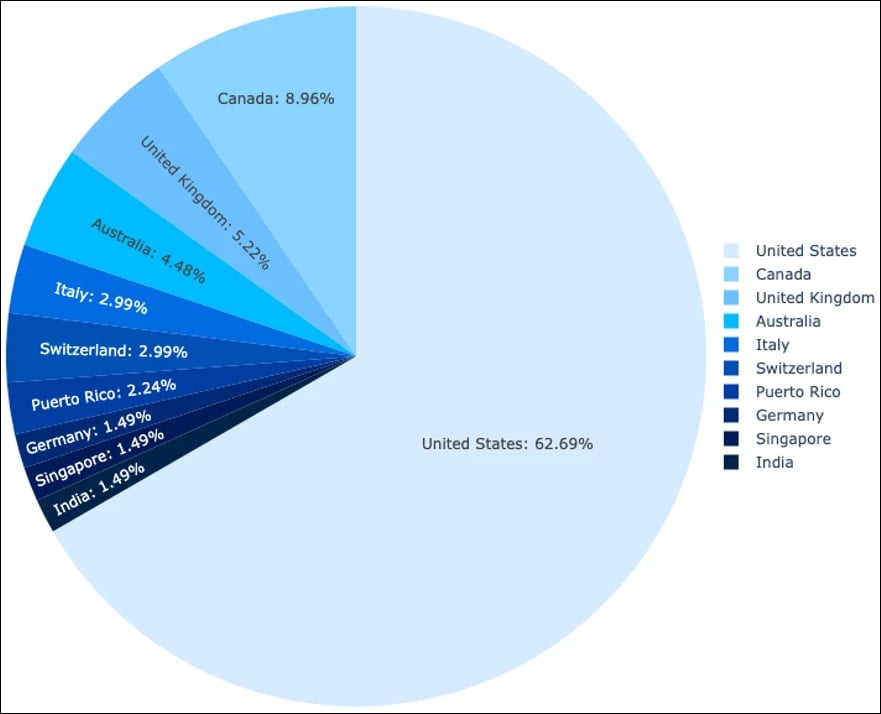
Supply: Sophos
Essentially the most focused sectors are companies (33%), manufacturing (21%), retail (12%), and monetary companies (8%).
To guard in opposition to phishing assaults, use multi-factor authentication (MFA) with AiTM-resistant FIDO2 tokens, deploy e-mail filtering options, and use DNS filtering to dam entry to suspicious domains like .ru, .moscow, and .dev.