A brand new vulnerability has been found that might enable an attacker to take advantage of a race situation inside GitHub’s repository creation and username renaming operations. This method may very well be used to carry out a Repojacking assault (hijacking fashionable repositories to distribute malicious code). This discovering marks the fourth time a novel methodology was recognized that might probably bypass GitHub’s “Popular repository namespace retirement” mechanism. The vulnerability has been reported to GitHub and has been fastened.
Key Findings
- A novel vulnerability was found, exploiting a race situation between the processes of making a repository and renaming a username on GitHub.
- Profitable exploitation of this vulnerability impacts the open-source neighborhood by enabling the hijacking of over 4,000 code packages in languages equivalent to Go, PHP, and Swift, in addition to GitHub actions. Notably, tons of of those packages have garnered over 1,000 stars, amplifying the potential impression on hundreds of thousands of customers and a myriad of purposes.
- The vulnerability has been responsibly disclosed to GitHub, which has subsequently issued a repair.
What’s Repojacking?
Repojacking is a method the place an attacker takes management of a GitHub repository by exploiting a logical flaw that renders renamed customers susceptible.
The attacker hijacks a reliable, typically fashionable, namespace on GitHub. A namespace is the mixture of the username and repo title, for instance:
example-user/example-repo
A namespace turns into probably susceptible to Repojacking when the unique username is modified utilizing GitHub’s “user rename” function.
The change of username course of is fast and simple. A warning lets you already know that each one site visitors for the previous repository’s URL will likely be redirected to the brand new one.
In its documentation for this function, GitHub mentions an vital implication:
“After changing your username, your old username becomes available for anyone else to claim.”
As soon as the username is renamed, an attacker can declare the previous username, open a repo beneath the matching repo title, and hijack the namespace.
The “retired” Namespace Safety
To mitigate this probably dangerous conduct, GitHub put in place the “popular repository namespace retirement”safety measure: any repository with greater than 100 clones on the time its consumer account is renamed is taken into account “retired” and can’t be utilized by others.
To make clear: what is taken into account “retired’ is the namespace, which means the mixture of the username and the repository title.
For instance, let’s take the repository named “repo” of the username “account-takeover-victim.”
This repository was lately cloned 100 instances, which qualifies it for the favored repository namespace retirement.
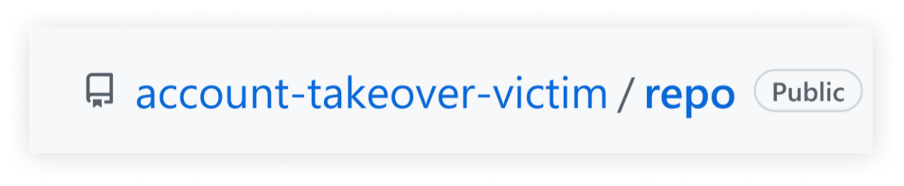
At this level, the account’s proprietor decides to rename the username to whichever title they select.
The sensible results of that is that the username “account-takeover-victim” can now be claimed by anybody.
Nevertheless, as soon as the brand new proprietor of this username tries to open a brand new repository beneath the title “repo,” they are going to be blocked and get the next message:
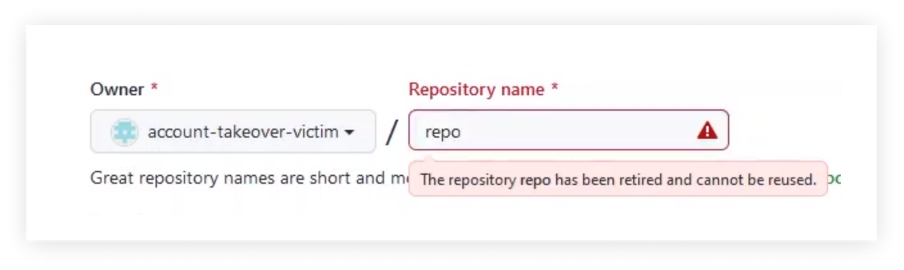
This fashion, the previous username is on the market for anybody to assert, however as soon as this new username proprietor tries to create a brand new repository with a “retired” title, GitHub blocks this try.
Influence
Profitable exploitation permits the takeover of fashionable code packages in a number of package deal managers, together with “Packagist,” “Go,” “Swift,” and extra. We’ve got recognized over 4,000 packages in these package deal managers utilizing renamed usernames and are liable to being susceptible to this system in case a brand new bypass is discovered. Of those packages in danger, tons of of them have garnered over 1,000 stars on GitHub.
As well as, exploiting this bypass also can lead to a takeover of fashionable GitHub actions, that are additionally consumed by specifying a GitHub namespace. Poisoning a preferred GitHub motion may result in main Provide Chain assaults with important repercussions.
Latest analysis by Aqua has revealed that organizations as giant as Google and Lyft have been susceptible to this type of assault. This underscores the crucial nature of the vulnerability, because it may probably impression a number of the greatest gamers within the tech trade, who’ve promptly mitigated the dangers after being notified.
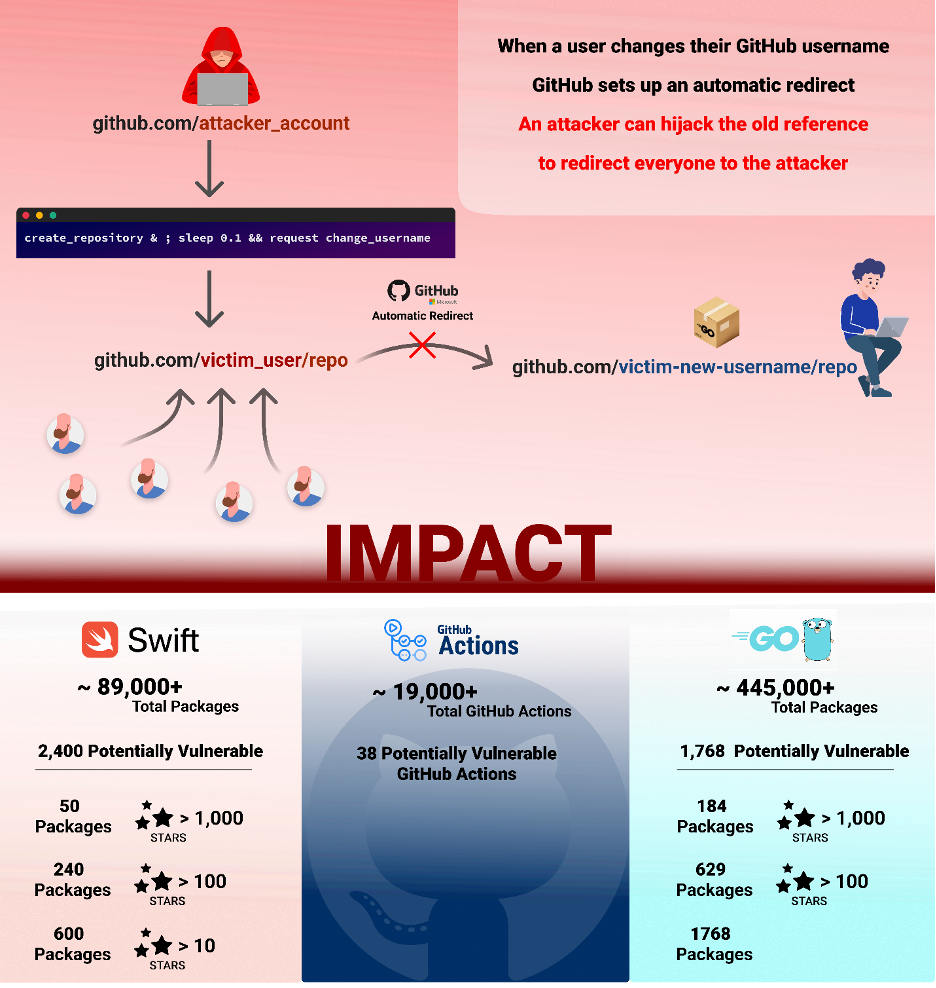
New Exploitation Technique Bypassing the Retired Namespace Safety
The brand new exploitation methodology takes benefit of a possible race situation between the creation of a repository and the renaming of a username. Checkmarx SCS Group Architect, Elad Rapoport, has been capable of reveal how he was capable of bypass GitHub checks by nearly concurrently making a repository and altering the username.
The steps to breed this exploit are as follows:
- Sufferer owns the namespace “victim_user/repo”
- Sufferer renames “victim_user” to “renamed_user.”
- The “victim_user/repo” repository is now retired.
- An attacker who owned the username “attacker_user” prepares a command which virtually concurrently creates a repo known as “repo” and renames the username “attacker_user” to the victims additionally username, “victim_user”. That is completed utilizing an API request for repository creation and a renamed request interception for the username change.
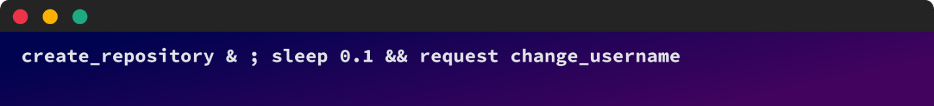
An instance of the pseudo-exploitation command
This discovery marks the fourth time an alternate methodology has been recognized for performing Repojacking. Checkmarx recognized and reported bypasses to the “Popular repository namespace retirement” mechanism twice in 2022, each of which GitHub fastened.
Joren Vrancken, an exterior researcher, discovered a 3rd bypass of this mechanism in 2022, which GitHub additionally addressed and stuck.
What are you able to do?
We advocate avoiding utilizing retired namespaces to attenuate the assault floor and guaranteeing that there are not any dependencies in your code that result in a GitHub repository susceptible to RepoJacking.
Moreover, think about using ChainJacking (https://github.com/Checkmarx/chainjacking) which is an open-source mission developed by Checkmarx, designed that can assist you understand if any of your Go lang direct GitHub dependencies is prone to the RepoJacking assault.
Timeline
March 1st – 2023 – Checkmarx discovers a further vulnerability to bypass the GitHub namespace retirement function and discloses it to GitHub.
Sep 1st – 2023 – GitHub responds that they’ve fastened the bypass.
Conclusion
The invention of this novel vulnerability in GitHub’s repository creation and username renaming operations underlines the persistent dangers related to the “Popular repository namespace retirement” mechanism.
Many GitHub customers, together with customers that management fashionable repositories and packages, select to make use of the “User rename” function GitHub gives. For that cause, the try to bypass the “Popular repository namespace retirement” stays a gorgeous assault level for provide chain attackers with the potential to trigger substantial damages.
Furthermore, it’s fascinating to note that GitHub’s supplied safety is activated based mostly on inside metrics and provides the customers no indication if a specific namespace is protected by it or not. This would possibly depart some repositories and packages unknowingly in danger.
We advocate avoiding utilizing retired namespaces and contemplating utilizing our ChainJacking open-source mission to determine susceptible packages.
Our staff continues to work diligently in figuring out these vulnerabilities to make sure the protection of the open-source neighborhood. This vulnerability has been reported to GitHub.