A brand new “EUCLEAK” flaw present in FIDO gadgets utilizing the Infineon SLE78 safety microcontroller, like Yubico’s YubiKey 5 Collection, permits attackers to extract Elliptic Curve Digital Signature Algorithm (ECDSA) secret keys and clone the FIDO machine.
NinjaLab’s Thomas Roche, who found the flaw and devised the EUCLEAK side-channel assault, notes that the facet channel can retrieve an ECDSA secret key utilizing EM acquisitions.
Nevertheless, the assault requires prolonged bodily entry, specialised tools, and a excessive degree of understanding of electronics and cryptography.
These conditions considerably mitigate the danger, limiting it principally to assaults from extremely subtle, state-sponsored menace actors towards high-value targets. With that mentioned, EUCLEAK isn’t thought-about a menace to common customers, even to those that use theoretically weak gadgets.
In 2021, Roche discovered a side-channel assault that focused Google Titan safety keys, permitting him to extract the ECDSA non-public key and clone the machine.
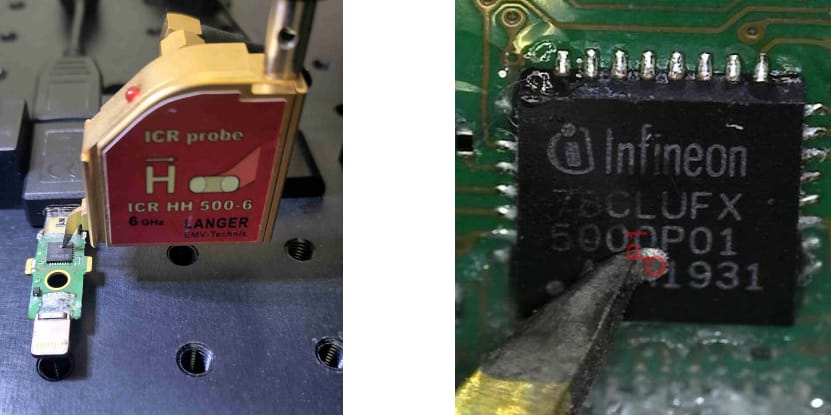
Supply: ninjalab.io
Yubico responds to EUCLEAK
The flaw impacts YubiKey 5 Collection gadgets working firmware variations older than 5.7.0, which makes use of Infineon’s flawed cryptographic library.
The fashions impacted by EUCLEAK are:
- YubiKey 5 Collection variations prior to five.7
- YubiKey 5 FIPS Collection prior to five.7
- YubiKey 5 CSPN Collection prior to five.7
- YubiKey Bio Collection variations prior to five.7.2
- Safety Key Collection all variations prior to five.7
- YubiHSM 2 variations previous to 2.4.0
- YubiHSM 2 FIPS variations previous to 2.4.0
The seller rated the difficulty as reasonable, assigning a CVSS rating of solely 4.9, which displays its low threat.
Additionally, Yubico notes in its advisory that attackers trying to get well credentials from impacted keys would require the consumer PIN or biometric verification for full exploitation, making profitable assaults even tougher.
YubiKey house owners can verify the firmware model of the safety keys utilizing YubiKey Supervisor or YubiKey Authenticator.
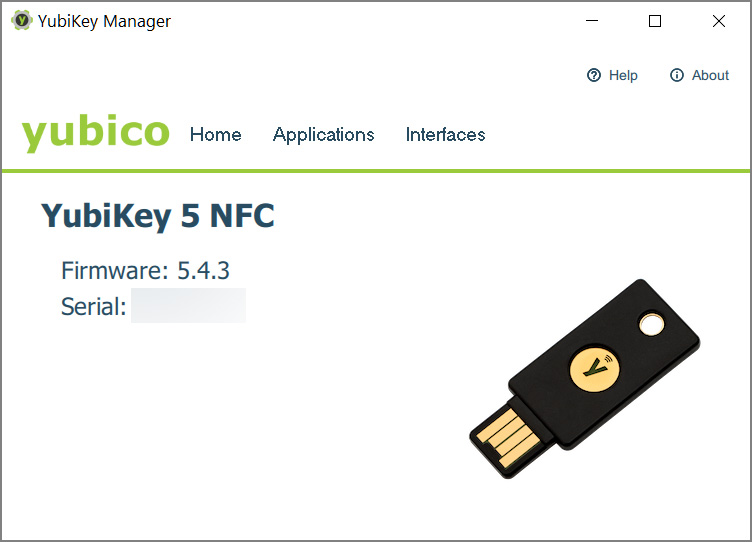
Supply: BleepingComputer
Sadly, if you’re utilizing a weak model, there isn’t any method to improve the firmware to the most recent 5.7.0 (YubiKey) or 2.4.0 (YubiHSM) variations to mitigate this flaw.
The seller recommends utilizing RSA signing keys as an alternative of elliptic curve (ECC) signing keys and limiting the utmost session length from the id supplier settings to require extra frequent FIDO authentications.
Different impacted merchandise
NinjaLab confirmed that EUCLEAK additionally impacts Infineon TPMs (SLB96xx), used for safe boot, authentication, and cryptographic operations, and Infineon’s Optiga Belief M safety microcontroller, utilized in IoT gadgets.
Infineon TPMs are used within the good enclaves of previous (between 2013 and 2018) smartphones and tablets from Samsung and OnePlus, and likewise some dated (from mid-2010s) laptop computer fashions from Lenovo, Acer, Dell, HP, and LG.
The Feitian A22 JavaCard, utilized in good playing cards and authentication techniques, can be impacted by utilizing the Infineon SLE78 microcontroller.
Different probably impacted gadgets embrace e-passports, cryptocurrency {hardware} wallets (chilly wallets), IoT gadgets, and any FIDO machine that makes use of Infineon’s SLE78.
