KEY POINTS
- DroidBot Discovery: A brand new Android spyware and adware, DroidBot, was recognized in mid-2024, working as Malware-as-a-Service (MaaS).
- Targets and Techniques: It targets monetary establishments and customers by disguising itself as safety or banking apps and exploiting Android Accessibility Providers.
- Capabilities: DroidBot can intercept messages, log keystrokes, seize screenshots, and remotely management gadgets.
- Affiliate Community: Utilized by 17 affiliate teams, it has attacked 77 targets throughout Europe, with growth seemingly.
- Prevention Ideas: Keep away from unknown apps, replace gadgets, and use dependable antivirus instruments.
A current discovery by Cleafy Labs has make clear a brand new Android spyware and adware risk dubbed DroidBot, recognized in mid-2024 and operates on the MaaS (Malware-as-a-Service) operation mannequin.
Just like the reputable Software program-as-a-Service (SaaS) mannequin, malware builders lease entry to the malware within the MaaS mannequin, making it simpler for cybercriminals to launch assaults with out requiring superior technical experience.
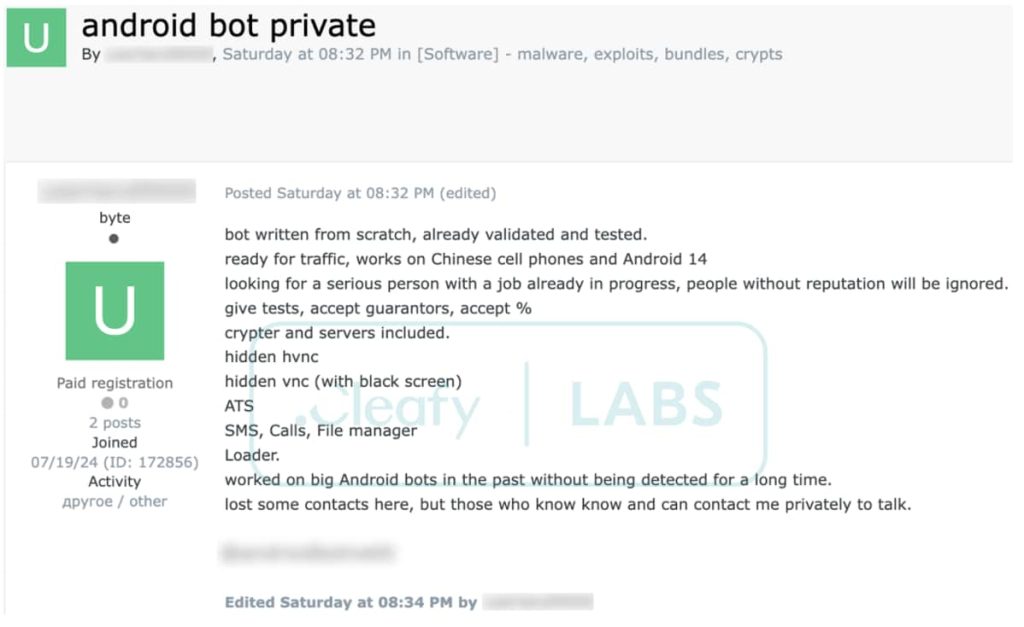
In accordance with Cleafy Labs’ investigation, DroidBot is a complicated Android Distant Entry Trojan (RAT) concentrating on monetary establishments and people throughout Europe. This spyware and adware is believed to have been developed by a Turkish-speaking group and leverages superior strategies to steal delicate data and management contaminated gadgets.
Analysis revealed that DroidBot is designed to focus on a variety of victims, together with banking prospects, cryptocurrency trade customers, and authorities workers. It employs varied ways to compromise gadgets, akin to disguising itself “as generic security applications, Google services, or popular banking apps,” and exploiting the Android Accessibility Providers for its malicious actions.
After infecting your system, DroidBot can intercept SMS messages, log keystrokes, and seize screenshots of the system’s display screen. It may possibly additionally remotely management the system, permitting attackers to make calls, ship messages, and entry delicate information.
This spyware and adware gives a mix of hidden VNC and overlay capabilities with spyware-like options. It features a keylogger and monitoring routines, enabling consumer interception, making it a potent instrument for surveillance and credential theft.
Moreover, DroidBot’s dual-channel communication mechanism permits for outbound information transmission utilizing the MQTT protocol, which was additionally utilized by Copybara and BRATA/AmexTroll banking trojans, and inbound instructions over HTTPS, enhancing its operational flexibility and resilience.
Essentially the most regarding side of DroidBot is that it operates on the MaaS mannequin with 17 distinct affiliate teams recognized every utilizing a novel identifier. This permits cybercriminals to lease entry to the malware, making it simpler for them to launch assaults with out requiring superior technical experience.
“At the time of analysis, 77 distinct targets have been identified, including banking institutions, cryptocurrency exchanges, and national organisations, underscoring its potential for widespread impact,” researchers famous within the weblog put up.
DroidBot is presently in energetic improvement, with some capabilities like root checks being placeholders and options various between samples. Regardless of these inconsistencies, the malware has demonstrated potential, concentrating on customers within the UK, Italy, France, Spain, Turkey, and Portugal, and a possible growth into Latin American areas.
“Within the code, we can see that this information is customised for 4 main languages: English, Italian, Spanish, and Turkish,” Cleafy Labs revealed.
To guard your self from DroidBot and related threats, be cautious when downloading apps from unknown sources, hold your gadgets up to date with the newest safety patches and use dependable antivirus software program.
RELATED TOPICS
- First Cell Crypto Drainer on Google Play Steals $70K
- Adware Present in Google Play Retailer Apps, 2m Downloads
- Google Removes Swing VPN App Uncovered as DDoS Botnet
- Malware contaminated Minecraft modpacks hit Google Play Retailer
- These 8 Apps on Play Retailer Comprise Android/FakeApp Trojan
- 35 malicious apps discovered on Google Play, put in by 2m customers