Replace added to backside of the article.
Hackers are actively exploiting a zero-day vulnerability in Cleo managed file switch software program to breach company networks and conduct information theft assaults.
The flaw is discovered within the firm’s safe file switch merchandise, Cleo LexiCom, VLTrader, and Concord, and is a flaw that permits unrestricted file add and downloads that results in distant code execution.
The Cleo MFT vulnerability impacts variations 5.8.0.21 and earlier and is a bypass for a beforehand fastened flaw, CVE-2024-50623, which Cleo addressed in October 2024. Nevertheless, the repair was incomplete, permitting risk actors to bypass it and proceed to use it in assaults.
Cleo says its software program is utilized by 4,000 corporations worldwide, together with Goal, Walmart, Lowes, CVS, The Dwelling Depot, FedEx, Kroger, Wayfair, Greenback Normal, Victrola, and Duraflame.
These assaults are harking back to earlier Clop information theft assaults that exploited zero-days in managed file switch merchandise, together with the 2023 mass-exploitation of MOVEit Switch, the assaults utilizing a GoAnywhere MFT zero-day, and the December 2020 zero-day exploitation of Accellion FTA servers.
Nevertheless, cybersecurity knowledgeable Kevin Beaumont claims that these Cleo information theft assaults are linked to the brand new Termite ransomware gang, which just lately breached Blue Yonder, a provide chain software program supplier utilized by many corporations worldwide.
“Termite ransomware group operators (and maybe other groups) have a zero day exploit for Cleo LexiCom, VLTransfer, and Harmony,” Beaumont posted to Mastodon.
In-the-wild assaults
The energetic exploitation of Cleo MFT software program was first noticed by Huntress safety researchers, who additionally revealed a proof of idea (PoC) exploit in a brand new write-up warning customers to take pressing motion.
“This vulnerability is being actively exploited in the wild and fully patched systems running 5.8.0.21 are still exploitable,” explains Huntress.
“We strongly recommend you move any internet-exposed Cleo systems behind a firewall until a new patch is released.”
Proof of energetic exploitation of CVE-2024-50623 started on December 3, 2024, with a big uptick within the quantity of assaults noticed on December 8.
Although attribution stays unclear, the assaults are linked to the next IP addresses in the USA, Canada, the Netherlands, Lithuania, and Moldova.
176.123.5.126 - AS 200019 (AlexHost SRL) - Moldova
5.149.249.226 - AS 59711 (HZ Internet hosting Ltd) - Netherlands
185.181.230.103 - AS 60602 (Inovare-Prim SRL) - Moldova
209.127.12.38 - AS 55286 (SERVER-MANIA / B2 Internet Options Inc) - Canada
181.214.147.164 - AS 15440 (UAB Baltnetos komunikacijos) - Lithuania
192.119.99.42 - AS 54290 (HOSTWINDS LLC) - United States
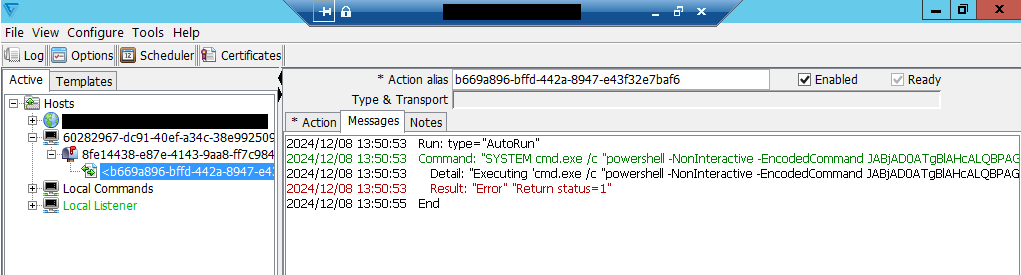
The assaults exploit the Cleo flaw to jot down recordsdata named ‘healthchecktemplate.txt’ or ‘healthcheck.txt’ into the ‘autorun’ listing of the focused endpoints, that are mechanically processed by Cleo software program.
When this occurs, the recordsdata invoke built-in import functionalities to load extra payloads like ZIP recordsdata containing XML configurations (‘primary.xml’), which include PowerShell instructions that will likely be executed.
Supply: Huntress
The PowerShell instructions make callback connections to distant IP addresses, obtain extra JAR payloads, and wipe malicious recordsdata to hinder forensic investigation.
Within the post-exploitation section, Huntress says the attackers use ‘nltest.exe’ to enumerate Lively Listing domains, deploy webshells for persistent distant entry on compromised techniques, and use TCP channels to in the end steal information.
When finished exploiting techniques, the risk actors execute PowerShell instructions to delete recordsdata from the assault, equivalent to ‘C:LexiComcleo.1142.’
Huntress’ telemetry signifies that these assaults have impacted at the very least ten organizations utilizing Cleo software program merchandise, a few of which do enterprise in client merchandise, the meals business, trucking, and transport.
Huntress notes that there are extra potential victims past its visibility, with Shodan web scans returning 390 outcomes for Cleo software program merchandise, The overwhelming majority (298) of weak servers are positioned in the USA.
Yutaka Sejiyama, a risk researcher at Macnica, advised BleepingComputer that his scans return 379 outcomes for Concord, 124 for VLTrader, and 240 for LexiCom.
Motion required
Given the energetic exploitation of CVE-2024-50623 and the ineffectiveness of the present patch (model 5.8.0.21), customers should take fast steps to mitigate the chance of compromise.
Huntress suggests transferring internet-exposed techniques behind a firewall and limiting exterior entry to Cleo techniques.
Firms can examine if their Cleo servers had been compromised by searching for suspicious TXT and XML recordsdata on the directories ‘C:LexiCom,’ ‘C:VLTrader,’ and ‘C:Concord,’ and examine logs for PowerShell command execution.
Malicious XML recordsdata will likely be discovered within the ‘hosts’ folder and include bash (on Linux) or PowerShell (on Home windows) instructions. Cleo has launched scripts for each Linux and Home windows that may assist discover these malicious XML recordsdata.
Lastly, Huntress suggests eradicating any “Cleo####.jar” recordsdata, for instance cleo.5264.jar or cleo.6597.jar) beneath the Concord/VLTrader/Lexicom as they had been possible uploaded through the exploitation of the vulnerability.
Additionally, it is advisable to show off the autorun characteristic by following these steps:
- Open the Cleo software (LexiCom, VLTrader, or Concord)
- Navigate to: Configure > Choices > Different Pane
- Clear the sphere labeled Autorun Listing
- Save the adjustments
Huntress says Cleo expects a brand new safety replace for this flaw to be launched later this week.
BleepingComputer requested Cleo extra questions in regards to the vulnerability and was advised the safety replace was “under development.”
“We have identified a critical vulnerability in instances of Cleo Harmony, VLTrader, and LexiCom products,” Cleo advised BleepingComputer.
“Promptly upon discovering the vulnerability, we launched an investigation with the assistance of outside cybersecurity experts, notified customers of this issue and provided mitigation steps customers should immediately take to address the vulnerability while a patch is under development.”
“Our investigation is ongoing. Customers are encouraged to check Cleo’s security bulletin webpage regularly for updates. Cleo remains focused on supporting its customers and has extended enhanced 24/7 customer support services to those needing additional technical assistance in addressing this vulnerability.”
BleepingComputer contacted Cleo once more to see if there’s a timeframe for when the safety repair will likely be prepared, however has not heard again.
Replace 12/10/24: Added Cleo’s assertion and extra technical info. Additionally fastened incorrect CVE at first of the article.
