KEY SUMMARY POINTS
- Focused Assaults: Subtle spear phishing campaigns are more and more focusing on company executives by way of cell gadgets, utilizing social engineering ways.
- Exploitation of Belief: Attackers mimic reputable providers like DocuSign and Google, leveraging urgency and credibility to deceive victims.
- Superior Strategies: Campaigns use CAPTCHAs, mobile-specific faux login pages, and compromised domains to bypass detection mechanisms.
- Infrastructure Abuse: Attackers make the most of platforms like Cloudflare for SSL encryption and DDoS safety, complicating detection efforts.
- Proactive Protection: Common worker coaching, superior cell gadget administration (MDM) options, and automatic incident response platforms are essential to mitigating these threats.
Cell gadgets have change into a main goal for classy phishing assaults, significantly these geared toward company executives. These focused assaults, often known as spear phishing, leverage social engineering ways to steal priceless credentials and achieve entry to delicate info.
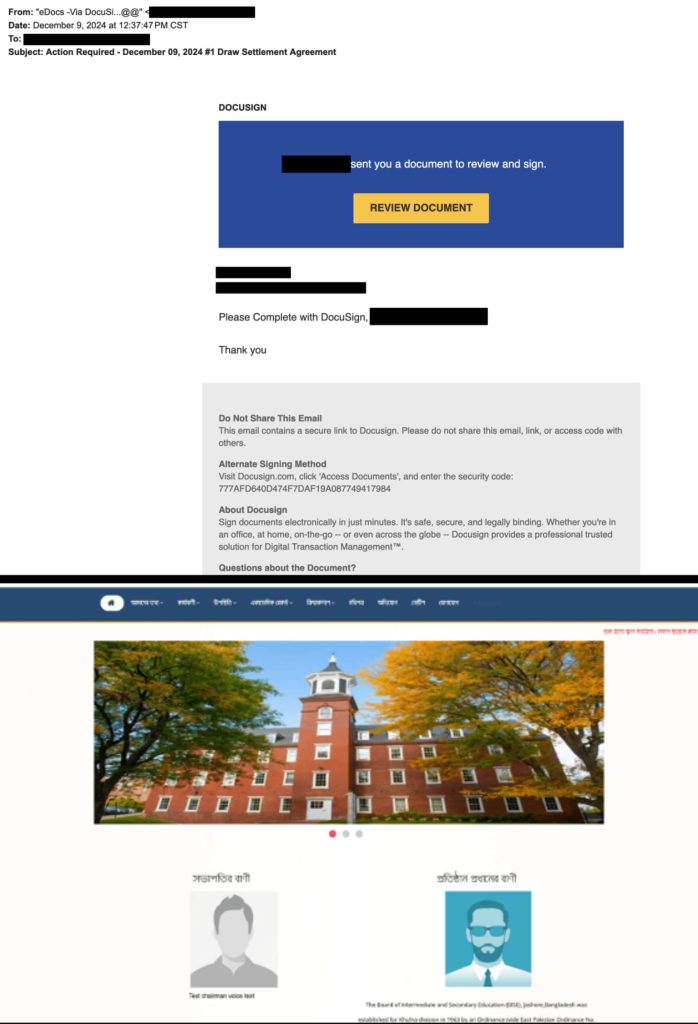
The Phishing and Information Analytics Group at Zimperium uncovered a latest spear phishing marketing campaign focusing on executives. The assault entails utilizing a mimicked reputable DocuSign doc requiring rapid overview, a standard tactic that exploits urgency and authority.
Spear phishing is a well-liked assault vector in opposition to company executives, compromising high-value credentials that grant entry to delicate knowledge and techniques. The assault begins with a seemingly harmless hyperlink disguised as a DocuSign doc. The hyperlink used a reputable area (clickmethryvcom) to masks its origin, and as soon as clicked initiates a sequence of redirects. First, it redirects to a compromised college web site, leveraging its credibility to bypass detection.
Researchers famous that attackers have used CAPTCHAs to forestall automated detection and carried out mobile-specific focusing on. Furthermore, if the hyperlink is accessed by way of a cell gadget, the assault presents a faux Google sign-in web page to steal credentials whereas desktops are redirected to reputable Google websites. One other statement is that the phishing web site (diitalwaveru) and its SSL certificates had been created simply days earlier than the assault, highlighting the attackers’ give attention to speedy deployment.
Additional probing as per Zimperium’s weblog put up, revealed that the attackers had utilized Cloudflare’s infrastructure for DDoS safety, SSL encryption, and quick content material supply, making it tougher to detect. And, along with email-based assaults, the marketing campaign additionally used PDF paperwork containing embedded phishing URLs. These PDFs mimicked reputable DocuSign workflows, bypassing conventional URL scanning and exploiting belief in enterprise paperwork.
The incident highlights the evolving nature of cell phishing assaults, with attackers investing closely in infrastructure to bypass safety controls, focusing on cell gadgets typically missed in safety methods, and exploiting compromised domains for credibility.
Subsequently, it has change into important to conduct common safety consciousness coaching applications to teach workers concerning the newest phishing ways and greatest practices for figuring out and avoiding such assaults. Organizations should additionally deploy superior Cell Gadget Administration (MDM) options to implement safety insurance policies, reminiscent of password complexity, display screen lock timeouts, and distant wipe capabilities.
Mika Aalto, Co-Founder and CEO at Hoxhunt weighed in on the scenario emphasizing the significance of proactive coaching for workers and administration to establish and report phishing assaults, as technical instruments alone could not catch all threats.
“Crucial factor that firms can do is to shift left and equip senior administration and workers with the talents and instruments to acknowledge and safely report a cell phishing (mishing) assault. We are able to hope that technical filters and endpoint detection and response applied sciences shortly develop to have the ability to choose up these extremely obfuscated, native code-based Malware assaults and pinpoint irregular alerts and visitors,“ mentioned Mika.
“In the end, it comes all the way down to folks. Attackers will launch a posh assault with what would possibly simply be a easy phishing message. It’s as much as folks to have the ability to take heed to that little voice of their head that’s telling them that one thing is incorrect and report suspicious messages as a matter of behavior. From there, you wish to have a platform that may mechanically categorize and escalate their experiences to the SOC for accelerated response,“ he defined.
RELATED TOPICS
- 99% of UAE’s .ae Domains Uncovered to Phishing and Spoofing
- Scammers Exploit Faux Domains in Dubai Police Phishing Scams
- Ongoing Phishing Assault Targets Workers Throughout 12 Industries
- Rockstar 2FA Phishing-as-a-Service Equipment Hits Microsoft 365 Accounts
- Xiū gǒu Phishing Equipment Hits UK, US, Japan, Australia Throughout Key Sectors