Safety researchers have found a brand new Android banking trojan they named Brokewell that may seize each occasion on the machine, from touches and knowledge exhibited to textual content enter and the purposes the consumer launches.
The malware is delivered via a pretend Google Chrome replace that’s proven whereas utilizing the online browser. Brokewell is beneath energetic improvement and options a mixture of in depth machine takeover and distant management capabilities.
Brokewell particulars
Researchers at fraud threat firm ThreatFabric discovered Brokewell after investigating a pretend Chrome replace web page that dropped a payload, a standard methodology for tricking unsuspecting customers into putting in malware.
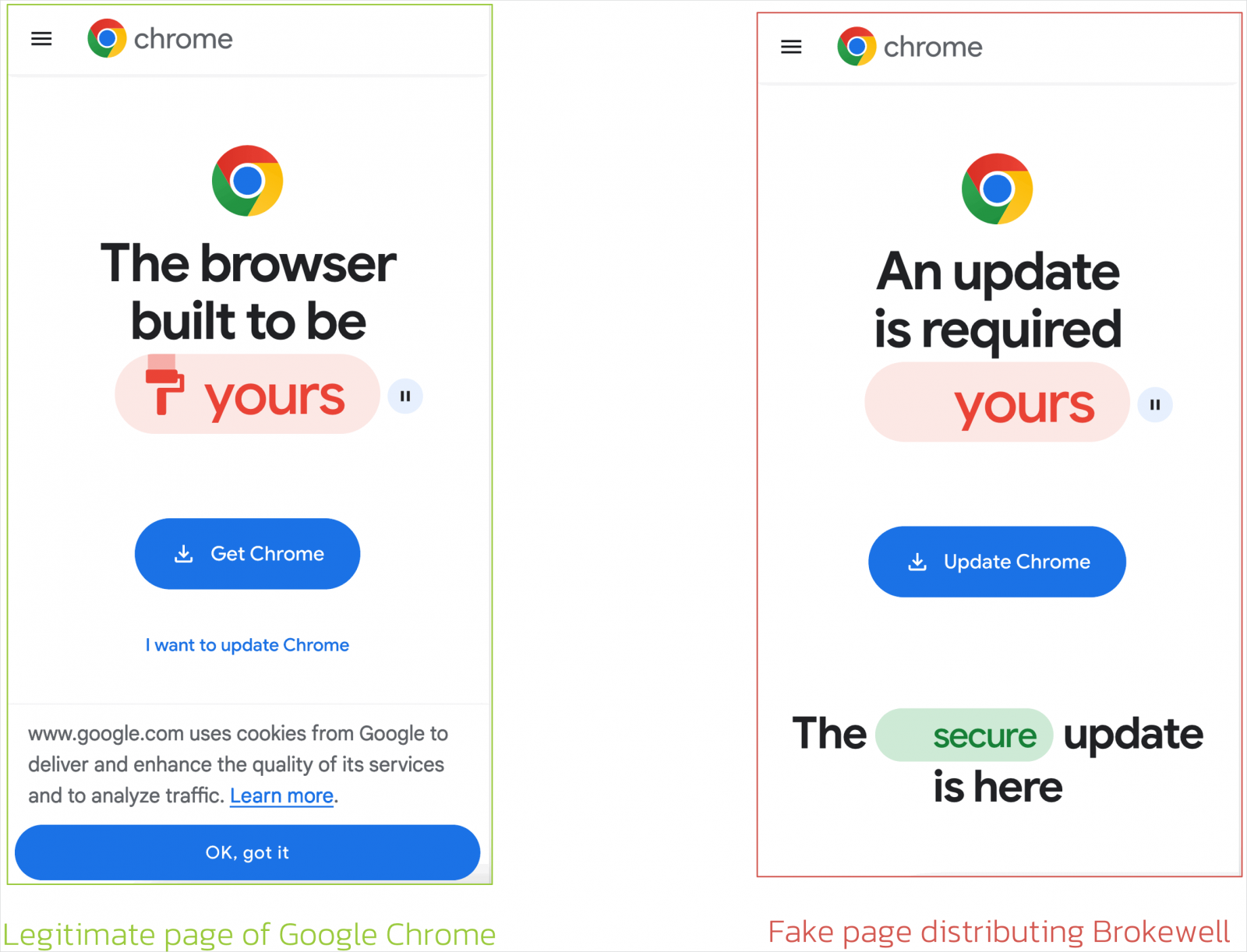
ThreatFabric
Taking a look at previous campaigns, the researchers discovered that Brokewell had been used earlier than to focus on “buy now, pay later” monetary providers (e.g. Klarna) and masquarading as an Austrian digital authentication software referred to as ID Austria.
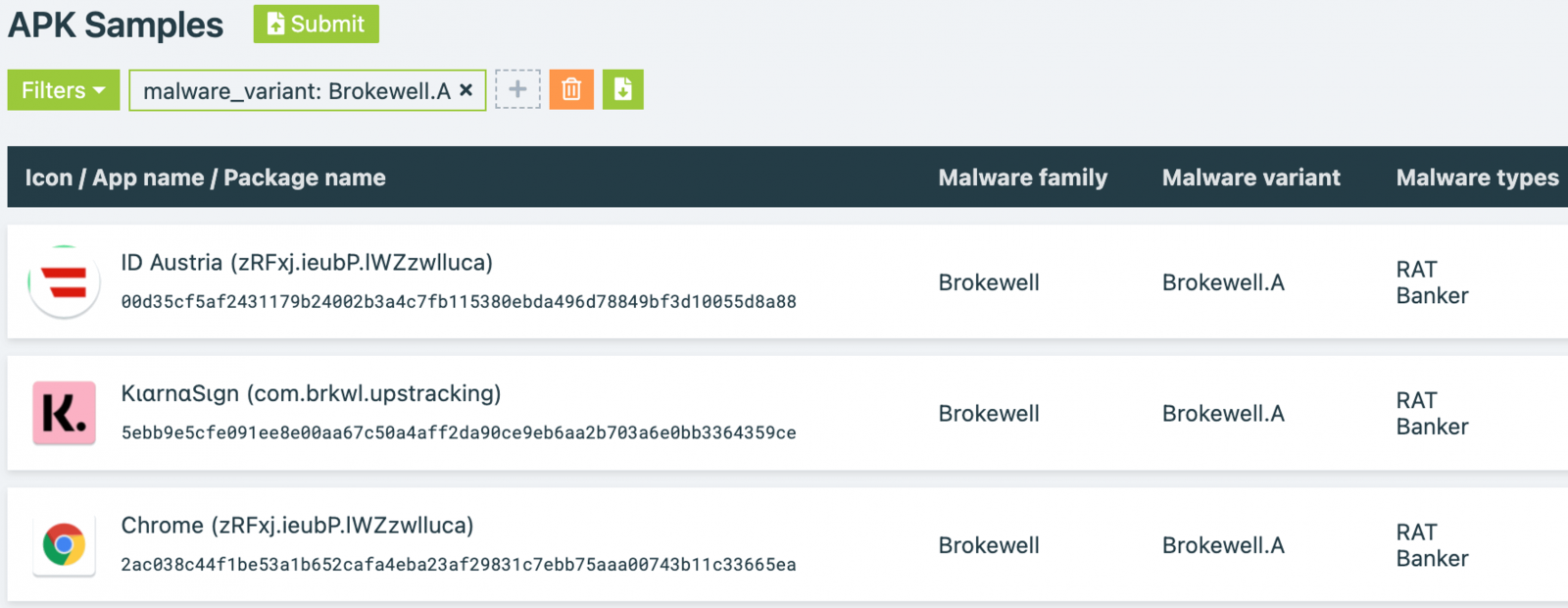
ThreatFabric
Brokewell’s most important capabilities are to steal knowledge and supply distant management to attackers.
Information stealing:
- Mimics the login screens of focused purposes to steal credentials (overlay assaults).
- Makes use of its personal WebView to intercept and extract cookies after a consumer logs right into a authentic website.
- Captures the sufferer’s interplay with the machine, together with faucets, swipes, and textual content inputs, to steal delicate knowledge displayed or entered on the machine.
- Gathers {hardware} and software program particulars concerning the machine.
- Retrieves the decision logs.
- Determines the bodily location of the machine.
- Captures audio utilizing the machine’s microphone.
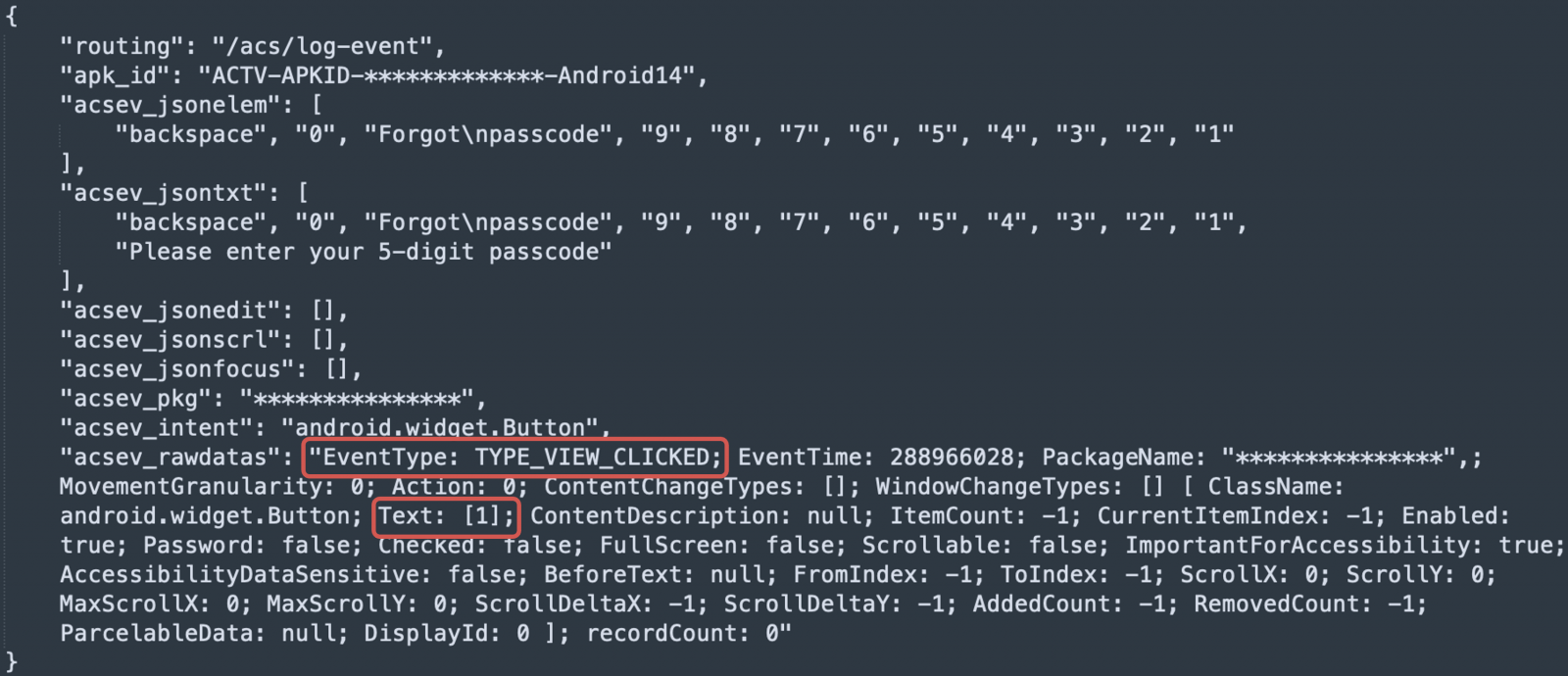
ThreatFabric
Gadget takeover:
- Permits the attacker to see the machine’s display in real-time (display streaming).
- Executes contact and swipe gestures remotely on the contaminated machine.
- Permits distant clicking on specified display parts or coordinates.
- Permits distant scrolling inside parts and typing textual content into specified fields.
- Simulates bodily button presses like Again, House, and Recents.
- Prompts the machine’s display remotely to make any data out there for seize.
- Adjusts settings like brightness and quantity all the best way all the way down to zero.
New menace actor and loader
ThreatFabric stories that the developer behind Brokewell is a person calling themselves Baron Samedit, who for not less than two years had been promoting instruments for checking stolen accounts.
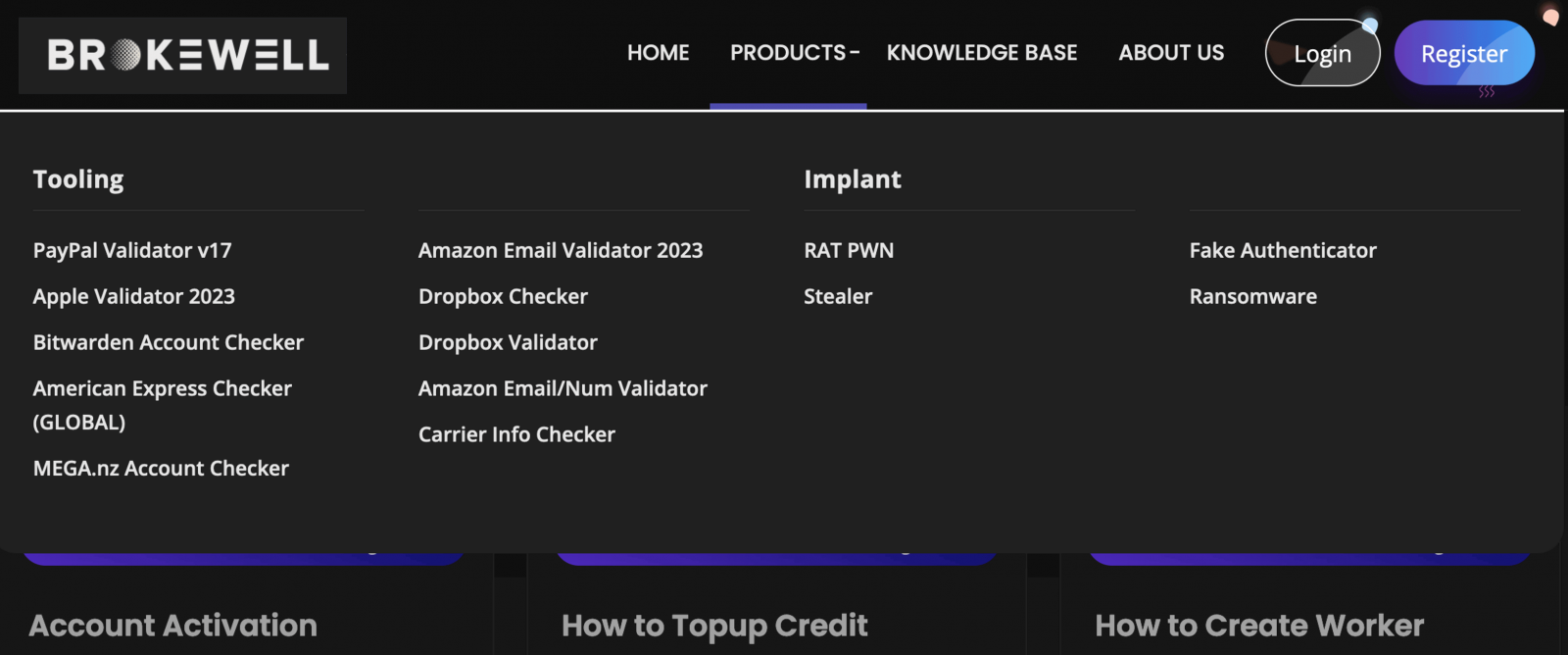
ThreatFabric
The researchers found one other software referred to as “Brokewell Android Loader,” additionally developed by Samedit. The software was hosted on one of many servers performing as command and management server for Brokewell and it’s utilized by a number of cybercriminals.
Apparently, this loader can bypass the restrictions Google launched in Android 13 and later to forestall abuse of Accessibility Service for side-loaded apps (APKs).
This bypass has been a difficulty since mid-2022 and have become an even bigger drawback in late 2023 with the provision of dropper-as-a-service (DaaS) operations providing it as a part of their service, in addition to malware incorporating the strategies into their customized loaders.
As highlighted with Brokewell, loaders that bypass restrictions to forestall granting Accessibility Service entry to APKs downloaded from shady sources have now develop into widespread and broadly deployed within the wild.
Safety researchers warn that machine takeover capabilities similar to these avaialble within the Brokewell banker for Android are in excessive demand amongst cybercriminals as a result of it permits them to carry out the fraud from the sufferer’s machine, thus evading fraud analysis and detection instruments.
They anticipate Brokewell to be additional developed and supplied to different cybercriminals on underground boards as a part of a malware-as-a-service (MaaS) operation.
To guard your self from Android malware infections, keep away from downloading apps or app updates from exterior Google Play and be sure that Play Shield is energetic in your machine always.
.jpg)