A brand new model of the BiBi Wiper malware is now deleting the disk partition desk to make knowledge restoration more durable, extending the downtime for focused victims.
BiBi Wiper assaults on Israel and Albania are linked to a suspected Iranian hacking group named ‘Void Manticore’ (Storm-842), which is believed to be affiliated with Iran’s Ministry of Intelligence and Safety (MOIS).
BiBi Wiper was first noticed by Safety Joes in October 2023, with its actions prompting an alert from Israel’s CERT in November 2023 about large-scale offensive cyber operations utilizing it in opposition to essential organizations within the nation.
A brand new report from Verify Level Analysis uncovers newer variants of the BiBi wiper and two different customized wipers utilized by the identical menace group, specifically Cl Wiper and Partition Wiper.
The report additionally highlights operational overlaps between Void Manticore and ‘Scarred Manticore,’ one other Iranian menace group, suggesting cooperation between the 2.
Pretend personas and cooperative assaults
CheckPoint suspects Void Manticore hides behind the ‘Karma’ hacktivism group on Telegram, which appeared following the Hamas assault on Israel in October.
Karma has claimed assaults in opposition to over 40 Israeli organizations, publishing stolen knowledge or proof of wiped drives on Telegram to amplify the injury of their operations.
A persona used for the Albanian assaults is known as ‘Homeland Justice,’ which leaked among the stolen information on Telegram.
This technique is similar to the method Sandworm (APT44) has adopted, who, in keeping with Mandiant, hides behind hacktivist-branded Telegram channels like XakNet Workforce, CyberArmyofRussia_Reborn, and Solntsepek.
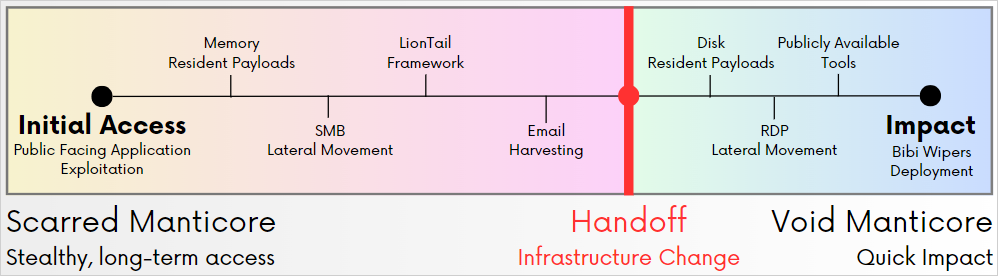
One other fascinating discovering is that Void Manticore seems to have handed over management of compromised infrastructure by Scarred Manticore in some situations.
Scarred Manticore focuses on establishing preliminary entry, primarily by leveraging the Microsoft Sharepoint CVE-2019-0604 flaw, performing SMB lateral motion, and harvesting emails.
The compromised organizations are then handed off to Void Manticore, which conducts the payload injection levels, lateral motion on the community, and the deployment of the information wipers.
Supply: Verify Level
Void Manticore instruments
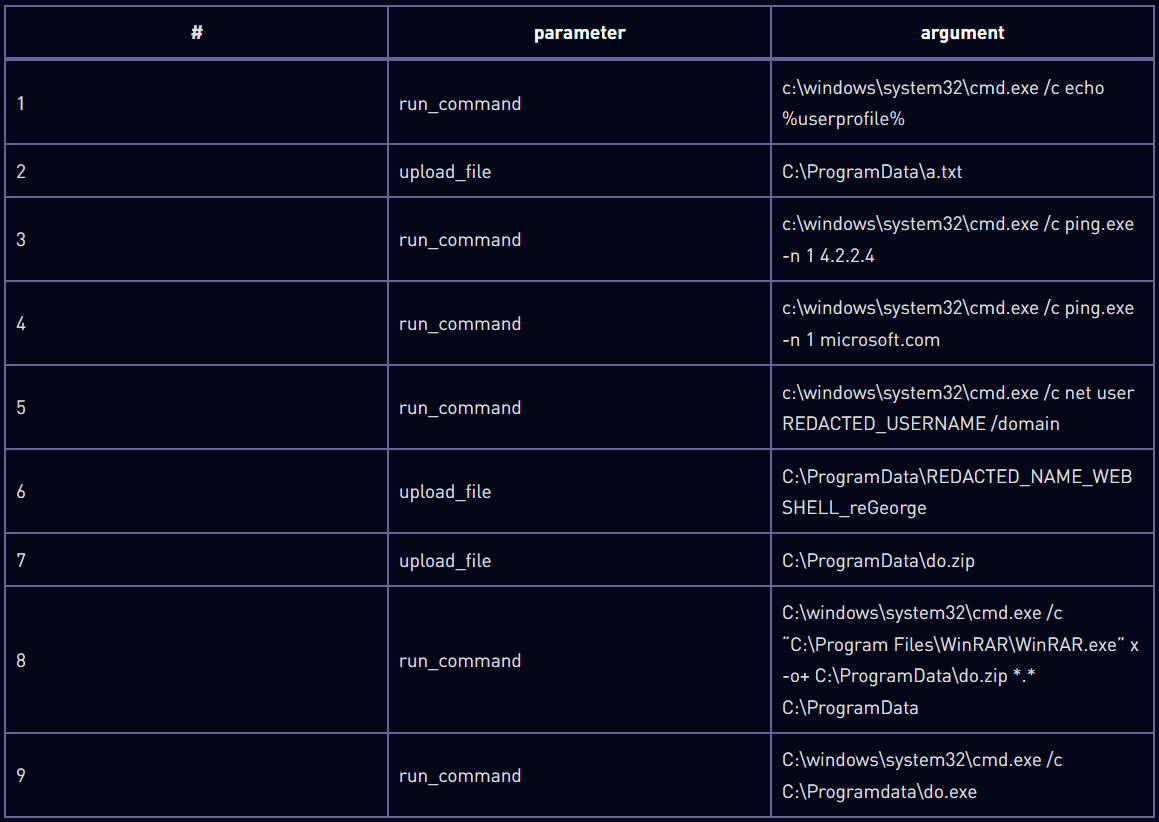
Void Manticore makes use of numerous instruments to hold out its harmful operations, together with net shells, handbook deletion instruments, customized wipers, and credential verification instruments.
Karma Shell is the primary payload to be deployed on a compromised net server, which is a customized net shell disguised as an error web page that may checklist directories, create processes, add information, and handle providers.
Supply: Verify Level
The newer variations of the BiBi Wiper seen by Verify Level corrupt non-system information with random knowledge and append a randomly generated extension containing the “BiBi” string.
BiBi has each a Linux and a Home windows variant, with some distinctive traits and minor operational variations reserved for every.
For instance, on Linux, BiBi will spawn a number of threads primarily based on the variety of obtainable CPU cores to hurry up the wiping course of. On Home windows, BiBi will skip .sys, .exe, and .dll information to keep away from rendering the system unbootable.
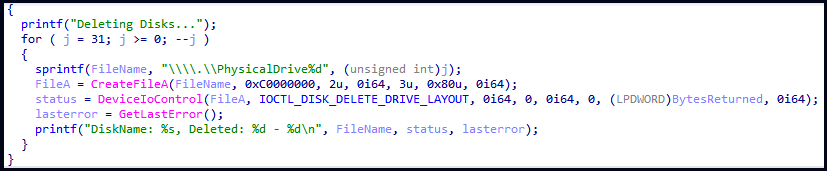
In comparison with previous malware variations, the newer variants are configured solely to focus on Israeli programs and don’t delete shadow copies or disable the system’s Error Restoration display screen. Nevertheless, they now take away partition data from the disk, making it harder to get well knowledge.
Supply: Verify Level
The CI Wiper, first seen in assaults in opposition to Albanian programs, employs the ‘ElRawDisk’ driver to carry out wiping operations, overwriting bodily drive contents with a predefined buffer.
Partition Wipers particularly goal the system’s partition desk, so the disk format can’t be recovered, complicating the information restoration efforts and maximizing the injury completed.
Assaults from these wipers typically lead to victims getting a blue display screen of loss of life (BSOD) or system crashes upon reboot, as they have an effect on each the Grasp Boot Document (MBR) and GUID Partition Desk (GPT) partitions.
